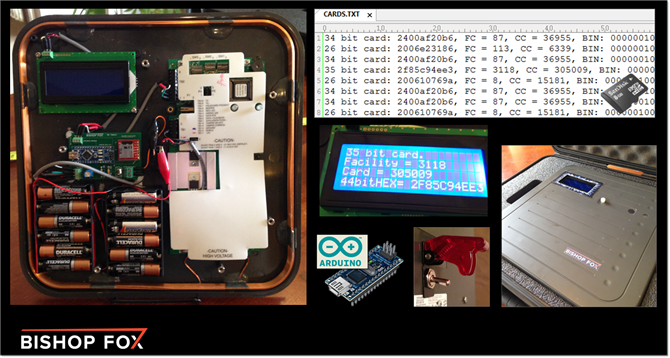
Security researcher [Fran Brown] sent us this tip about his Tastic RFID Thief, which can stealthily snag the information off an RFID card at long range. If you’ve worked with passive RFID before, you know that most readers only work within inches of the card. In [Fran’s] DEFCON talk this summer he calls it the “ass-grabbing method” of trying to get a hidden antenna close enough to a target’s wallet.
His solution takes an off-the-shelf high-powered reader, (such as the HID MaxiProx 5375), and makes it amazingly portable by embedding 12 AA batteries and a custom PCB using an Arduino Nano to interpret the reader’s output. When the reader sees a nearby card, the information is parsed through the Nano and the data is both sent to an LCD screen and stored to a .txt file on a removable microSD card for later retrieval.
There are two short videos after the break: a demonstration of the Tastic RFID Thief and a quick look at its guts. If you’re considering reproducing this tool and you’re picking your jaw off the floor over the price of the reader, you can always try building your own…
















A followup article on a presentation that was a followup using the exact same reader over a year prior.
Anybody relying on security from a card that simply broadcasts its credentials in cleartext is a fool, of course.
The problem is these cards are commodity items so they ALL will talk to the same challenge query from HID brand readers. So a thief get’s a HID reader, hacks it and now you have everything you need.
Card access is ungodly insecure, but most security professionals lack ANY education in electronic security to know any better. I was told by one “experienced professional” that they were unhackable and his installations were impossible to get into the room without the proper card. I won a $100 bet from him by grabbing a step ladder, popped the ceiling tile and dropped down on the other side, then yelled out, “less than 5 minutes to defeat your security”.
He was pissed and was going to reneg on his bet.
Don’t use a motion detector to unlock a door from one side and a keycard or other lock from the other side, if the door doesn’t seal tightly. http://thedailywtf.com/Articles/The-Flux-Capacitor.aspx
“Chad left his ID badge at home. That’s inconvenient in any office, but when you work at a US Naval Base, they take security more seriously. Without his ID badge, the door wasn’t supposed to open.
Chad was a Marine veteran who had become a civilian IT contractor. The enlisted men had a name for this sort of security: “Private Proof ”. A Marine Private might be stymied, but anyone with two brain cells to rub together could bypass it. Chad and his co-workers kept a large “year-planning” calendar on the insecure side. Chad pulled it down off the wall and slid it beneath the door. Waving the calendar around triggered the motion-sensor on the secure side, opening the door.”
Doubt it….passive infrared motions, which is most likely what it was, detect heat.
Or cold….
This was a nice read… last year: http://proxclone.com/Long_Range_Cloner.html
He sent us the link literally yesterday: I couldn’t find a single news article that links to the project/build page on the firm’s website, so I suspect that’s what’s new (and what HaD readers care about).
I was aware of a few custom solutions (Proxclone – http://proxclone.com/Long_Range_Cloner.html, Wired Magazine RFID Reader – http://www.wired.com/threatlevel/2009/08/fed-rfid/, …) that people had discussed and posted photos of, but that had never actually ended up releasing the tools, schematics, code, guidance, or anything that would remotely be useful in replicating what they had done. This holds especially true for your average Fortune 1000 security professional trying to get setup for an RFID penetration test.
The tool discussed in the Wired magazine said they’d be releasing a $50 kit you could use to recreate it at h4rdw4re.com. It never happened. On the ProxClone contact page (http://proxclone.com/contact.html), he specifically says he will not be releasing his code and not to ask. Ultimately he posted some pictures and an electrical diagram. Neither of these are practical or useful to your average security professional trying to get up and running for an RFID pentest.
By contrast, I actually released what I built. I released the parts list, Fritzing diagram (also Extended Gerber format), and Arduino code. After ordering and receiving parts, you have all you need to get up and running in a couple hours. I’ve been getting lots of emails from people excited because they were able to get a version of their own up and running in an afternoon, most with photos of their new tool. I’m going to re-state that because it bears repeating. They got up and running in an AFTERNOON. I would have killed for something that got me up and running in an afternoon before. Instead, I had to code, design, build, and lord knows troubleshoot my own device from scratch over the course of several weeks. I am more than happy to have released the results as to save others the time and trouble. If you don’t see value in that, then I don’t know what to tell you.
“that had never actually ended up releasing the tools, schematics, code, guidance, or anything that would remotely be useful in replicating what they had done.”
Well besides the project that actually did release code that seemed to make it into your project in large chunks without attribution.
http://colligomentis.com/2012/05/16/hid-reader-arduino-rfid-card-catcher
Considering that link’s dead…
Thanks for this! Very well documented and easy to follow, even for a noob like me. Took me two days to figure out my garbage was coming from needing to change the serial baud rate, but once I did that, everything worked like a charm!
Speaking of snooping, WLAN bugs found in flatirons! From BBC news:
“State-owned channel Rossiya 24 even showed footage of a technician opening up an iron included in a batch of Chinese imports to find a “spy chip” with what he called “a little microphone”. Its correspondent said the hidden devices were mostly being used to spread viruses, by connecting to any computer within a 200m (656ft) radius which were using unprotected Wi-Fi networks. Other products found to have rogue components reportedly included mobile phones and car dashboard cameras.”
Heres a link to the footage of the teardown if anyone is iterested.
http://www.youtube.com/watch?v=hkiqenPy8zY
interested*
Excuse the typo, sorry!
In the 60’s and 70’s the CIA and Xerox installed cameras in photocopiers leased by the Soviet government to take pictures of everything that was copied. The contracts stated that only authorized Xerox service people from the USA were allowed to service the copiers. Xerox trained CIA agents to service the copiers and as part of the regularly scheduled cleaning, toner replacement etc, they’d also change out the camera film.
Some models of IBM Selectric typewriters are very easy to convert to a computer input device – or to bug. They have a small number of levers which are actuated by key presses. It only takes some properly positioned switches and a bit of electronics to convert the combinations to binary code. Just like a keylogger.
Selectric typewriters in secure government facilities were routinely checked for additions which didn’t come from IBM.
It’s just as easy to convert one to a printer, by reversing the encoding to trigger the solenoids connected to those levers. It’s what many homebrew computer builders did in the late 1970’s when keyboards and printers were hideously expensive but a used Selectric could be bought for $100 or less.
I don’t think the Russians need Chinese spies to give them viruses. It might be a start if they stopped writing so many of the fuckers.
Who knows, maybe it’s disinformation by the Mafiya? They’ll sell you “virus removal” software AND a new clothes iron for just 50,000 Rubles!
[I confess I’ve no idea what a ruble’s worth, and they probably use Euros anyway]
You are asking a bit too much. (a bit more than 1000 euro).
Has this guy broken the secure environment? Visa would be mighty pissed about that… I should say has he implemented software accessing “secure” (lol) RFID information.
NFC payment cards don’t use any active authentication or encryption, they use a rolling code system similar to RSA SecurID. You can a credit card with any NFC-equipped phone, but the CV2 code will change with each read, and reusing a code or using codes in the wrong order automatically voids the card number.
how can a rolling code system be passive?!
RFID tags have a chip that’s powered by the reader. I assume it’s not much harder to put more silicon in there, and up the reader’s transmit power.
Blah. I remember HaD having a post that I’m not inclined to look for about some presentation that handed out rfid tags to listeners and the presenter scanned them from across the room(or so he said) with som ham radio kit.
Why do this and look like a risky person when you can just warddrive up to a front parking space and scan people going in and out?
This particular set up only reads HID Prox cards.
Not to say you couldn’t get a credit card reader off of ebay and use the rest of the setup
to skim creditcard codes.
and you might have to mod the sketch of the controller to handle the data from the
reader correctly.
Back to the Prox card.
Granted it is one of the most prevalent card access medium used in the US.
If your secured area uses only the presences of the card to allow access to a secured area then you are open to this attack.
The next step to making this type of access system a little bit more secure is to add a PIN (Personal Identification Number)
Most data centers that I have access to use a combination of the card plus a PIN and Fingerprint.
Other higher security areas ( I won’t mention where.)
Use other bio-metrics.
Retina scan
Hand geometrics. (mesures finger length)
Keypads with individual displays under each key.
That can be only be read by the person standing directly
in front of the keypad.
The keypad randomizes the pattern of the alpha numeric displays position
so you couldn’t figure out someones PIN from a distance.
All of the above measures are not 100% secure but in combination
they are harder to defeat.
also the higher security areas have your card ID married with your photo on file and a remote security operator compares your ID photo with live video before granting access. You also had to put the ID on top of a reader that the operator could see and compare to the live video and file info in addition to you inputing your PIN.
I have never heard of that. It is also stupid. Why not just, you know, have a guard and a security badge like we have had for decades?
Cheaper to have one guard operate 20 doors remotely than have 20 guards and assign one to each door. If you are running a larger secure operation that needs to be accessed from multiple entrances this make sense.
Hi. My name is Werner Brandes.
My voice is my passport. Verify me.
and facial verification is also easy to get past if you find a good enough latex and makeup artist.
“All of the above measures are not 100% secure but in combination
they are harder to defeat.”
Latex is old school. Silicone made it obsolete 20+ years ago.
Do you even need latex? From what I’ve read, facial-recognition, or at least the early stuff, used things like nose / eye / mouth / eyebrow distance. If you measure these accurately, you get an accurate system that’s not too hard to program.
I might guess that a few light and dark spots with makeup might do the job. Milhouse your eyebrows so they look higher up. You could even remove the real ones. If you’re a woman nobody will think that’s odd. Or a drag queen I suppose. I guess similar stuff could be done for the eyes and nose. Blank your mouth with pale lipstick then draw a new one on.
Head size would be a bugger but maybe that’s just relative to the features. If you magnify your features accordingly the machine might just think you’re stood further away.
Not something I’ve tried but I bet it’d be a ton of fun for the people who develop this.
For the keypads with display thing, why not just use a touchscreen with whatever they use on ATMs over the top? It’s some sort of film or optical thingy that makes the screen look completely blank from the side.
if any of you got credit cards with rfid you may want to get rfid blocker sleeves because someone could clone your credit card and live hi ho yippy o on your credit card.
same could be done in theory for the disney cards if they can allow purchases on the cards.
Most rfid credit card transactions require your zip code or pin code.
and using the car number online require the CVV code and expiration date.
I would hope that info is not transmitted.
RFID card transactions, at least in Europe, don’t require anything except putting the card on the reader.
Honestly though, the limit on my card is £20 in a single transaction and £50 total before it requires an online transaction (i.e. I need to put my card into the reader and type the pin in, not “online” as in on the Internet). There are bigger things to worry about.
Mythbusters was going to do episode about RFID security. Companies unleashed the lawyers so no episode.
http://www.youtube.com/watch?v=-St_ltH90Oc
As far as I know security hasn’t improved from those days that much, if at all.
EETimes published years ago (print) that the Navy was able to read RFID tags from a fighter plane 1.5 miles away. Something banks and other govt. agencies don’t want people to know, I bet.
I’m gonna call bullshit on this. There’s no way a tiny RFID tag can transmit over a mile. Even if it could, how would you even receive that many IDs at once? I imagine that there’s a whole lot of RFID tags in a mile and a half. There’s at least 160,000 just in the few thousand square feet of the library I work in. I don’t think there’s a feasible way to read our 160,000 tags and the many thousands of other tags in the city.
Regardless of any technological hurdles, why would you even want to do this? To get a security pass for a building, or something I’d presume. The question is then, how do you even find the ID you want out of the potentially hundreds of thousands you’ve scanned?
NASA is still receiving data from the Voyager probes, at the edge of the solar system. The effective received power is one billion-billionth of a watt. Sure, they have bigger antennas and better amplifiers than onboard that fighter, but calling bullshit because of your underestimation of how tiny a signal can still be picked up is bullshit itself.
OK
Lets put things into perspective here.
#1 these are passive tags not active.
Passive tags have no power source and use the RF energy field
to power the chip and broadcast back the data.
Active RFID tags have a power source and constantly transmit the data.
The Voyager probes transmit in the range of a few milliwatts, IIRC. But that’s through space, which is mostly empty. They have a clear, direct line of sight with Earth. The antennas they use to pick up those signals are many meters in diameter, and I think they use huge arrays of these antennas, but I might be wrong.
RFID tags use what, a couple of microwatts? They have trouble transmitting through an inch-high stack of CDs, how are they going to go through buildings, trees, people, cars, etc?
Comparing RFID tags with the Voyager probes isn’t really productive, they’re entirely different things. And, like Louis said, RFID tags are passive, they’re powered by the reader. The Voyager probes have cool nuclear thermoelectric generators.
Voyager’s transmitter is 23 watts, just to mention.
Rexxar: Voyager is an active transmitter, but that’s not the point. The EFFECTIVE RECEIVED POWER from their transmitters is one billion-billionth of a Watt. That’s what arrives at NASA’s antennas. That’s what is left of those 22W beamed directly at earth, through empty space.
And if they can get an actual signal, carrying data, from 10e-18 W received power, I have no reason to believe you CAN’T pick up a signal from an RFID card 2000 meters away, given some dedicated, bleeding-edge skunkworks gear.
If the skunkworks gear includes the 70 metre dishes (or a pair of 34 metres) NASA use to pick up Voyager, in a veryvery directional signal from outer space, in a fairly noiseless waveband, travelling through empty space with nothing to disturb it, then yeah ok. Though that assumes the RFID card is in radio-quiet outer space, not noise-laden Earth. And Voyager is self-powered. To power your RFID card remotely you’re gonna need a powerful and directional transmitter.
Anyway yeah I bet it’s impossible. Shannon’s laws and other stuff to do with interference and power levels ‘n’ stuff. There are veryveryvery clever techniques to receive signals below the level of noise, though they require the transmitter to use the same techniques. I expect the RFID people were pleased enough with themselves when they got remote-powered CPUs with transceivers to work at all. Even reeling off a serial number was pretty impressive to me the first time I heard of it.
So much for the “security” of implanted RFID chips.
Oh well, back to the piercers.
Right now my implants are pretty safe,
for the simple reason that not many people have them and therefore aren’t a target.
12AA batteries? What the hell just use a couple 9 volts instead.
9V batteries don’t have the same current capacity as a equal amount of AA batteries.
The spec for the reader he used says it runs on 12 or 24v. So that’s 8 or 16 batteries, I wonder why he’s used 12?
Just a guess, but so he can run them down to 1.00v each so that a least a decent amount of the capacity is used.
What he really missed from the data sheet is that it draws more amps at higher voltage. A friend of mine (also a prof pen tester) is building one of these, he sent me the link and I rofled. I responded no im not letting u use 12 fucking AAs I called HID tech support because I noticed that bit on the data sheet about power draw. It has max range at its max voltage. Its probably not a huge diff, but when the objective is the longest range possible its a rather stupid detail to over look. Other issues with AAs include cost of replacement and internal resistance. I assembled a Battery Pack with 4x 18650s (the Panasonic 3500mah), a protection + balancing pcb, an output lead if you want to use a more beefy hobby charger to balance faster. I am shipping it to him with 2 DC-DC converters, one to run the Reader one to run the arduino clone. I took care that I selected units that operated above the 125khz used by the tag. With this setup it should run all day and If one wanted they could keep 4 charged 18650s in their pack to swap out…say if the last guy forgot to charge it. Im looking into an arduino compatible mcu that can also do wifi so the person using it in the field could monitor it from his/her smart phone with out opening their bag.
It is definitely worth mentioning that this applies to some 125kHz RFID cards. They’re designed to be fairly simple and are generally a “what’s your card number” sort of system.
It doesn’t apply to any of the 13.56MHz systems that are used for things like NFC, transit systems or credit cards. These don’t have this sort of range, and the communications between card and reader aren’t as simple and spoofable.
I mention this because I just saw a tweet from a company that should know better saying UK (MIfarre based) transit cards are vulnerable.
And if the person grabs your rfid passport details with your card you are in for one hell of a ride!
Anyone that has a proper RFID reader/write for tracks 1 and 2 contact me, am in the market. Looking for something from Russia. Contact me, once we contact we go PGP from there on out
-F
Did you ever find someone to build this devise? I want to purchase one as well
lol I’m with you buddy. Let me knw if you found somebody
Does the tastic rfid thief read credit card dumps track 1 and 2
“from a fighter plane 1.5 miles away.”
I also call BS on this! Ain’t no way, for the many reasons posted above.
(Said from a 35 year RF Engineer)