Concerns over privacy online are an ever growing theme. Every day we see people complaining about the policies of facebook and the like. [Mike Cardwell] points out another method of gleaning a bit of personal data from you that you may not have seen yet. By embedding a hidden image or using some really simple javascript, he can tell if you are currently logged into Gmail, Twitter, Facebook, or Digg. While this could possibly be used for more nefarious things, he points out that you could also use it for customizing your website to better suit the experience of the browser. For example, if the “reader” is already logged into Gmail, you could have any email links automatically open a gmail instance instead of the local mail client.















You know, I just had this idea earlier today. That’s awesome.
What isn’t awesome is that the link is dead. :(
Link is quite up.
@ALL,
this is a “soft opening” of our forums. Please be patient with us as we’re sure there will be issues.
After a very long time of people requesting it, here you go forums.hackaday.com
-caleb
30 seconds in, and I have to say “cool”. Here’s the first test, verbatim:
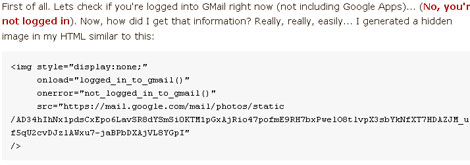
“…First of all. Lets check if you’re logged into GMail right now (not including Google Apps)… (Please enable JavaScript). Now, how did I get that information?…”
It’s a dangerous web out there everyone. Don’t surf without protection.
Browsing in ‘incognito’ mode (or w/e depending on browser) is a must do nowadays.
I’m logged into gmail and have javascript enabled but it says I’m not logged in. Perhaps because I’m using the mobile gmail interface.
@Caleb Kraft
Well, thats one way to kill further comments on an article.. just post a link to the new forum! :D
I’m assuming a new post will be made announcing the forum when its ready?
@bluewraith,
there will be a post about it. I just didn’t want to have EVERYONE go there only to have it crash and burn. I’d rather have a few people trickle in and find the issues slowly.
I expected more abuse and less…. status codes.
They can see if I’m logged in to a social networking site, OH NO!
The real issue is if you can use the JS to pull down the whole page and then regex query for a username/email/real name/address/ip address, then you should worry.
@Standard Mischief: same here. Surfing without NoScript is liking driving without seat belts.
A neat trick, but I am really straining to see how this is a serious concern for anyone.
His example at the top about being able to tell if you are logged into a porn site is really stretching it, since you need to adapt this trick to each and every site individually. Unless somebody is willing to go through and find URLs to check for every online service/forum in existence, there isn’t a whole lot to be worried about.
scenario…?
Check if the user is using gmail. open a popup with hidden JS (key tracking) and an iframe to log the user out of gmail. If the user then logs back in would it be possible for the hidden js to track keyboard input for that window?
Sorry, haven’t programmed JS/web in a while so not sure if it would work? any thoughts?
Who cares? CSRF like this has been around for AGES, and well known too. If I am not mistaken, gmail has had this “issue” for a long while, and was even pointed out here.
You think this is a big deal? Take a look at getComputedStyle() in javascript. Set visited links and unvisited links to some static values; you can see quickly where this is going. You will be able to retrieve whether or not the user has visited an arbitrary url.
This is nothing new.
In chrome it tells me I’m logged into Twitter when I’ve never actually been to Twitter in recent memory. It does tell me I am logged into FB when I am though.
In FF it tells me I’m not logged into Twitter and just says “Checking” for facebook, even though I am logged in there.
Don’t really see the value of this, but it’s an interesting read.
noscript.
“First of all. Lets check if you’re logged into GMail right now (not including Google Apps)… (Please enable JavaScript). Now, how did I get that information? Really, really, easily… I generated a hidden image in my HTML similar to this:”
I don’t think he knows what I’m logged into. Not much of a hack. Nor a new one.
counterpoint: noscript.net
This trick *could* be used to detect if someone is a mod or admin on a given site (thus when they visit the page they see different content). That could result in delayed moderation of malicious links because the mods wouldn’t be able to verify that the link is malicious.
Or it could be used to target/harass certain users or groups of users who can be uniquely identified by whether or not an image/page can be loaded.
Or it could be used to trick people into thinking that a malicious page is associated with a site they already have a “trusted” relationship with.
http://whattheinternetknowsaboutyou.com/
Using “a:visited” CSS tag the website scans your history for popular sites.
To people asking what is the point? The point is ££££££ / $$$$$$$$
If the bad guys (advertising company) knows which sites you visit and how often, he can target adverts to you. this means more money in the bank to him.
Maybe knowing which email provider you use does not give him much ammunition, but knowing what types of forum you visit regularly will do.
As mentioned above, using hidden hyperlinks on a page and then checking if their colour turns to “visited” is already been used to track peoples internet habbits for a while.
The internet is turning into a pretty f*cked up place to hang out…
Only if Javascript is on.
Oh wait, scriptblock wont let his trick work.
IT’s just an example on how modern browser scripting is broken and needs to be fixed.
I hoped everyone is using one browser for the casual websites and the other (one window or tab at the time) for the “risky” and “interesting” side of the web.
Surfing without script, history and cache control is asking for trouble.
Most of the suggested abusive uses people are coming up with here seem to be completely ignorant of existing blocks on cross-domain access.
Site X cannot load up a Gmail page and parse it for information because it’s in a different domain. Likewise, Site X can’t open up a popup to Gmail’s login screen with keylogging enabled because it’s a different domain.
The closest you can get to accessing information from an external domain through Javascript alone is this method, or by checking the rendered colour of external links to see if they’ve been visited, and even that’s probably been removed now.
CSFire protects you from these kinds of attacks on Firefox. I highly recommend it, though you do have to occassionally turn it off to make some sites work (or you can configure it to work with sites you use often, if it creates problems with them). Check it out: https://addons.mozilla.org/af/firefox/addon/csfire/?src=oftenusedwith
I blog about it here: http://albosure.blogspot.com/2010/04/plugging-privacy-leaks-with-csfire.html
I’ve seen this in the wild already for Twitter and Facebook.
Gotta love noscript on this one ~