Some type of logger or sniffer exists for almost every form of electronic communication. Your keystrokes, phone conversations, and wireless networks could all be monitored. In this awesome proof-of-concept project, [James] expanded that array to include garage door openers. After receiving a piece of chain mail which stated that criminals have the technology to record any remote code and play it back, [James] wondered if he could build such a device that would work on at least his opener model.

[James] started off with a trip to the hardware store. He was unable to find both a transceiver that worked on the frequency of his remote control (308MHz clocked MAX7042 chip), so at least for this incarnation (he plans to build another one that is capable of replaying a captured signal), only a receiver was implemented. The receiver was connected to a logic analyzer in order to determine its protocol. Since the signal coming from the receiver was very low, [James] had to amplify it through a buffer before it could be detected.

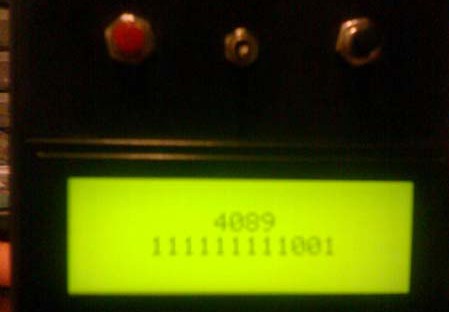
An ATtiny26 and a 4 line x 20 character backlit LCD were used to interpret and display info from the receiver. [James] built the sniffer around a custom PCB (though he ran into a few layout errors that he had to fix post-production). All of the firmware was written in C. It is fairly straightforward, but takes up 98% of the microcontroller’s memory. The program is designed to monitor pin change interrupts and timers to filter out invalid codes as well as noise. Any info (the door codes that have been sniffed) is displayed through a 4-bit interface on the LCD, for easy recording. With the codes, one can configure another garage remote to open the door. If you have any suggestions for V2, We’re sure [James] will be reading the comments.

Update: The code and PCB files (with the error) are available through one of the following mirrors:
filesavr.com/codegrabber
filefactory.com/file/a0eb0gg/n/code_grabber_zip
filedropper.com/codegrabber_1
mediafire.com/?sharekey=7c4692dd4f3ad2c36e7203eb87368129e04e75f6e8ebb871
















ironic, a peace of mail sent out to warn people about there security makes them less secure. this is still a coll project though, and i got the first post!
lol security tip. don’t send emails saying what can be done…
btw nice job
Looks pretty good! Whats the distance on this? I think v4 needs a built in transmitter!
Especially a transmitter and a program to resend the signal 1-3 seconds after recived. Watch people in thier own driveways as thier door yo yos.
A grand majority of modern garage door openers from the last 20 years implement a rolling code security measure. This will never give you the same code twice. It’s highly unlikely that you will be able to predict the next code in the sequence without massively reverse engineering the opener.
Just saying.
While this is a neat project, Doc Oct has a valid point – even though you can grab the code, the majority of garage door openers use the rolling code. Playing back the same code would be pointless as the opener will have already moved onto the next random sequence, and the odds of the same code coming up again are slim to none.
It would be nice if you could have slots for different codes. So if you have more then one opener (one for the gate, the garage, the office) you can record more then one code and ditch 3 remotes for 1
Most garages are built with cladding and siding on just one side of the framework. A battery sawzall gains you entry in about a minute, and can be done from the non-street side to minimize being seen.
//just pointing out that all those security mailings about how their opener uses rolling codes doesn’t add much to the overall security of your garage.
You’d be surprised at how many of those older openers are still out there. Mine was just replaced a few months ago, it used a static 12bit key.
How about spamming all 2^12 possibilities on the various frequencies used by popular openers? The neighbors would love that.
Or depending on make and model, put a 200 watt linear amp on your CB, drive into the neigborhood and key it. Poor RFI filtration means that a lot of older ones just trigger. Play musical doors…
Seems to me like picking the basement door deadbolt is a much faster, reliable, and subtle approach.
It’s scary how cheap a set of decent picks is, and how easy it is to learn to use them.
i wish i was skilled in electronics.
@than
read books/internet resources and find someone to teach u o ya and WANT that wish to come true :)
KeeLOQ is a common rolling-code algorithm used in gate doors and automotive remote-keyless-entry systems that was busted a few years ago. Using a sniffer like this you can get the serial of the fob (which is not encrypted in KeeLOQ) and implement your attack. The “rolling code” is just a counter that is synced at the time the fob is programmed into the receiver, each button press on the fob increments the counter. As long as the counter is within ~16 numbers of the true count it will authenticate you. If you are further out it requires two transmissions with the counter in sequence and then the receiver will resync to you. The keyspace is large enough to make this not a weakness to bruteforce (since you have effectively divided the keyspace by 16). But all that is moot since the encryption used on the counter has been busted in several ways and the algorithm is now published on wikipedia: http://en.wikipedia.org/wiki/KeeLoq
Another thing I should point out is the total lack of publicity about seeing keeloq busted. If your remote-keyless-entry fob for your car says “TRW” on the back then you are vulnerable (Hint: if you drive a Chrysler, Dodge, or several others). Of course, it’s still way easier to smash a window, but this has received no press at all.
I never understood why you would use this for criminal purposes. The people in the house are going to hear the loud ass garage door opening, and if they aren’t home there are much easier ways to get into the house. If you are trying to steal the car then you could just get in and use the opener button on the wall.
You don’t understand it because you’re not a thief.
Burglars are at their most vulnerable when they are actually making entry to the house. Picking a lock takes time and skill, which they don’t have. Breaking a window or door can make noise and attract attention, which can lead to cops or armed neighbors showing up.
Being able to press a button, then drive or walk into the victim’s house and close the garage door behind you with no trace of forced entry is very attractive to a burglar.
In reality, no burglars are going to go to the trouble of building a sniffer to capture codes. They do sometimes use stolen remotes — which is why you should treat a garage door opener the same as the key to your front door. And there have been cases of burglars using brute-force cracking to find the code to a targeted house’s garage door, or just cruising around with a remote and seeing what garages open when they pass.
If you have your remote stolen, or have your garage door mysteriously open on its own when someone drives or walks or bikes past, it would be a very good idea to immediately change the code.
There are a lot — a LOT — of garages and other “locked” doors that still use the non-rolling-code openers.
Knock out the cheap/flimsy plastic window, and pull the chain release hanging nearby…
nice work, but please focus your pictures before sharing them. I strain my eyes enough.
thanks for the related keeloq info dosman.
–PidGin128
@shibathedog
Exactly. This is pretty much just a “because I can” project. Still very cool.
And I thought I was the man for buying another remote control and copying the switch settings over to get two cars into our communal park.
Not saying it was anything special but it made me feel pretty sharp. Till now that is…
I was told by a Linear Corp sales rep that they moved approximately a million units a month of their 10 bit non rolling code transmitters.
There is much value in hacking those since they are used in nearly 90% of all residential automatic gate operating systems. There has been no effort in moving to a more secure product. Even higher security access control systems still do not implement any sort of rolling code. (DoorKing Microclik, Linear Megacode, etc.) Many people who live in gated communities have a false sense of security. This exercise has great relevance, even today.
Why use this to break into a house?
If you walk up to a house and hit (what appears to be a garage door opener) the neighbors will probably just assume that you are friends of the people who lived there. As long as the residents are out people probably wont even care.
or if you want to get a little more advanced… http://www.dealextreme.com/details.dx/sku.28717
Now this is a hack in the true sense of the word. Well done Hackaday for putting this up and well done to James for this extraordinary bit of kit.
Good hack, even if it outdated it show a lot of really useful info for RF sniffing / decoding
@dosman
KeeLoq being “broken” does not entirely mean that it is insecure.
For the rolling codes used in rke for key fobs and garage door openers, there are three valid attacks: First, a side-channel attack which requires physical access and works mostly on pre-1996 devices. Second, a birthday paradox-based attack to attempt to guess the correct slot for the rolling codes (works relatively well as the code space is ~64K, and with a valid code window of 16 we AT MAX have to try ~4K codes). Third, jam the signal to prevent the car from locking. None of these are really that fantastic of a break.
In any of these cases, that is alot of work to do when a good-sized rock through the window will get you into the car just as effectively.
The real break has to do with STEALING cars. For almost all cars manufactured in the last decade, the keys have a tiny .5″x.25″x.1″ rfid-type micro in them. The car sends this micro a random 32-bit plaintext and the micro responds with a 32-bit cyphertext, if the cyphertext is valid, the immobilizer releases. The break occurs if a third party sends the micro 65536 plaintexts and receives the resulting cyphers back (takes ~1hr). Then, using a cluster it is usually possible to get the encryption key from this (you have a ~65% chance of success). Additionally, some manufactures obtain the encryption key from combining a model-specific manufacturer’s code with the serial # from the key (the micro will give the serial # up if you ask it). If this is the case for the key you cracked, then you can obtain the manufacturer’s code, and get the encryption key for all other cars of this model just by asking the micro what its serial # is. Once you are around the immobilizer, you now need a way to start the car (photographic reproduction of a key, bump keys, hot-wiring the ignition, etc). Note – this method works for some rki systems as well.
I actually wanted to add transmit capability but there just wasn’t enough room on the chip so I had to remove it. I’m busy with v2 based on the atmega88 which has a number of extra features including saving codes etc.
I’m also gonna try my hand at rolling code systems and whatever else I can find, these are the most common here so that’s why I started with them.
For anyone interested in the keeyloq hack check out the ccc conference from last year, it’s a pretty entertaining watch.
Speech overview:
http://events.ccc.de/congress/2008/Fahrplan/events/3030.en.html
Conference Recordings (#3030):
http://events.ccc.de/congress/2008/wiki/Conference_Recordings
Nice project, neat setup, but not hardly new. KeeLoq was busted a while back. Here’s the decoding datasheet on it: http://www.keeloq.boom.ru/decryption.pdf
@Zendu: That could be a very useful approach to this->”The most devastating practical consequence of the side-channel analysis is an attack in which keys can be cloned by intercepting only two messages sent by the legitimate key from a distance of up to 100 metres (330 ft).”
@Dave0:
Certain vehicles, like many Chrysler/Dodges, have a system to record and playback 3 different garage door opener codes. The system is called HomeLink (homelink.com).
hello
i need more information for this device
Not much more I can tell you, the code was done in AVRStudio and the schematic and layout in kicad, I used a standard garage door receiver that receives a 12 bit code, the receiver has active low logic levels. Rest you can get from the code and schematic.
Wonderful job. I am unable resist my myself from praising your work. Its among the results of creativity. It educated even me. Now onwards I will keep on observing this blog for such valuable information.
Nice I’am a Repo man in colorado need info for scanner R.F transmitter/scanner code grabber for fixed 12 pin security gates. Would love some other type of application for rolling algorithm’s. taw22576@yahoo.com
Or where or how can I build one or buy one. I’ve also heard of people clonning smart key R.F signals for the vehicles that don’t use a key only a R.F transmitter key fob. Any info would love to hear back will always make my job easier.
Please contact me, I have something to propose you :)
I was reading a doorking manual and it seemed to me that the remotes for gate entry had to have their five digit code entered into the system and then receive their code to open the gate. This sounded to me like a wireless router where you can enter the device MAC address. Wouldn’t this make the sniffed code unusable as you wouldn’t have the correct device number?
Anyone know where to get the source files? The links are dead
The point of being able to pull off an intrusion like this is that you can really screw someone. Because if there is no sign of forced entry then there is no guarantee that the victims insurance will pay for the theft. Its the same issue that came up when bumpp keys first became prevalent. It screws the person twice because they lose their stuff and then have to pay to replace it ;)
I have a security gate opener in my possession that opens the common access gate for apartment complex. The one in my possession belongs to my room mate, and I simply want to dupe it so I can have one too. The homeowners association wants $275 for a new one, fuck that.
When I open it up and look at the wafer its very simple, but must be using a fixed code as there are no bit switches or interface ports. The plastic case says 418 MHz, the name of the company that issued it, and a sticker with a serial number AND a number marked ‘Code:’. I’d greatly appreciate advice, it sounds like the people posting here would know. Thank you!
I not have the patience to build one and was wondering if anyone in so cal would be willing to build and sell me one… please let me know.
Would you be kind enough to let me know where one might be able to purchase a MC16F871-I/P, that has been programmed for a U.S. Automatic Patriot Control Board, Gate opener.
The company will only sell a complete board.
I’m an old Vietnam Vet and refuse to go down without a fight.
I have worked on RF4C planes, so a gate opener is no challege. The only but, is the PIC chip being programed.
Any help would be greatly appreciated.
If you’re not totally confused, you’re not thinking clearly.
All the best, Alex
Hello, if there is french who see this, i have the same electronics device:
http://www.electronika.fr/blog/?p=913
It can copy code of camé, beninca…. and other 12bits remote with fixe code. It can scan all the 4096 code and it can re send the code who you want. It is do whith 16f877A microchip and programmed in C with css.
How can I get this device or where can i buy it?
i want one
There’s a very simple way around this that works well for me. In areas with a high concentration of garage doors like gated communities, condos, or dense residential neighborhoods just take a trip to the closest home improvement store. Usually there are only a few brands of openers on the shelf like craftsman or genie. You can buy one or just the remote and then have fun. Neighborhoods that are 15-20 years old have had the majority of their openers changed out and a high percentage of people just go to the closest place to get one. Just point and click the remote and you’d be s uprising with how many actually open after a few presses of the button. This has worked consistently in several neighborhoods for me…. as for call box gates, good old DTMF tone are still out there, dial a random number from the list, keep the person on the line and then play back the tones with your phone……. open sesame.
This comment is filled with a lack of knowledge and straight BS.
Buying a genie remote wont open a single genie garage. Genie uses rolling code. Your off the shelf genie remote has a seed number of say 1. The neighbors garages may have a seed number of 50,000. When you pair the remote to your garage you are literally syncing the seed number which goes into the rest of the crypto computation.
In no way shape or form would buying a remote open anyone’s garage without pairing.