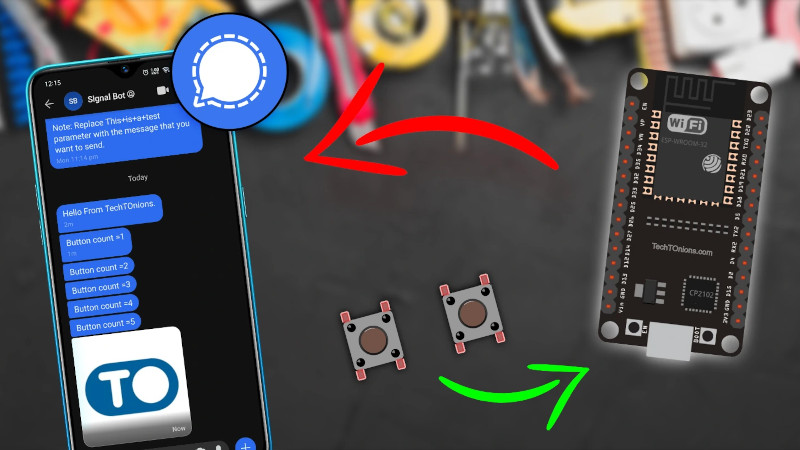
Signal is a popular encrypted messaging app, typically used on smartphones. The cross-platform service can now be used via the ESP32, however, thanks to the work of [Dharmik] and [Tirth].
The demonstration is simple, using an ESP32 microcontroller fitted with two push buttons. When one button is pushed, it increments a counter and sends a Signal message noting the current count. The other button sends an image as a Signal message.
The project relies on a Signal bot to deliver an API key that enables the project to work. Messages are sent by making HTTP requests with this key to the CallMeBot.com server. With the API key as authentication, users can only send messages to their own number, keeping the system safe from spammers.
While the demonstration is basic, it merely serves to illustrate how the project works. The aim was to allow home automation and other Internet of Things systems to send Signal messages, and through this method, it’s now possible. The highly security conscious likely won’t want to rely on a random third party server, but for those tinkering around, it may not be such a big deal.
The Internet of Things has a long history with self-messaging projects; we featured the Twittering Toaster back in 2008! Video after the break.















This seems to forgo the security niceties of Signal. Rather than using a third-party service, perhaps run Signal locally on a different machine with remote debugging enabled?
https://github.com/mandatoryprogrammer/signal-bot
This doesn’t fix the security concerns between the ESP32 and the relay system, but at least it keeps it local.
Would be nice if it’s possible to send data back to the ESP32. This would open the possibility of using Signal as a medium to fully connect ESP32’s over the web.
Yes, you are right the bot that we have currently used is still under development. And they will be adding lot of new features to their bot in near future,
And we continue this interaction series where we are finding different approaches to interact with social media platform.
Thank you for reading and suggestion.
Tcp/IP over Facebook Zero IM? For those places where it is free. Just an idea.
In case you want to self host: https://github.com/bbernhard/signal-cli-rest-api
Let’s hope the coming hordes of signal powered IOT devices don’t kill the network.
I have trouble with wifi. how using wifi mesh on small city 3-10km diameter?
Lora and an uplink
Why not use XMPP-compatible messanging service?
It’s not the new hotness.
Signal isn’t that either
Would this work? (for the medium-paranoid)
Add ECC608 to ESP, store private key on this, use same to generate shared AES128 key via ECDH with remote host, then only send AES encrypted data from ESP, but use ECC608 to hash and sign payload.
Telegram offers a perfect API for this… No third party service etc. Just the Telegram Bot API…
And closed source server. Hard pass.
Yeah, better use an third party server with unencrypted communication and under development software than using the telegram api which works both ways, is encrypted and is been working great for years…