Running suspicious software in a virtual machine seems like a basic precaution to figure out whether said software contains naughty code. Unfortunately it’s generally rather easy to detect whether or not one’s software runs inside a VM, with [bRootForce] going through a list of ways that a VirtualBox VM can be detected from inside the guest OS. While there are a range of obvious naming issues, such as the occurrence of the word ‘VirtualBox’ everywhere, there many more subtle ways too.
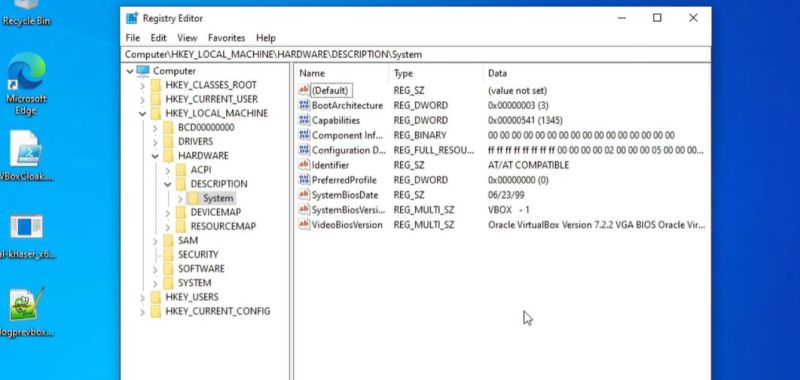
Demonstrated is the PoC ‘malware’ application called Al-Khaser, which can be used to verify one’s anti-malware systems, such as when trying to unleash a debugger on a piece of malware, run it inside a VM, along with many more uses. Among its anti-virtualization features are specific registry key names and values, file system artefacts, directory names, MAC addresses, virtual devices, etc.
In order to squeeze by those checks, [bRootForce] created the vbox_stealth shell script for Bash-blessed systems in order to use the VirtualBox Manager for the renaming of hardware identifier, along with the VBoxCloak project’s PowerShell script that’s used inside a Windows VirtualBox guest instance to rename registry keys, kill VirtualBox-specific processes, and delete VirtualBox-specific files.
Theoretically this should make it much harder for any malware to detect that it’s not running inside Windows on real hardware, but as always there are more subtle ways that are even harder to disguise.















What do we use to detect our universe is running in a VM?
Probably look at fundamental things like distances and time, see if they are quantized at some level. Non-infinite precision of the VM runner and all. You’d also expect the equivalent of drawing distance, like not being able to go faster than a certain speed because the VM needs to be able to keep up. Plus maybe the VM does some lazy execution, which could result in things not being calculated when there’s no observer. If you could find one of these things, I’d think that would be a good hint we’re running on a VM.
… the reasoning in the VM might also seem to be consistent and hence (such it may tell you) disallow provability of being inside…
https://jhap.du.ac.ir/article_488.html Explains why we couldn’t be in a simulation.
FYI this website is run by government of Iran, watch out for malware.
Well done!
So a leaky abstraction?
Leaking like a keg of finest german Pißwasser.
You might look for inconsistencies in unobserved systems, or correlations that imply information wasn’t fully realized until measured quantum mechanics already teases this with wavefunction collapse.
Delayed-choice quantum eraser experiments are particularly eerie — the choice to measure after an event seems to retroactively change its past behavior.
That could fit the metaphor of a simulation updating prior states once an observation is requested.
speed of light a kind of global tick limit on information propagation.
Cosmic censorship you can’t see inside black holes, perhaps because the simulation doesn’t render those details.
Information density limits – Bekenstein bound and holographic principle both say there’s a finite amount of information that can exist in a region of space, which smells a lot like a data cap.
Minimal measurable length or time step (like the Planck length/time).
Ultimately not much of this necessarily differs from reality, ex. Why would it be possible to store infinite information in a space?
Also, look for storage effects like where you’re snapshotting every change so your storage medium is ballooning when you have a lot of interconnected changes but if that interconnectedness breaks down you’ll see your snapshotting and media growth suddenly reduce. Also bear in mind that growth might not be as much as expected in such a case if you don’t account for deduplication.
This will also have a side effect that once all snapshots with related changes are pruned you’ll eventually get back your space but not before.
I have a suspicion that life might not be possible if the speed of light is instantaneous.
Planck’s constant is a thing. Resolution limits through all kinds of noise phenomena are a thing. Rayleigh`s criterion is a thing. We should be worried.
Good news everyone!
http://www.imdb.com/title/tt21814946/
The presence of “sudo add-apt-repository multiverse” in any log file is suspicious at the very least.
There’s a finite bit representation, orbital predictions have a small span of accuracy of around 2 million years. Oscillations would be more stable on a computer simulation. If the simulation was on a computer these orbital predictions would be accurate past 2 million years. Then perhaps we could comment on the magnitude computational complexity involved. My comment is pseudo techno jargon babble of course.
I’m looking for any easter eggs the developers left behind.
we are probably standing on one.
The Easter egg is that on one tiny rock in the simulation, there is a meat-based organism that built a computer that is running Linux which is running Wine which is running a Glide wrapper which is running UltraHLE which is running Legend of Zelda Majora’s Mask (which is actually an accurate representation of the world outside the simulator)
The Mandela Effect observations are the best tool for the job — it’s the clearest evidence that memory breach and corruption has occurred between VMs. Be on the lookout for the next occurrence, though that issue might’ve been patched back in ’09 under Patch 09.5: Observer Sync Update.
I don’t suppose asking Agent Smith is an option.
Difficult at the best of times, but what if Malware is attacking the hypervisor, BIOS or Management Engine/AMD equivalent? Black box security through obscurity only gets you so far. Ideally proxmox Hyper-V? Or BIOS level virtualization? Segmented storage/NVMe and PCIe?
I wonder if this would also work for malware that’s bundled with some video games.
Do you mean that malware that requires you to pay a subscription and have an internet connection just to play the game even as a single player, and that will also disable the game remotely at the whim of some board of directors in the name of profit?
+1,000,000 Quatloos
Q: If this was a simulation, I shouldn’t be freezing with my eyes shut dry in the morning of a late autumn (fall for the ppl over the a-pond)?
A: please wait for the behaviour chip.
A secondhand PC costs less than $100, just test on that.
You can’t attach a debugger to real HW as easy as to a hypervisor.
Sure, buy one of those PCIe cards that give another computer full runtime memory access to the machine it’s in and you are kinda set but that is a lot more work…
Neat, I knew about PCIe DMA in theory but didn’t know there was a software suite for it: PCILeech on Github. It’s compatible with PCIe-FPGA-DMA cards that are about $200.
If malware doesn’t want to run on a VM, then it can also be interesting to make a real computer look like it’s a VM to keep malware out.
We’ve reinvented Batesian mimicry: https://en.wikipedia.org/wiki/Batesian_mimicry
As I recall there are some timing-jitter-something issues inside a VM compared to real HW.
And even JS running in browser can test for that?
Not sure – the memory is a little vague.
Aye, there is jitter and UDP tests that make VM machines easily identifiable.
Would be funny to make any computer look like Arduino Nano. Or 555, whichever.
Neat – and this reminds me of trying to install free home user AV software on a windows 2008 server (or something).
The specific OS type was only checked during installation – one way around this was to basically spam a specific registry key with a script while running the installer to let it think it was on normal Win7.