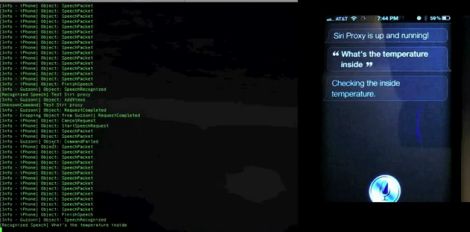
[Pete] has an iPhone 4s and loves Siri, but he wishes she had some more baked-in capabilities. While the application is technically still in beta and will likely be updated in the near future, [Pete] wanted more functionality now.
Since Apple isn’t known for their open architecture, he had to get creative. Knowing how Siri’s commands are relayed to Apple thanks to the folks at Applidium, he put together a proxy server that allows him to intercept and work with the data.
The hack is pretty slick, and doesn’t even require a jailbreak. A bit of DNS and SSL trickery is used to direct Siri’s WiFi traffic through his server, which then relays the commands to Apple’s servers for processing. On the return trip, his server interprets the data, looking for custom commands he has defined.
In the video below, he gives a brief overview of the system, then spends some time showing how he can use Siri to control his WiFi enabled thermostat. While the process only works while Siri is connected to his home network via WiFi, it’s still pretty awesome.
[youtube=http://www.youtube.com/watch?v=AN6wy0keQqo&w=470]
















This is pretty awesome.. too bad it requires having to have it running under a proxy rather than just editing an XML file or something.
I wonder…. If your able to man-in-the-middle siri servers like that. I wonder how hard it would be to trick the servers into using the IRIS port of Siri using a thin layer..
The Applidium guys managed to make a request from their laptop, so that’s perfectly possible. You still need a valid iPhone/iPad UUID to connect, though.
It would be really cool if you could cut out the phone and have the proxy just fake it, becoming a DIY Siri-enabled device. The “proxy” server at this point could pretend to be an apple device itself and could receive voice data from anything else you build, and return the results. In theory, any sufficiently powerful device might be able to do this, meaning you could build this into projects and carry it with you, rather than rely on a server back at home.
this website need to start working
Pretty cool. All you need now is WiFi control over the fridge, lights, and maybe some more ;)
Very awesome. I’d love “Siri” to be on all my devices.
Right now on my laptop I’m using the Mac’s “speech recognition” tool (which should be updated to Siri).
trick ssl without jailbreak ?!!
You don’t need a jailbreak to install your own root CA cert, although you do need physical access.
Does it mean, that anyone who have an access to hosts relaying Siri’s communication with Apple servers can “read” what I have said (e.g. boss, wife, ISP) ??
No! They need to manually, physically install a root certificate in your phone, or Siri won’t accept the proxy’s certificate and fail to connect. This is NOT a security hole.
Please read step 2 in the “Setup Instructions”.
Pretty cool. But makes me worry about implementing this.
How soon before Apple puts out an update to the Siri protocol and breaks this thing?
its SpeakToIt hacking time :D
(i just want siri to my android)
So, in other words, anyone running a WAP can spy on your conversation with Siri? Thanks Apple!
Between you and Olek, the lack of actually taking the time to read the guy’s site makes me want to cry.
Yes, anyone with a WAP can spy on my SIRI conversation, providing they jigger with DNS AND if I happen to install the self-signed SSL cert they have created on my phone ahead of time.
Seriously people RTFA.
If you connect to my WAP, I can see every single bit you send. This has nothing to do with Apple.
No! Siri checks to see if the proxy has a valid certificate for the server. The only way they can bypass it is because they manually, physically installed a root certificate they control on the phone.
Unless you physically give your phone to some stranger, the HTTPS connection will fail and Siri won’t be able to connect.
I feel your frustration dude! I think these guys are only here for the videos, not sure they are actually able to read a blog.
Where are all the cool android hacks?
And as the previous commentor said, where is a hack for Speak to It assistant?
Dude… yeah… pretty FREAKING cool if you ask me. Great job on this! Thank you for sharing your progress.
I have a voice automated house and I was pissed I had to run mics everywhere so I could just talk in every room. This is EXACTLY what I need. Thanks man! Great work!
You could totally run Juniper pulse vpn on the iPhone and access from anywhere via 3g/vpn would be very cool! Awesome Job!
might not require jailbreak but may require udid registration as part of the $99 developer kit.
Still work?