Over on YouTube [Matt Brown] hacks a Chinese security camera recently banned by the US government. If you didn’t hear about this you can find out more over here: Major US online retailers remove listings for millions of prohibited Chinese electronics.
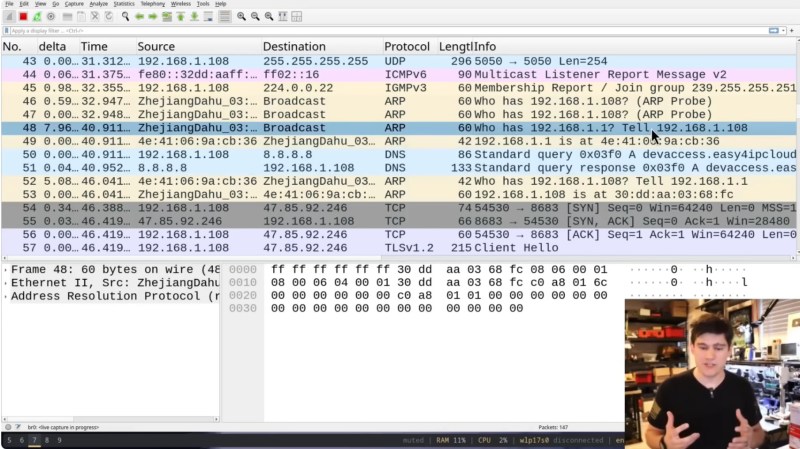
After powering the camera with a power-over-Ethernet (PoE) adapter [Matt] sets about monitoring network activity with Wireshark. The first data comes from DNS for the host devaccess.easy4ipcloud.com, which whois reports is operated by Alibaba Cloud LLC in California. This is a Chinese owned company with servers in the United States.
[Matt] covers some basics of TLS and how it works. He then goes on to explain how a Man in the Middle (MITM) attack works at a high level. To setup a MITM attack against the camera [Matt] sets up some port redirections using iptables for ports 443, 15301, 8683, 9898, and 12337 which his Wireshark analysis indicates were being used. His MITM attack works, which means the device is not properly verifying its certificate signing chain.
[Matt] goes on to reverse engineer the custom UDP protocol used for transmitting video data. He uses a vibe-coded Python program along with ffmpeg for that and manages to reconstruct a few frames of video taken from the UDP packet capture.
We think it would be safe to say that [Matt] did indeed find a few security problems with the camera as-is, but we don’t think that’s the point of the ban. The real problem is that there is auto-update facilities for the device firmware which means that in future malicious software could be uploaded by the manufacturer in the form of a firmware update. So even if this device was secure against MITM attacks and didn’t send unencrypted video data over UDP you would still have the problem of the firmware update if there is no trust.















There should be a different term between people who don’t know how to program using AI, and people who do know how to program but simply go “Eh, I can’t be bothered.”
Like, “I just slopped out the code with AI”.
I agree. But, also, I think vibe-coding is a misleading term in general. Sounds like someone’s writing pseudo-code, not “I told an AI to do it”. Should just be called “AI coding”.
you are writing pseudo-code, and the llm translates that pseudo-code into ‘real code’
I’ve had AI turn flow charts into code.
If this were a TV show in 2009 they’d say “We had the computer analyze the data steam and generate an algorithm that could reconstruct the video from the captured UDP packets.”
*stream
It WAS a TV show. Around 2002-2006 TechTV The Screen Savers had a segment with Kevin Rose demonstrating EtherPEG (or Driftnet?) to ?Patrick Norton? EtherPEG was a program sniffing wifi combing cleartext traffic for images to show on your screen, it let you see what everyone on the lan was browsing right now.
How about ” an untested piece of code got from the ‘net ” ?
The vibe coder may indeed have tested the output the LLM gave him/her.
Read as: The original coder that the LLM stole from may well have tested the code before publishing to their blog
This is just copium. LLMs write code suitable to the occasion, they don’t just copy paste code they memorized. This is no different from a human programmer who roughly remembers code she saw online, and adapts the technique for the new use case.
I’m tired of people claiming that AI is just fancy autocomplete, when there’s a whole neural network behind it outputting natural language and code and making effing sense. We are living in sci fi land now, and some of us are still in denial.
Presumably the same logic applies to any networked camera should the parent company’s government decide the device’s owner was worth snooping on? Plenty of countries in this world with overstepping authoritarian regimes that think the constitution is a guideline…
Well yeah, Snowden and others revealed that the US is capable of and is actively infiltrating the supply chain to insert exploits into network devices, there is absolutely no reason to suspect they stopped or that any other technically capable country isnt doing exactly the same.
A little Google digging will give you all sorts of examples of state security services hacking, overstepping boundaries etc to surveil all sorts of domestic organisations and you’d have to be dangerously naive to believe they weren’t also doing the same to gather intelligence on other countries.
The mildly cynical among us might even suggest that bans on Huawei gear were only put in place because they refused to backdoor their gear for western security services.
Also don’t forget the generic gag orders that companies have against disclosing that the us government has forced them to implement backdoors.
US doesn’t ban companies because they refuse to insert backdoors. Strong-arming tech companies like that is obvious, amateur hour nonsense that gets found out and makes headlines, rendering it worthless. NSA deals in 0-day exploits that nobody else knows about, including the manufacturer.
devaccess.easy4ipclound.com
(Clound?)
firmeware – firmware?
Does anyone even spell check anymore?
ipclown*
Sorry. Fixed those. Thanks for pointing them out.
Let us collect some open source pointers for all the Iot related stuff that is more secure.
camera: Thingino
switch: Tasmota
I’ll add another open source camera firmware project: openipc.org
Never tried it, but there’s https://openipc.org/
Thx for the url. Had never heard of it before.
Along the lines of Tasmota, there’s also ESPHome: https://esphome.io . A little less turn-key, maybe, but probably a little easier to do simplistic hacks on top of.
Every device with a vendor-controlled path to install software without user-interaction is untrustworthy. From chinese webcams to Google Android phones
Unfortunately, amen !
And yet any device that doesn’t will likely become part of a botnet because most people won’t bother with manual updates. Is the right compromise a default on auto-update that you can log in and disable?
The simple solution is to use the camera on a network that is isolated from the Internet. No auto updates.
The auto-update feature “which in future could be used to upload malicious firmware from the manufacturer” sounds like Standard Operating Procedure for just about every device and software maker. Using it as justification for banning devices is just thrashing around looking for something the ‘rubes can swallow.
I don’t like external accesses being done without permission which is why we run a PiHole on our network.
I don’t think devices should ever be allowed to auto-update unless the end user specifically opts-in.
Too many companies are now sending out ransomware updates that break features unless you pay to have them reactivated. If I were the kind of poor sod who buys cloud-reliant devices, I would be pretty displeased to find that my thermostat which has been working fine for 4 years suddenly requires a $10/month payment.
Cameras are one of those things that should be kept local.
Yeah. There’s a very widely-used home-computer operating system made by an American software vendor. It ships mandatory updates about once a month.
Sometimes these mandatory updates include firmware updates provided by the hardware manufacturer.
Sometimes the hardware manufacturer is in a country that may be on the “outs” with the current government of the United States.
Sometimes that hardware includes a camera.
I was going to chime in with just this. That design philosophy covers every Windows install and every piece of UEFI hardware it’s allowed to run on. Android as well. Nevermind the iPhone. That’s the vast majority of compute at retail.
So if the quallifier for the national ban hammer is “initiates updates with no authorization” I have some unfortunate news…
I recently found a generic pan-tilt webcam in the trash. “I’ll hack it” I though… What a disappointment! The factory root password is LITERALLY “1234”, it’s burned in the ROM portion of the firmware, it can’t be changed!
That’s like saying that it’s “operated” by AWS.
Show me an iot device that is fully secure…. They don’t exist.
Lets look for ms windows home calls too..
Any device wanting to send data somewhere else requires access to a network. Providing the right access level on the network will stop 99% of all these “attacks”. If you put a camera (or any device) on a network with external or internet access then obviously it can auto update to any behaviour the company or a hacker wants (easier if no security keys). But even without an update, images can be redirected as shown etc. This is all incidental though as simply stopping these devices from accessing the internet is all thats needed. If WAN access is available on your LAN then whitelist local devices (eg using MAC address) that are allowed to access external networks on your gateway, or Blacklist (MAC address) all devices that are not allowed external access on your gateway, use sub networks, physical separation etc , all of these will stop any unauthorized external access/data capture for most usecases. This problem is scaremongering for 99% of peoples domestic use. And if you do want external access to data/images simply use a seperate server/buffer PC rather than direct access and cache all the data you want to see – this again stops the device from being hacked etc. Who cares if this device can do bad things if its got no external access ?
I have one of these cheap camera’s, it’s still available on amazon. A couple of weeks ago I asked chatgpt and it suggested I run upnpc -l (linux bash), and it found an open igd gateway. With the name of my router, chapgpt walked me through how to disable udp. Now upnpc -l finds a disconnected idg gateway. It also suggested that I disable tcp/ip on the net for the camera’s ip, but that shut the application down. Apparently the camera has to upload in order to create the local files. Chatgpt then suggested that I install one of several applications to monitor the camera, instead of the native app. I’m considering this.
It’s great to see the progress that’s been made in suspecting undocumented backdoors in vendor firmware. If you suggested this in an online forum just a few years ago you would be called out for being a conspiracy theorist and troll.
The big mystery to me is why they waited 5 years to start banning these devices, because that is how long ago I directly pointed out to one Five Eyes SIGINT agency some very specific technical details of weakness in such technology.
“I directly pointed out to one Five Eyes SIGINT agency some very specific technical details of weakness in such technology.”
I think you just answered your own question.
Proof of concept vulnerabilities can be demonstrated on virtually any low-end consumer IoT device. I’m sorry, but I can’t see how this was a “hack” at all.
IP cameras should always be put on their own network that doesn’t have an internet connection. For remote access, you VPN into a server that has access to the camera network.
I have several of these cameras as well as an NVR, and I have firewall rules set to block any/all outgoing traffic from them to the internet. It’s interesting to me that they will try to hit public DNS servers by IP after failing to get out through my lan network server.
How do I get the rtsp URL?
I tried with Wireshark, but I only see port 17900, ports in the 10101-10110 range, and the dynamic streaming port, but I can’t find the exact URL.
I need to install the IP micro camera as a rearview camera in my car to view images from an Android app in the head unit.
I did some research and realized that the rtsp protocol is probably disabled and the MJPG images are encapsulated in the proprietary 1TEG and 2TEG protocols