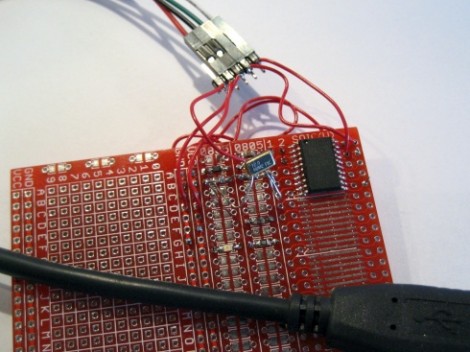
Mircrochip has a new USB to Serial converter available called the MCP2200. [Sjaak] suspected that it may have been made from an existing 20-pin PIC and found that reading the device signature with the PICKIT3 shows that the chip is an 18F14K50. Most likely this is running Microchip’s USB stack but it’s hard to tell because chip is code-protected, reading back all zeros. So he set out to write some replacement firmware which would provide the same functionality and give you access to the rest of the chip’s features.
There were some speed bumps along the way. The first one is that Microchip’s licensing for their USB stack won’t allow you to open source your firmware. That’s okay, it seems there is already a USB stack that can be ported which doesn’t have this restriction. The second wrinkle in the plan is that [Sjaak’s] code doesn’t come with a VID/PID pair that you can use like V-USB does for AVR chips. But that doesn’t diminish the accomplishment of getting the device to work by echoing back characters it receives. Full USB to serial support with the replacement firmware is on the way.
[Thanks Chris]
















would it be legal for someone to sell these hacked chips?
Unless you sign some disclosure agreement upon buying the dongle(?), you own it and they can not stop you from using it at your behest. This may be a different story if you buy the chip OEM.
This is pointless. The chip is infact just a programmed PIC18. Microchip sells these chips for 10 cents more than they would the unprogrammed PIC18 equivalent. The customer is paying for the ease of mind that comes with production volume firmware. While I’m sure the person doing this reverse engineering is learning alot, he/she’s work is technically useless.
In fact, MCP2200 is a little bit cheaper than PIC18F14K50 which might suggest that slightly defective PICs might be used to “produce” these USB converters. For example devices that do not meet some analog specs etc.
@realEngineer
This time I can’t help but saying the same thing…
Mircrochip ?? It is the first word in the post! lol
#corrections
@realengineer: in fact the MCP2200 is 0.33$ cheaper then the real PIC. (1.75U$ for the MCP2200 and 3.08U$ for the 18F14K50, single qty. at mouser).
As for most hacks they are useless and more for fun and a ‘just because I can’ factor. Instead of flashing it with just a blinking led (it has this as a bonus) we decided to port the experimental stack written by Honken to it.
Also, this isn’t useless, if, say, you find that there is a product with one of these in it that you want to hack.
You could, for example, program it to behave normally, but also have some extra features. Might be cool.
@biozz
Nothing stopping you from buying them and reselling them as reflashed MCP2200s so long as you’re clear about what they are.
What you can’t do and it is probably uneconomical to do anyway even with the slight discount is buy MCP2200s, erase them, grind the top clean of any markings and then reprint them as regular PIC 18F14K50s. The internals may be a 18F14K50 but Microchip don’t validate them to be sold as such.
This is an interesting discovery! However the chip has, most likely, faulty peripherals. So, if you’re expecting to have a fully featured 18f14k50 for less money, just remember that if your ADC doesn’t work as expected, it’s not Microchip’s fault… It was already faulty from factory ;)
Yikes! That’s actually a pretty scary security hole on Microchip’s part… I would be afraid to use these in any self-respecting product now.
If they’re going to recycle a general purpose uC, they should have blown the programming fuses after putting the firmware in it. It’s now possible for some malicious third party (distributor, vendor, neighbor-that-you-let-borrow-your-thingy) to superstitiously alter the software in what should be a completely walled-off black box to do only God-knows what! If, for example, this went in a USB keyboard, the chip could store keystrokes. A special key combo could then order it to spit them back out. Much much more nefarious scenarios could be devised depending on the specific device.
Bad, bad Microchip!
A great number of devices have firmware uploaded on connection i.e wifi interfaces… some stuff has firmware in flasm rom you can get access to with basic tools.. your ship has sealed
@Charper
Really? So your neighbor/vendor/etc is gonna borrow your keyboard, hack the firmware on the USB chip, give it back, then borrow it again and repeat a keystroke to keylog you? How paranoid are you?
This is standard business practice. Limit the functionality of a device by programing it (making it easier to use) and sell it cheaper because of the limitations. I don’t see what the big deal is. I get that the slightly cheaper chip can be re-purposed for the same use as the PIC, but can someone fill me in on why that’s awesome?
Don’t misread, I do think reverse engineering is great and it’s wonderful to suspect this from MCP, but I don’t see the ‘unlocking’ part to be amazing.
Charper,
You’re on the right track. It doesn’t really matter if they blew the fuses on the PIC. Reconstructing the code for this chip isn’t a daunting task. With a new PIC soldered in place of the old one containing some additional malicious code it would be nearly impossible for a consumer to ever know their uC was replaced.
There are easier exploits but this could tie in well for a various sophisticated attacks.
@Spork
I said I wouldn’t want to use this in a product I made.
Ok. So flip that scenario around. Say you are selling USB keyboards with this chip in it. Some company buys them and installs them on all their computers. An employee of that company reads this article, and turns a few keyboards into keyloggers. There’s no hardware modifications to be found anywhere, no solder connections, no hardware dongles, nothing. Your reputation as a manufacturer would be scarred at best and you’d find yourself in the middle of a big lawsuit at worst.
Also note that the keyb sniffer was just a quick example. I’m sure there are other nefarious uses.
@ Charper. One, you would have to solder to it to reprogram it. Two, physical intrusion stickers/warranty void if open labels to detect things like this. Three, tons of companies use off the shelf pics and cypress and amtel chips in their products. Now a days they are just the cob instead of dip or smd versions. And as a manufacturer, with contracts with Microchip, any tampering on a large enough scale like that that would lead to a lawsuit, one can be sent to Microchip to verify the code on it.
Has someone recently been watching that old Tom Selleck film Runaway? where robots go crazy because someone installed a rogue chip in them.
@Charper
The paragraphs under my response were not to you, they should have been above.
The subversive chip replacement is highly unlikely to happen in this case. Remember, it’s just a USB to RS232 converter: it’s not going to be in a keyboard.
Now, I happen to know that a lot of USB Logitech keyboards did in fact use a reprogrammable or replaceable HC08 USB microcontroller. So if you wanted to worry about in-keyboard undetectable hacks, you should have started about 8 years ago.
@charper: “superstitiously alter the software”
Wow! That must be a new technique I’m not familiar with…
…although I think you meant “surreptitious” ;-)
“An employee of that company reads this article, and turns a few keyboards into keyloggers.”
News flash, people that work at those companies are smarter than the people here. They knew this stuff a year ago.
If you are worried about a chip that would never end up in a keyboard (usb to rs232… do you know how keyboards even work?) then I better not tell you how easy it is to modify a computer’s bios to do the same thing without you knowing it.
Very nice hack, just be sure that the other chip peripherals are fully functioning.
Some vendors sell partially defective chips by repurposing them to use the peripherals that work then masking or disabling the ones that don’t.
Many X GHz computer CPUs, for example, come from X+Y GHz lots where the units proved to be functional only at lower clock frequencies, therefore instead of trashing them , the vendor sells then relabeled at the right frequency.
heh @qwerty one of my friends unlocked a broken X3 and revived the 4th “bad” core, then overclocked it to 4 GHz with water cooling.
Amazingly it works perfectly, he thrashed the hell out of it and not so much as a blip.
Thanks AMD!
(wonders if the bad cores in the Cell chips on the PS3 can be hacked in the same way!)
for some applications even a broken core with say one instruction yielding a bad result can be worked around with creative coding.
even better, the “bad” cores might only be unstable above certain temperatures, so if you know which instructions break you could feed back current temperature to adaptive code which switches the instructions to a good core in realtime.
(scuttles off to try this!)
-ZPM
@zeropointmodule
The hard part is that its difficult to determine what exactly is defective. The exact trigger for the flaws might be only under certain conditions like the other cores are running a specific miax of instructions and you’re trying to run X on the reactivated core and your previous instruction was Y.
The CPU manufacturers know how to test all parts of the CPU and will have the necessary tools and equipment to do so. Thats not easy to replicate at home.
Just have a look at the published errata for the x86 CPUs and you’ll see some really esoteric bugs along with some really bad ones which are just worked around by the OS.