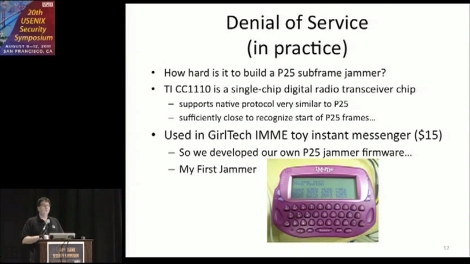
Would you believe you can track, and even jam law enforcement radio communications using a pretty pink pager? It turns out the digital radios using the APCO-25 protocol can be jammed using the IM-ME hardware. We’ve seen this ‘toy’ so many times… yet it keeps on surprising us. Or rather, [Travis Goodspeed’s] ability to do amazing stuff with the hardware is what makes us perk up.
Details about this were presented in a paper at the USENIX conference a few weeks ago. Join us after the break where we’ve embedded the thirty-minute talk. There’s a lot of interesting stuff in there. The IM-ME can be used to decode the metadata that starts each radio communication. That means you can track who is talking to whom. But for us the most interesting part was starting at about 15:30 when the presenter, [Matt Blaze], talked about directed jamming that can be used to alter law enforcement behavior. A jammer can be set to only jam encrypted communications. This may prompt an officer to switch off encryption, allowing the attackers to listen in on everything being said to or from that radio.
[youtube=http://www.youtube.com/watch?v=NW-jRRTPCuw&w=470]
[Thanks DanAdamKOF and Uhrheber]















This is quite interesting.
What a nice project.
maybe im just confused but three hours since posted and NO comments???
DID THE YAHOO CENSORSHIP GOONS GET INTO THIS SITE???
srsly i heard those radios were “unbreakable” even to expert coders… A KIDS TOY ??? wow.
The encryption may be unbreakable, but if the only way to use the radio is to turn off encryption then in a way its broken.
hmm my “1st” comment got beat by 4 mins, sry HAD staff. please remove my last comment.
what i wanted to say:
seriously, i heard those radios were “unbreakable” even to expert coders… A KIDS TOY ??? wow.
I can ‘break’ a Rubik’s cube with a hammer. It doesn’t mean I figured out how to solve the puzzle.
Application has use, figuring it out dose not.
law enforcemnet? Spelling error in the title…
Cool project btw!
These radios are “unbreakable” in the sense they haven’t been broken yet. Any radio system is susceptible to jamming.
The Titanic was “unsinkable”. Arrogant humans.
@tony, The Titanic was monikered “Unsinkable” by the media and myth. Arrogant posters…
They have been broken in Australia. https://www.dailytelegraph.com.au/hi-tech-hackers-crack-nsw-police-force-22-million-encrypted-radio-system/news-story/c4dd519b7edd72918212ca380ecfaded?sv=907f29a6cbe309c1bc439b303b733241 and yes it was a P25 system.
So does this mean that GirlTech will now be a defence contractor? (I can hardly wait for the pink rifle!)
http://blog.riflegear.com/archive/2007/12/26/hello-kitty-ar-15—evil-black-rifle-meets-cute-and.aspx
Too late!
http://www.riflegear.com/blogimages/HelloKittyParts.jpg
does that come in betty boop
If you want to listen to unencrypted P25, I highly recommend the PSR-500 by GRECOM. I got it from scannermaster – it is awesome!
“It’s going to be someone somewhere creating the Project 25 jamming kit and it’ll be something that you download from the Net,” Blaze said. “We’re not there right now, but we’re pretty close.”
i’ll be looking for HAD to cover it when it comes out
Wonder if anyone did any analysis of Tetra.
http://tetra.osmocom.org/trac/
P25 was never designed to be jam-proof. There are some radio systems with anti-jamming techniques built-in, but mostly in military systems where jamming is a real threat.
Google HAVE QUICK II , STANAG 4372 or AN/PSC-11.
Now THIS is hacking!
I myself have researched this radio standard for a few years now. I have found many more vulnerabilities than these guys have mentioned.
I won’t share them for the sake of it falling into the wrong hands, but I can say that it’s enough to make me a little queasy.
Not only are there problems with the security, the price is another factor. Many law enforcement agencies have to buy this equipment in order to keep up with surrounding areas. The vocoder itself is very expensive and has a hefty royalty fee.
I have taken it upon myself to address these issues and turn speex into a new digital radio system standard. And Ham’s should at least benefit from the lower cost of my work.
@John
Speex is a little ‘heavy’ for HAM/NFM work, checkout CODEC2.
http://www.rowetel.com/blog/?page_id=452
What a lovely bit of Black-Hat hacking :P Of course, the officers could always switch to cell phones, which are spread spectrum and therefore harder to jam.
Civilians are supposed to be able to listen to police broadcasts…encrypting their communications is wrong. I love that you can use a toy designed for little girls to do this.
I wonder if the TI watch I have on the way could do the same?
While I agree that official communications should be recorded and subject to review for accountability’s sake, I disagree that they should always be unencrypted. For example, consider a hostage situation in which law enforcement must coordinate without the knowledge of the hostage-takers or other parties in order to take them by surprise. There are times when encrypted communication is necessary for the effective execution of their jobs.
Too bad police dont have magical devices called “cellphones” that already do this.
Oh wait, this is what they do already.
Police comms should be encrypted to protect the operation and personal details…. however it should also be made available after the fact with any redactions explained.
The police are public servants and should be accountable for their actions.
There are some communications so private that they should never be made public. An example might be the name of a rape victim or an abused minor.
There are some communications that need a delay, but only a short delay. Perhaps the oddball hostage situation.
For the overwhelming majority of police radio communication, they need to be transmitted live and in the clear. I can’t tell you the number of times I’ve found out exactly why a helicopter had been circulating the area or what the huge firetruck response was all about. After an accidental chemical release or a terrorist attack I’ve found out exactly what was going on thanks to my scanner. The media has been less than helpful because usually only get a strange diluted version of what happened, after a delay, on the five o’clock news.
Unfortunately this is exactly the reverse of what is happening. Puppycide and SWAT teams and garbage trucks bought with homeland defense pork spending. Super-seekret cross-state radio networks that encrypt even the mutual aid frequencies. Getting the recycling collectors and the dog catcher both on scrambled trunked radio systems. I can’t see any of this crap ending well.
This has received a lot of unwarranted publicity from the chicken little gallery. It’s also what happens when you have “IT” weenies with ZERO real world radio background focusing in on something to make themselves look credible in their industry (IT security).
As someone on another message board suggested, I could write big headlines to the effect of “$.10 cent Home Depot part renders top secret national security million dollar device inoperable!!”…what might this be ? hey, i’ll just drop a screw onto a live circuit board inside say a control panel for an F-22 CDU.
Some of you need to stop “skimming” articles and repeating the hype generated by a rag of CNET’s caliber.
To Old Crows in the defense industry, and others in the radio business, this is no news. Heck there are literally dozens of more PRACTICAL ways to disrupt communications. The time/effort needed to implement this kind of EXPERIMENT, would be tactically unsound in the REAL WORLD (particularly when less complicated vectors to achieve the same goal exist).
Also, you’ll notice the academic work focused on end users not selecting encryption-on. In other words they were transmitting un-coded messages. This is not a hardware issue, but a user issue of the feature being ignored.
All hype, little substance of practical value (to anyone but IT weenies wanting to push buttons of clueless management types and politicians – presumably to give the illusion of elevating their own ‘value add’ to the organization).
As I stated, dozens and dozens of more easier ways to disrupt a radio system.
Read the paper or watch the video, i agree that an army of criminals armed with girltech im-me jammers are not a real threat. but attack behind this using selective jamming of frame only needs 4db of power UNDER base station received power. Not to mention the ability of selective jam comms.
These are pretty clever attacks.
You sure are angry on the Internet about Information Technology!
@John P, keeping the knowledge back does far more damage because when the “bad guys” do figure it out they will probably use it to greater effect.
Better to publish what you know anonymously in a way that proves the system is fundamentally broken and let the authorities take appropriate action.
Remember, security through obscurity is no security at all!!
(Sony learned this the hard way, military grade security on the PSP and it could be defeated with a simple buffer overflow from the battery E2PROM)
from what i read, it wasnt a buffer overflow
it was a backdoor for recovering it from a bricked state
if the serial# is 0, it will boot off the memory stick
they simply left out any signed boot file checking on the backdoor
nothing to be wow about, single transistor can jam spectrum, gas lighter can jam, broken lightbulb can accomplish goal
Can any of those just jam communications between specified people? Not really the same are they.
Haven’t been broken yet? Um, with a $15 toy and a small power amp you can make encryption useless so they have to switch to clear mode.
I’d say that’s a fairly broken system.
@truthspew
There is a world of difference between knowingly talking on an unencrypted channel and talking on a channel you believe to be secure. The encryption itself hasn’t been broken/cracked. Having users mistakenly believe it is turned on when it isn’t is a Very Bad Thing(tm) but has nothing to do with the IMME attack. The attack is about two things, creating a positional knowledge of nearby radios and selectively jamming only the encrypted traffic so that users are forced to go unencrypted (though they should know this and therefore watch what they say a bit more). Both are very bad.
@JohnConnor
I don’t think you understood the attack. By sniffing the start of the packet, you can determine not only if it is encrypted, but which radio is sending it. So no, it is not a spectrum jam, but a highly targeted and specific jam. Like if you followed someone around in a crowd and only dropped banana peels in front of that specific person or waited to hear the first word of their sentence and if it started with a vowel then you would cough really loudly to drown out the rest.
It sounds like this could be adapted to knock out or even replace specific radio IDs so that a legit user could be completely silenced or impersonated. THAT sounds like a scary scenario!
Are any of you noobs even comprehending the hype in that dubious IT resume padding article ?
Encryption was NOT broken or “hacked”, in any way, shape or form ! The radio user did not switch encryption “on”. LUSER error. It can be configured out by the way, just program the talkgroup as “secure” only”.
Besides, that $15 “toy” was hacked with custom firmware and an add on power amplifier. If I was an adversary, why the hell would I even bother with such troublesome and lengthy procedures when I can just buy a radio off e-bay, and jam the damn control channels at the tower sites ? You’ll really take down the system in that way. Repeat for each site for a wide area (multi-zone) system.
Get off your “IT” weenie-geek momma’s basements, and enter the real world of terrorists using simple but cheap AK-47’s, or gas bombs with a match and a fuse… (NOT complex Arduino controlled timing mechanisms!)… sheesh…
Wow, two comments full of the same drivel! You are real mad about Information Technology! Did a sysadmin break your heart, perhaps?
You might not understand this, but maybe hobbyists don’t want to “enter the real world of terrorists”.
Do you understand the term “proof of concept”?
You need to learn how to communicate with civility. I’m certain you have many wonderful things to say, but if you keep saying them in this manner, I fear that you will be banned, and then nobody will be able to learn from your wisdom.
Please take a step back from the situation and re-evaluate your attitude, as it is hurtful to the free exchange of ideas.
Thank you.
Law enforcement grade? You mean commercial grade with encryption as they dont make “law enforcement grade”
Motorola and others make commercial radios.
@truthspew.
you don’t know what the hell you’re talking about.
jam a channel and they can still use it in “clear” mode ? what universe do you live in where the laws of physics as we know them, don’t apply ?
you jam spectrum (unless you’re running anti-jam milspec waveforms), the spectrum usage is negated for both coded and clear messaging.
kind of like saying. dump oil on the highway, it’ll prevent Fords from driving, but Chevy’s can still operate.
And here’s proof that JohnConnor didn’t even bother to read the paper/watch the video.
A simple spectrum jam is easy to detect (radio not working), and with a single or unsynchronised jammers it’s easy to get the locations of the sources.
This attack allows jamming only specific parts of the transmission for example herding the users to turn off crypto.
very nice.
Does anyone know if something similar could be done to the European version? (TETRA)
Any change to upload new firmware to the IM-ME (spectrum analyzer) without using GoodFET ?
Bus Pirate, ez430 dev kit? any other?
Thank you.
@Will
Please describe to me the effort/reward ratio of the scenario you present.
There are simpler ways to execute the radio ID spoofing you describe. The least of which is to clone a legit radio and put it on the system (remember the old AMPS days of cellular cloning?).
Newer generation of core software these P25 systems are running (at least with one manufacturer), will be deploying dynamic radio authentication similar to what cellular phones do before being allowed access to the network. This is specific to that one vendor, and is permitted in the P25 specs as a “value added feature”.
This is nothing but a tempest in a teapot. It has zero practical value for any adversary.
Simple tactics are the most effective (a lesson the insurgents in the middle east have taken to heart).
JohnConnor, I believe the P25 authentication you mention only works in trunked systems. I don’t think it prevents any of these attacks.
Really, I don’t think you understand the work that you’re criticizing.
Their paper is online. It is available at this link: http://www.crypto.com/blog/p25 You might want to read it.
I’m curious: why are you so angry about this?
I think a lot of people become angry on the internet when they see something they recognize. For JohnConnor, it’s perhaps trivial to “clone a legit radio,” but for me and people on this website it’s easier to combine an RF poweramp with a kid’s toy. For us that IS the most elegant solution.
Especially if our goal is learning more about the system and not just destroying it, as JohnConnor seems to be expert at. I think JohnConnor is pissed that us younger, more open-minded folks are not taken part in his Man-dance. He probably sees all of our activities as non-productive, materialistic ventures into stupid oblivion, but the world is more fluid now than it used to be and sometimes a random little project like this can stimulate one of us to do valuable, useful things.
I like people like superlopez, who post useful links to the topic.
You sound mad, you work for Motorola?
@JohnConnor
Wow, if you want to start a flame war, you should pick a less knowledgeable opponent or at least read up on the topic you’re debating… I have no love for “IT” types but I have even less love for anyone who has “manager” or related in their title. At least IT folks do real work… I myself am neither and never will be, I am a firmware engineer who started out in board level EE and mechE design, cut my teeth on software and has racked up a nice portfolio of high level software projects in C, Java, C#, etc. My current job is all about embedded RF chips just like the CC1110. But I digress.
The attack vector as described in the video details using a $15 piece of equipment coupled with a piece of software allowing an attacker to:
1) completely jam all P25 traffic
2) selectively jam specific types of traffic (encrypted or unencrypted)
3) locate, identify and monitor specific radios within range (using a second triangulation source)
4) potentially impersonate (clone) a specific radio while at the same time knocking transmissions from said radio off the air.
Any of the above is pretty darn scary considering what these radios are supposed to be used for. It is even scarier considering that any of this could be done for less than $1000. Does that mean that every BadPerson(tm) will pick this specific method to cause trouble? No. But then again it’s not your average Joe who has access to anthrax or a nuke either and we still worry about those.
The thing about security is that you have to consider ALL risks and then weigh them based on probability of occurrence. This is why buffer overflows in software are a big deal. Sure they are unlikely and hard to find and a real pain in the a**. But if you were in any company I’ve worked at and decided to ignore them you’d be out the door or demoted to cleaning toilets so fast it would make your head spin. This particular attack looks to be pretty easy, very low cost, high availability and extremely disruptive. So yeah, it is a big deal unless it can be disproven based on technical arguments which you have yet to coherently voice.
Not sure how ethical this is, but cool nonetheless!
Those interested in inner working of P25 and/or owners of old analog scanners will find this very useful
http://wiki.radioreference.com/index.php/Digital_Speech_Decoder_(software_package)
@rasz.
No, I work for a large defense systems integrator and Motorola is a partner on some of our ventures.
The IT weenies muscled their way onto “turf” that used to belong to RF guys. Because of the presence of servers, management thinks “oh IT”… to which we say BS!
@Al, you’re proving my point. “IT” people just don’t get RF (radio). If you’re speaking of “conventional” operation, there are even more simpler ways of spoofing.
Come on, what next ? A paper on man-in-the-middle attacks on a microwave back haul ? or what about the publicity hounds on ATM “hacking” ? (and I don’t mean Asynchronous TM)… easy money, no ? well we don’t hear much about such high tech “hacks” – more low tech – dude drags the ATM away with a pick up truck!
As stated earlier ‘tempest-in-a-teapot’. Nothing but academic toilet paper. We’ve all written them in our college days.
So, these people not only walked all over your turf, but they also had the nerve to discover problems that your way of looking at things didn’t regard as being problems?
Yeah, I’d be pissed off too.
+1 Al
And for the record, JohnConnor, some of us that do IT stuff are also pretty well versed in EE.
So don’t generalize just because you don’t like your coworkers.
Furthermore, as a proof of concept, I think this is interesting. Hacks like this are a first step toward defeating the encryption entirely. I think you’d agree that would be a problem.
HAD: I’d love to see more RF stuff. Every real radio post I’ve seen has been interesting.
The interesting part of this is that they have cracked the P25 protocol.
It could be interesting news for HAM radio operators. I live on the other side of the globe and we have P25 repeaters and people do own motorolas that do it.
It would be sweet to send P25 compatible txt messages to people who own compatible radios.
The problem with IT geeks (even if they might have EE), is, they seem to be preoccupied with minutaie regarding the practicality of concepts.
When I was an engineering manager for another firm, i’d constantly have to “reel” in overzealous software people who would want to expend resources on designing out scenarios that were statistically improbable, and would have prevented a timely product release.
For example, one guy wanted to “seizure proof” a device so epileptics would be able to use it. My response was ‘hey, we don’t have to be ADA compliant!’.
If I were the prof’s adjudicating a grade for this paper, i’d evaluate it for what it is. A mediocre PR stunt. Now, if you’ll excuse me, I’m going to go “hack” the ATM down the street (could use some extra cash). Oh wait, it’s easier to phone in a fake 911 call on the other side of town, crash a pickup truck thru the front door, and haul off the ATM to my garage. Screw all that “hacking” of crypto algorithims and spoofing magnetic strips, blah, blah, blah. Ah yes, that pesky concept of “REAL WORLD” adversaries is intruding.
Wow… Your pride must be incredibly hurt for you to harbor such anger towards “IT geeks”, the fact that a $15 toy and some “IT geeks” are able to circumvent security that had billions of dollars in R&D thrown into it says a lot about the way you “manage” your software engineers. Maybe instead of being so closed minded and telling them to stop “wasting time” trying to make the end product better, you let them do their jobs and you wouldn’t be in this position… But just like every other clueless manager out there, you think your way is the only way and that everyone who works for you knows nothing, newsflash my friend, most of those “overzealous software people” you’re putting down are MUCH smarter than you are, and most of the people you’re putting down on this very website are as well… So please, take your condescending attitude and ignorance out of here, we don’t need douchebags like you here, you’re absolutely useless.
So, you don’t think “minutaie” are relevant to the practice of security and cryptography, to say nothing of engineering in general? That’s certainly an interesting point of view.
Don’t tell that idiot anything. If he isn’t smart enough to know that many people may have epilepsy and not know it( the reason his programmers wanted to proof it), then he doesn’t deserve his positon. I may not have an ee or a mba, but I atleast know that it’s best to research every senario in this liability-sueing world. Btw, how does someone to down to hacking but suggestd using social engineering in the same breath?
*talk down about*
is there a guide on how to do this?
Just as an FYI… Even if you do figure out how to do this with the IM-ME toy you will not be able to hear any traffic over the toy just make the Apco-P25 user switch-off thier encryption so you can listen on your pre-existing scanner. But I asuume most of you got that already.
Speaking of legacy toys (now discontinued): Check out the Ohio Arts Zender (http://tinyurl.com/d2tbw53) still available via EBAY or Amazon. It was a 49 mHz 2-way messaging transceiver with a 500 foot range. It is said to exploit a *still* classified USAF radio encryption technology. Evidently Ohio Arts had/has some employees once associated with such stuff in their R&D dept. They evidently saw no reason why not use such technology sans permission from UNCLE SAM. The reasoning was all they had to do is request that the FCC keep the details sequestered, which they did. The PCB is all SMT electronics and good luck trying to reverse engineer the signals with your spectrum analyzers. Cool toy though.
Other interesting 2-way messaging RF toy technology is the Russian-engineer-inspired CYBIKO. Also discontinued with only a small dedicated following special interests groups. It was a 900 mHz toy. This toy had really promising uses only the amateur-coder-programmer could imagine. Maybe that’s why it got pulled?
Another is Hasbro ChatNow SMS walkie-talkies. Somehow the engineers designed a protocol that just can not be easily tracked with standard scanner, frequency counter, and analyzer tools. Evidently it sets up a control channel (maybe random) and then sends out data to other listening units to set up a messaging channel. Really intriquing design. Also discontinued.
The next one is truly amazing and is NOT discontinued: The TriSquare TSX300 spread spectrum walkie-talkies. (http://www.trisquare.us/tsx300.htm) These things are not really toys but they are relatively cheap. And it appears possibly NO ONE can monitor you with a scanner! You can also do SMS text messaging.
BTW – I spoke too soon. The TriSquare was shortly pulled from the US marketplace. Good luck finding one now at a reasonable price. I guess we HaDers have to hack out our own version with an Arduino or something. :-)
Bill Bailey – Don’t give up on us that fast. Yes we like to argue a bit but we have some bright minds here on HaD. Browse around or use the search engine. What were you looking for? One of us could give you the info you seek (just as long as its legal!). :D
Your comment is the only place in the entire internet that I have seen a reference to the Zender using USAF encryption technology. Can you provide more information on this as it is fascinating…
I too noticed that same Internet anomaly. I’m beginning to suspect someone is skimming the Internet to “sanitize it” of sensitive subjects. The information by Ohio Arts was a long time ago. I may have got it from skimming subject matter discussion forums. Sometimes employees like JohnConnor let the cat out of the bag by complaining about stuff they should STFU about. I think JC is a Senior RF Engineer from Harris, RCA, Bechtel, Battel, or Philips but I could be wrong. Maybe some OA employee was blowing off steam or something. I only do OS information gathering.
Or I may have got it from the public FCC database in where you can actually read the manufacturers pleas to make their stuff more secret from prying eyes. The FCC usually gives in too (sometimes not completely dumbed down). This particular USAF technology was briefly in the movie Fail Safe (1964). But it only showed pilot’s user interface not the radio’s inner workings (it was 1964!). I think it’s based on something like P25 as the Zender technology is based on X.25 encryption. That is also used in IT world for SNA3270 remote terminals with mainframe computers.
Just did some more OSINT researching and the FCC site has the LZ3333 unit which is the only RF transceiver Ohio Art Toy Co ever made. The inventor was the late James E. Watson, who was in USN and US Army. He died 12 years ago. Can’t find any USPTO data on it. It allegedly also uses the P25 format and was a popular calculator-like toy back in 1994.
When listening on 49.86 Mhz you can barely hear it as it’s only little quick blips. It will transmit a full alphanumeric text sentence to it’s properly encoded partner unit. Range is upto 500 feet (152 m). I think you can still get some on EBAY. I heard it was Watson’s idea to use this technology as a marketing idea. Since there is no patent license to contend with, they just rolled with it.
You could modify the output to a more powerful radio transmitter. However, you need to port the radio scanner input to this device as there is no known software that can decode it yet.
https://thumbs.worthpoint.com/zoom/images2/1/0211/22/zender-text-message-tranceivers-ohio_1_2f0266ccc73223a7d7e30647e27e145a.jpg
I watched the 1964, AND 2000 versions of Fail Safe, and although the movies are almost identical, it would take an incredible stretch of the imagination to think of the Zender as even remotely close to the Fail Safe code device. I also watched Dr. Strangelove, and despite the device in that movie being larger, and electro-mechanical, the purpose, operation, and description is nearly identical the the operation of the Zender. I think you got your movies mixed up.
Random Internet Commenter – On 2nd thought, after reconsidering what I’ve already said, I think I may have mangled the last transmission. The Ohio Art Toy engineer PROBABLY meant that the toy exploits P.25 just like the other pink GirlTech IMME toy the OP is talking about. P.25 does have a clandestine past history and that’s probably what James Watson meant by saying a classified USAF encryption method was used. That was back in 1994, Not so much classified today. However, some guys in Australia allegedly broke it. https://goo.gl/XpC59U
Good God! I came to this site for some useful info and I end up reading an argument (a gripping one at that. lol). No useful info here. Good luck…
What did YOU provide…?
In regard to the post of “When listening on 49.86 Mhz you can barely hear it as it’s only little quick blips.”, those “quick blips” are roughly six seconds long, and as the unit sends them several times, what is heard can be likened to monitoring a national paging frequency for several tens of seconds. It’s harsh, loud, often, and gets old, really fast.