This very informative talk given at Shmoocon 2011 has been posted over at IronGeek. Covering all kinds of angles that a person could attack someones computer through the USB port, this should be read by anyone who is security minded at all. No matter which side of the port you tend to be on, this article has great information. They cover some common attack methods such as keyloggers and fake keyboards as well as some common methods of securing your system against them. We’ve actually seen this in the news a bit lately as people have been using the keyboard emulation method in conjunction with android phones to hack into systems.
[thanks Adrian]

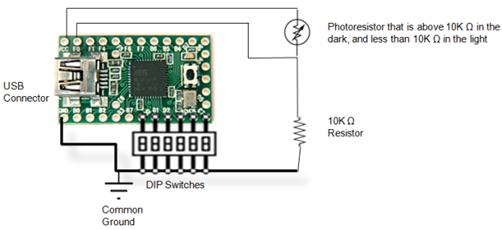














Wasn’t this at Shmoocon 2010? Also, relies on mostly the same technics as it uses the teensy boards and emulates keyboards (or other HID for that matter)
http://www.irongeek.com/i.php?page=security/programmable-hid-usb-keystroke-dongle that’s what i meant.
This was one of my ideas I had years ago and never acted on :(
You could also put a keylogger right into a keyboard, and so it doesn’t need to be recoverable, have it detect a period of inactivity, and use that ‘alone’ time to send its log off.
If someone has physical access to your machine then it’s game over anyway. Why bother going to all the trouble of using a phone to emulate different devices and send a sequence of keystrokes that may or may not be the right ones to achieve something? There is already a keyboard, and I’m sure the person is fully capable of pressing keys.
kemp:
In a lot of cases there won’t be a keyboard.
So what we’re relying on here is a supposedly secure system, with no input devices, in a room by itself (preventing you from pulling a keyboard from another machine), to which random strangers are given physical access and which is left permanently logged into an account with admin privileges? (Random strangers because a disgruntled employee will just take a keyboard from another room easily enough, and logged in because no where in this “hack” is there a way to magically bypass security.) No offense, but this is gradually sounding more unlikely.
Why hasn’t there been anything about USBs DMA-access that could be used to read a PCs RAM-contents directly without ever installing a driver on the host?
To everyone out there, do not use keyloggers besides for home use. I can almost guarantee that you will be caught. I recently got caught and seriously regret it. So to all students and everyone else in the workforce. Dont mess up as I did.
Metali,
I’ve had a keylogger on my girlfriend’s computer for 4 years now. Never got close to being caught. You must have been terribly obvious.
@ota benga
You and metali have some serious problems….
@benga
Wow…that’s just really sad on a whole lot of levels…
My wife and I are currently enrolled in a Computer Network and Database Security curriculum, and even though the instructors haven’t covered USB-based attacks yet, the students are all very intelligent, curious individuals, and read about this stuff. We are the soon-to-be professionals that will be looking for this stuff.
@Kemp – I can think of a few cases where malicious USB devices can be very effective. Having a USB drive commit a dictionary based attack while the user is distracted by some simple game, or porn-based entertainment, is just one. I new of an individual a couple years ago that bought some flash drives, installed some spyware/viruses and music on them, then dropped them off at the local mall food court.
@rallen71366
Even better to use el-cheepo MP3 players instead of thumbdrives.
As always, be aware of any device connected to your computer.
I was an Intelligence Analyst and I now work in the IT field. I can see several potential targets for USB device attacks that all have varying degrees of effectiveness and if used (im)properly can be very profitable for the attacker.
Some possibly obvious locations are:
shopping mall kiosks
libraries
Fed EX/Kinkos, UPS Stores, and the like
schools
financial institution kiosks and unmanned desks
internet cafes
tax preparation centers
retail stores that use WinCE to run their registers
@Metali I hope you’ve learned not to use this technoology improperly
@ota benga You have some SERIOUS trust issues. You’re spying on her and can actually be prosecuted and serve a prison sentence for that. If you’ve been together for that long, you’re not married then you and she might both need to move on. I encourage you to look into cases where a husband has gone to jail for spying on his wife and catching her having an affair on their family computer.
I once looked in my ex-wife’s email sent items (she had given me her password and asked me to check her inbox for me) and I found evidence that she was cheating. I went to her social networking site of choice and found further evidence (didn’t have to log in) and then I found pictures and videos on both a Micro SD card and on the hard drive of MY computer that confirmed my suspicions.
Even going into her sent items with a password she provided to me could have been considered a form of trespassing and I received some good advice NOT to declare that as a source of my information. Because of this, I filed for divorce citing irreconcilable differences, rather than adultery, so now I have to pay alimony.
My point is that even if you get the information you’re looking for when spying on others, you can’t use it to its fullest potential without consequences that outweigh the benefits.
@rallen71366 Do I know you? Did we take some classes together in Korea? If not, I’m sorry for the confusion. Anyway, that food court thing is devious. I applaud that individual’s creativity in deployment, even though I deplore the rest of that activity. While it may seem simple to some, most people who don’t know anything about computer security will simply pick up and take the thumb drives and take them home for personal use. This looks like a hardware adaptation of the Trojan based attacks. What could make that particularly evil is to use this method to turn these home computers into zombies and launch DDoS attacks from all these unsuspecting users’ locations. Oh, and if any of them are foolish enough to take a ‘found’ device to a work computer then they could be in even more trouble.
“Having a USB drive commit a dictionary based attack while the user is distracted by some simple game, or porn-based entertainment, is just one.”
It’s not the use of USB devices as an attack vector that I’m debating so much (I can see how that would work in several cases – taking advantage of auto-run is an example mentioned in the linked article – though Firewire is, of course, the more well-known option). What I’m debating is the use of a keyboard emulator like everyone has been raving about recently. If the user is present then they’re going to notice something trying to type on their system (windows popping up, things actually being typed, etc). If the user isn’t present then you must have got physical access yourself to install the device, so there’s no point using it.
Am I overlooking some basic element of the technique here?
@ Kemp
One example of how such a thing could be useful: While the machine is locked, such a device could be plugged in (say, after-hours by a ‘janitor’). The device can have a sound sensor that triggers a set of commands that would create a new user account in Active Directory when the room has been silent for 20..30..whatever… minutes.
This would assume/hope that the admin has walked out of the room, leaving their station unlocked (not as uncommon as you’d think, especially if this is a high level person with their own office, or the machine is behind a locked door of some sort).
Something else I’d consider having it do, is activate a key press (maybe scroll lock on/off) every 9 or 14 minutes, depending on their screen lock policy, this would allow it to sit for longer, as it waits for an extended period of silence before delivering.
Or heck, simply having the station remain forever unlocked could be helpful to the ‘janitor’ who will be in later that evening.
Of course locking their workstation when they get up would nullify this, but you and I both know that companies enforce group policies that force lockouts after inactivity because a lot of people DON’T windowkey+L when they stand up.
oh, and one more thought for payload; launch a web browser to some sort of remote assistance page (webex, goto my pc, etc…) to allow the attacker full access to the machine without even needing to go back.
lol: if you catch your spouse cheating – using YOUR computer, YOUR internet connection, then SHE is the one doing the trespassing. There’s other ways to work that, including using the “illegally” obtained evidence to find ways to legally obtain the information you need to get an adultery divorce, but sounds like that boat has sailed. Hell – in some states, you can sue the other guy. I understand it’s not common, but when it’s tried, it’s often successful if you live in New Mexico.
*shrug* I guess it depends on jurisdiction – so look up your state laws; but there are states (like New York) where it’s virtually impossible to get a divorce, and then there are states, like Missouri, where if you catch your spouse cheating, you can just about get away with assault. No matter how happy you are in your relationship, it’s ALWAYS a good idea to consult a lawyer BEFORE you get married. BEFORE you even start digging around (if you’re already married). BEFORE you confront a suspected miscreant. Always a good idea to have a pre-nup – I have told my kids they don’t get my “blessing” to marry unless they have a pre-nup.
Alimony – wow, in the 21st century. That’s just f–king extortion.
Thanks for the explanation, that makes more sense. It still seems to be of incredibly limited scope, but at least now I can see a real usage scenario.
Kemp, why not even do something like embed a micro USB hub into the dongle, and inside this dongle you have this piggy back keylogger/keyboard emulator along side two storage units the one storage unit is used to store dummy files and the second storage unit is essentially write protected to the user but the keylogger/keyboard emulator can read write to this storage device, also it can be used as a way to covertly store a package for deployment of some kind.
The possibilities are endless. Where I live its illegal to record video/voice of someone without their consent for legal/commercial reasons but transcriptions of said audio are legal for use. Just an abstract comparison but I’m sure this information is enough to help even by feeding this gathered information to a P.I. or something along those lines.
Oh finally a write-up on this – I created a virtual Keyboard on my GP32 about a year or so after they were released – WalMart kiosk computers often implicitly trust the keyboard – then when SparkFun started shiping the AVRStick this is actually the first thing I got it for – my POC did a [Win]+R and typed debug – and then typed out the TinyPE executable for downloading and executing a payload, there was just enough flash in the ATtiny85 to pull it off.
I had a more innocuous version that would [Win]+R – notepad.exe and then typed out the hacker manifesto for a laugh – I wrapped it in a plastic shell from a thumb drive and left it in the office for fellow hacker geeks to get that “oh crap” feeling in their guts ;)
I always love people like Kemp that have absolutely no imagination.