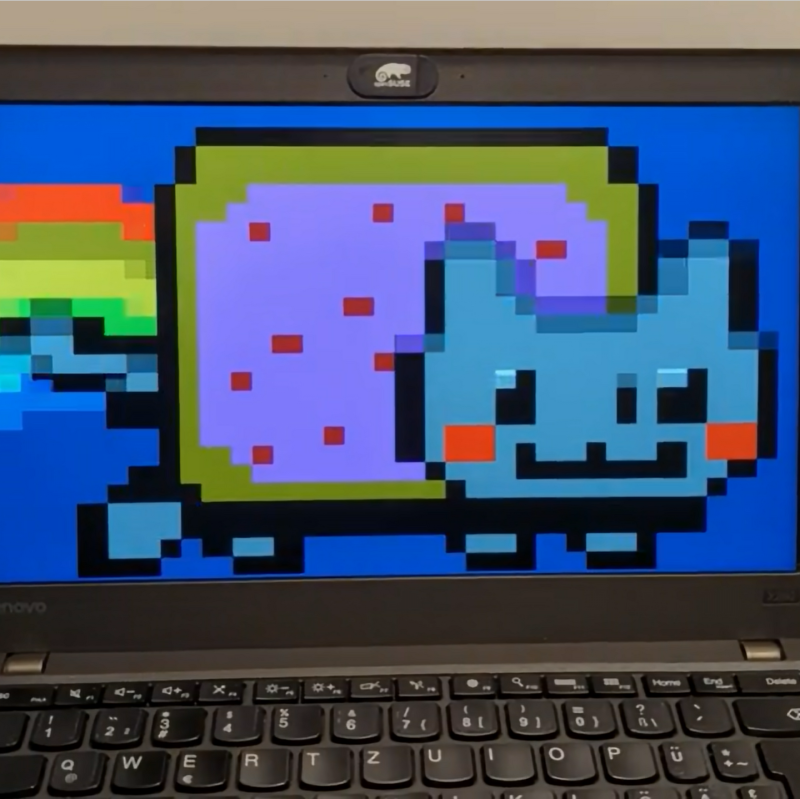
The Unified Extensible Firmware Interface (UEFI) took over from the classical BIOS some years into the new millenium. It’s typically used for running a computer at the basic pre-OS level, and most of us don’t even notice it past boot time. However, you can do some neat things in this space—you can even port over Nyan Cat if you’re talented like [Cornelius].

Yes, Nyan Cat is now available as a UEFI application, running via the EFI Simple Text Output Protocol. [Cornelius] approached this creation by first learning Rust, before progressing to the Hello World stage. Before long, the computer was booting up to display a simple text message with no OS required.
From there, creating the Nyan Cat animation required figuring out how to display it as a bunch of dancing characters, which is where the Simple Text Output Protocol came in. Nyan Cat was really the perfect animation for the UEFI environment, since its simple pixel art style was easily recreated with text. With a bit of work, the animation came together, with a remarkable resemblance to the original artwork.
All that’s missing is a routine to play the music over a PC speaker; only, those are hardly a thing anymore. A pity! In any case, if you’ve been cooking up your own nifty UEFI hacks, don’t hesitate to drop us a line!















I consider UEFI a major security threat. My rig uses Gigabyte EP45-DS3L mobo and C2D E8400 CPU. It’s still more than enough to run web browser, gcc, CLISP (LISP intrerpreter for Windows), Red Faction Guerilla and Gothic 2. TrueCrypt also works like a charm on this setup and provides deniable security in case I ever get raided by ministry of internal security (ABW) or police.
Nobody’s itching at the chance to poke holes in your UEFI to access data of crucial importance to national security like your Red Faction savegames, and if they were it’s not by sticking to BIOS that you’ll keep them at bay. And on the off chance you actually are a person considered dangerous by government entities, it’s quite irresponsible on your part to be gaming on your crimestation. Do yourself a favour, ditch the paranoia and get something that won’t half an age to load anything on the modern Internet.
Hi, you may find this news article to be interesting.
https://tinyurl.com/2avyj79a
Very nice technical achievement but a failure on the image processing side. The original image has 21 “pixels” in height, stretching it to 24 lines was a terrible idea and it completely breaks the pixelated style of the image. Just needed to fill the extra lines with the background color and it would be perfect.
and if you don’t have the space, you can always use my master-boot-record version :-P
https://github.com/brainsmoke/nyanmbr (not 100% true to the original, and no sound, but what do you expect from 442 bytes :-P)
Interesting timing. I was playing with the POSIX-UEFI project (https://gitlab.com/bztsrc/posix-uefi ) over the weekend just to see what sort of toys I can make for it.
I think a Zork/z-machine would be a good fit for what’s supported in the libc in POSIX-UEFI or the capabilities of UEFI in general. Maybe not as exciting as Nyan Cat. But a working C environment is more my speed than learning Rust. Another idea is a stripped down version of Rogue, but getting an old build system to target something it was never intended to support can be a wild goose chase sometimes.
proof that UEFI bios are crap… easy to install a virus/tracker/whatever into it and compromise the whole system with zero protection..
I still prefer UEFI Zork.
Lots of “uefi is bad complainers” here, this only works if you set your firmware(bios menu) to allow it. Secureboot is a thing, and you can disable the automatic adding of external bootdevices to a bootselect menu.
As if yall forgot about optionroms, just insert on the isa, pci or lpc bus and away you go.
Now, intel Me or csme today, is another story and the way uefi is implemented or worse, the defaults by some manufacturers is definitely debatable. But the idea of uefi is pretty smart and secure enough, especially if you can trust your own hardware
SecureBoot is a non-free software, cannot be audited and since its encryption keys are owned by Intel, Microsoft and Apple it’s a de facto a government backdoor into any libre encryption code.
See Richard Stallman interview about UEFI to learn on how it presents a grave danger to libre software ecosystem.
“Now, intel Me or csme today, is another story and the way uefi is implemented or worse, the defaults by some manufacturers is definitely debatable.”
To my knowledge, there is no other implementation of UEFI in practice.
All manufacturers use the intel example code as a blue print, sadly.
In simple words. The history of UEFI is quite confusing. 🙁
“But the idea of uefi is pretty smart and secure enough, especially if you can trust your own hardware”
In my opinion, OpenFirmware was the better, cleaner alternative.
The design flaw with UEFI is that it is too complex.
It’s more than just a firmware with a set of helper functions, like BIOS was.
The UEFI is a miniature OS in its own regards and that’s the flaw.
– Though “small” is relative, maybe. Windows 3.0, Amiga OS 1.x, Mac OS Toolbox or Atari TOS 1.04 were just as “small” if not smaller.
Anyway, the problem is that it can lie to the host OS and has network stack.
It’s acting behind the curtain, yet it has no firewall, no online-updater feature, no anti-virus software etc.
UEFI by view of an anti-virus software can be described as a backdoor, a trojan, a memory-resident virus.
Fun project. If you let it run long enough it will warm up your laptop, hopefully not enough to make it catch fire!