There’s pandemonium on the streets. You look down from your 4 story apartment and see hundreds of people marching and chanting. You pick up your phone and call your buddy, expecting it to link up to the nearest cell tower which will route your call to where it needs to go. Instead, without your knowledge, you link to a tricked-out police surveillance truck a few blocks away. They intercept your call and listen to the conversation in hopes of tracking the protest.
Dispatch: “CPIC [Chicago police’s spy ‘fusion’ center] on the air for a mobile”
Officer 1: “Go ahead”
Officer 2: “Yeah one of the girls, an organizer here, she’s been on her phone a lot. You guys picking up any information, uh, where they’re going, possibly?”
Officer 1: “Yeah we’ll keep an eye on it, we’ll let you know if we hear anything.”
Officer 2: “10-4. They’re compliant, and they’re, they’re doing ok now but she’s spending a lot of time on the phone.”
Officer 1: “10-4”
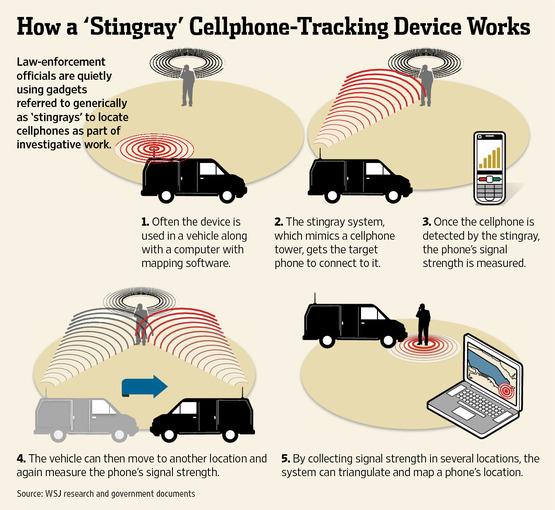 This scenario undoubtedly took place on November 28th of this year in downtown Chicago. People began to notice the truck following the protest, some even complaining that their cell phone stopped working when it was close by. Most probably had no idea that the police truck was equipped with Stingray technology. It forces your cell phone to connect to it as opposed to the nearest cell tower, allowing authorities to listen in on your conversations and track individual phones by moving and measuring the difference in signal strength. The hacking group Anonymous released some audio of a conversation between two officers and a command center (block-quoted above) which provides damning evidence that such actions indeed took place on Chicago streets.
This scenario undoubtedly took place on November 28th of this year in downtown Chicago. People began to notice the truck following the protest, some even complaining that their cell phone stopped working when it was close by. Most probably had no idea that the police truck was equipped with Stingray technology. It forces your cell phone to connect to it as opposed to the nearest cell tower, allowing authorities to listen in on your conversations and track individual phones by moving and measuring the difference in signal strength. The hacking group Anonymous released some audio of a conversation between two officers and a command center (block-quoted above) which provides damning evidence that such actions indeed took place on Chicago streets.
So here’s the question: Can it be fooled? Can you spoof the spoofer? Can you tell the difference between a signal from a Stingray versus a cell tower? If this is not possible, surely the cell network providers can add something to the signal allowing end users to verify that it is a legitimate signal from a cell tower. But can it be done in a way that a Stingray can’t replicate?
https://www.youtube.com/watch?v=QLpk2EB6LMo
Thanks to [John Tirelli] for the tip!
















Good morning Will, hi there everyone still following this important question!
I would like to quickly recommend our Open Source Project on GitHub to you: The Android IMSI-Catcher Detector! Get it here: https://secupwn.github.io/Android-IMSI-Catcher-Detector/! Our project is developing this App completely FOR FREE and OPEN SOURCE to detect and avoid fake base stations (IMSI-Catchers) in GSM/UMTS Networks.
Everyone is very welcome to join our effort against StingRays, IMSI-Catchers, Silent/Stealth SMS and other attacks – even the smallest pull requests are extremely welcome! Thank you for checking out and following our GitHub respository.
Have a happy and safe New Year everyone! ;-)
SecUpwN and the whole AIMSICD Team
Good morning @willsweatman and hello to everyone else still following this important question!
Let me quickly introduce our Open Source Android project to which everyone is very welcome: The Android IMSI-Catcher Detector (AIMSICD) on GitHub: https://secupwn.github.io/Android-IMSI-Catcher-Detector/! Our App is currently in heavy development to detect and avoid fake base stations (IMSI-Catchers) in GSM/UMTS Networks as well as SIlent/Stealth SMS attacks. On top of that, it will enable several protection mechanisms against these creepy devices. Feel free to help us, we are currently seeking Android developers and hackers of any age, even the smallest pull requests are extremely welcome!
Thank you for checking it out and folllowing along on our GitHub.
Have a happy and safe New Year, Geeks! ;-)
SecUpwN and the whole AIMSICD Project.
So many of the comments are so far off topic. The original question is “How do you defeat stingray”? – With a specific scenario if a peaceful protest.
I *loved* the comment about the cops just talking to the organizers. If its a peaceful, legal gathering there’s no need to break out the deception.
If for some bizzaro reason the organizers feel it necessary to defeat electronic surveillance (e.g. stingray/hailstorm) it seems to me you could simply make up your own sim cards before the rally/protest, and set up a basic cellular base station that travels along with the group (a laptop and an antenna is all it takes). The base station would identify itself as a fake network, say, “Legal Protest Cellular (LPC)”, and the sim cards would only allow the phone to connect to that network.
Sure, this method limits communication to only those within the group (i.e. range of the base station), but really, what more does one need in a station like that.
This method solves a few problems at once.
First, the guys in the surveillance van don’t have to break the law anymore – there is no need to spy in the “innocent” (e.g. non-participants)
Second, it makes it very clear when a surveillance vehicle is intercepting calls because the caller/callee won’t have an active connection to the LPC base station. A little bit of software on the (Android) phone makes it easy enough to check the status on an incoming or outgoing call.
I have a question regarding stingray, if my phone have a feature to lock on an specific GSM tower (BTS) so it will never connect to fake truck tower, can it avoid stingray tracking?
Even if you would have the possibility to do so (which does not exist, to my knowledge), your phone would always connect to the strongest signal source (which will be the IMSI-Catcher). Furthermore, these devices can fake the BTS ID pretty well. PWNED. Alternatively, feel invited to check out https://cellularprivacy.github.io/Android-IMSI-Catcher-Detector/ and see if you can contribute.
Think I captured pic of fake stingray operator https://www.anony.ws/image/JIYM
What is the best app that i can install that will block my ip or what ever else uncle sam might be using to ping my phone?