[Mike] sent in a tip about Newstweek, and we’re turning to our readers to tell us if this is real or if we’re being trolled. The link he sent us points to a well-written news-ish article about a device that plugs into the wall near an open WiFi hotspot and performs something of a man-in-the-middle attack on devices connected to the access point. The article describes the device above as it observes, then spoofs the ARP table of the wireless network in order to inject fake news stories in pages you are reading. Apparently once it boots, the small box phones home for commands from its maker over a TOR connection.
The box reminds us of the Sheevaplug so it’s not the hardware that makes us question the possibility of the device. But look at the Linux terminal screen readout. It shows a prompt with the word ‘newstweek’ in it. That’s the address of the site the article is hosted on, giving us a strong sense of being trolled.
What do you think, real or fake? Let us know (and why you think that) in the comments.















http://vagueterrain.net/content/2011/01/newstweek-network-permeability-and-headline-hacking
I’d say it’s real. Look at the pineapple that Darren Kitchen over at Hak5 created. essentially this is the same thing but taking it a step further.
off topic, making an automated wifi sniffer to leave at coffy shops and alike to sniff out “useful” info could be both an issue and pritty effective, not sure how many people use credit card details or paypal while at random wifi’s but more than enough people check there emails and throw in personal info
Look at all of the sheep that gather in public places like coffee shops and attach to an SSID named “FREE WIFI” connection that does the exact same thing.
It’s a device by two artists. (1 minute via google) But it actually works. Heared about it at CCC conference last year.
http://blogs.computerworld.com/17820/hackers_use_hidden_device_to_manipulate_news_at_wi_fi_hotspots
Real, newstweek might have been injected into it, or what ever >_> But they know who made them
Looks legit to me – judging from the link egasimus already posted and another one ( http://www.imperica.com/features/newstweek ) it seems like it’s an art project – and a pretty complex and well-executed one, too.
Seems plausible, I did something similar to a workmate who always checked the stock market instead of working. I whipped up a program to perform an ARP man in the middle, DNS spoofing and started modifying his stock ticker info :) The numbers were wildly incorrect so he was not going to act on them.
The article is a artistic fabrication for sure, but the device itself is probably real.
The article has way too much technical information to be a real news article. The ‘security expert’ mentioned in the article, Zdzislaw Kotla, is actually a Polish Olympic sailor. The links on the top banner are all useless. The pictures at the end of the article link to the authors’ homepages. The last line is pretty funny: “Note the black hat worn by what may be a colleague in the first photograph.”
Feasible, but this story is probably part of someone’s college project on media manipulation.
Just take a look at
http://blogs.computerworld.com/17820/hackers_use_hidden_device_to_manipulate_news_at_wi_fi_hotspots
registrant-firstname: Howard
registrant-lastname: Lester
registrant-organization: A.J. Lester & Associates, Inc.
registrant-street1: 9898 Bissonnet ST
registrant-street2: Suite 678
registrant-pcode: 77036
registrant-state: TX
registrant-city: Houston
registrant-ccode: US
registrant-phone: +1.7132704277
registrant-email: callmehowie@hotmail.com
Focussing on the site itself;
1. None of their “most popular” stories show any hits in a Google search (actually, none of their stories have).
2. I cannot find any other stories on the site as the headlines are not links (neither are the “Subscribe”, facebook or twitter links).
3. The images in the article are stock photos (despite one being captioned to imply the woman in the picture is the woman in the story)
4. I haven’t seen this story on any other sites.
5. there is a link at the bottom of the page to JulianOlivier.com (in the copyright list, labeled “Oliver”). A few co-incidences arise on there.
Based solely on the site reporting it, I call troll.
I can’t comment on the technical aspect of the device as I don’t know enough about this sort of thing.
Of course an SBC in a AC box can do it, why it would use TOR to connect to the MC, or how that even remotely hides MC, is anyones guess…
Also most APs have ARP checksums these day..
On watching the video;
1. The “device” is referred to as the “Newstweek device”
2. The presenter uses an N900 phone for the demonstration. The same model was reported as handed into a police station in the article.
Yes it is real.
The beauty of the internet is that every position is absolutely equal to the next.. Every hop retransmits data. This retransmission has the potential ability to modify the data it receives. Because of this, the “Backbone” creates a hierarchy.
If you’d like to recreate a ARP redirection, download a program on your Android telephone called “Shark for Root”. It performs an ARP Spoofing where every time someone requests “who is the router”, your phone will say “I’m the router”… All data goes through your phone and is logged. The data is then retransmitted to the Router and noone is the wiser.
Now, This is a simple spoof. It is used for diagnostic purposes. When you want to find out about problems on networks, you use a protocol analyzer with ARP spoofing capabilities. It allows you to look at the packets being sent and see what’s causing the problems you are experiencing.
If you take this diagnostic process one step further… As data is received, it can be modified before it is sent out. This is a man-in-the-middle attack. It is not a high-tech or hard to recreate process. It’s a matter of working with data at a low level of the OSI model.
If you’d like to make your own man-in-the-middle.. Get a small ARM computer, like a Android phone, get linux up and running, then find a way to compile Ettercap onto it. All data received by Ettercap can be changed and modified. Also, look up dnsspoof, webmitm fragrouter and ssldump.
If you want to go a bit bigger, you can install Backtrack onto a small i386 nettop computer and it has all the tools you need. Set up the backtrack computer as a firewall on your network and let it rock’n’roll.
Has anybody tried scanning the barcode on the screwdriver?
Remembers me of that guy who had a open wireless network where he installed a transparent web proxy that would replace all (or some) images on any web page with images from some cats web site, which then got complains of people that said they hacked their computer. Hilarious! Cannot find the URL right now, though.
I’d say it’s real. Clicking the “read more” link takes you here: http://newstweek.com/2011-01-07-device-distorts-news-on-wireless-neworks
Where at the bottom of the page, links to http://selectparks.net/~julian/ and http://k0a1a.net/ can be found. Both appear to be artists dealing the the realm of the crossover of art an technology.
The damning evidence appears on one of the above sites: http://k0a1a.net/redbox/
awesome idea! however the picture looks fake.
no DC power supply.
220 VAC != 3.3/5 VDC
A bit of poking around on the newstweak site reveals the following URLs:
http://www.imperica.com/features/newstweek
http://blogs.computerworld.com/17820/hackers_use_hidden_device_to_manipulate_news_at_wi_fi_hotspots
So, this incarnation of this gadget is “art,” but it has real implications. This has been going on as long as there’ve been hot spots.
The potential for monitoring of those in the cafe (or wherever) is a big deal, but the reverse risk (of a remote attacker being able to appear to be anywhere) is a big deal too. Now you can’t trust the logs of what you saw. For all you know I was half way across the world when I published that tweet or facebook message from the cafe across the street.
Whether or not this device is legit or not, it *is* possible to pull off. To pull it off, not only would you need the website to not be using SSL, but you’d need an HTTP server running, plus a way to re-format incoming pages on-the-fly. Regardless, with something like a Sheevaplug, I could see it being possible.
I call shenanigans…look at the top image on that site where they clearly show a picture of “newsweek” magazine with this device on te cover…pretty poor photochopping.
http://newstweek.com/?2011-01-07-device-distorts-news-on-wireless-neworks.head.129503152513
and look at some of the “headlines” on some of te side articles…12000 year old bong found in space junk….yeah
who knows if the device is real, however, the website is so rogue. Not even the fake links at the bottom of the page work and the main domain is about the same news all over. So rogue and fake.
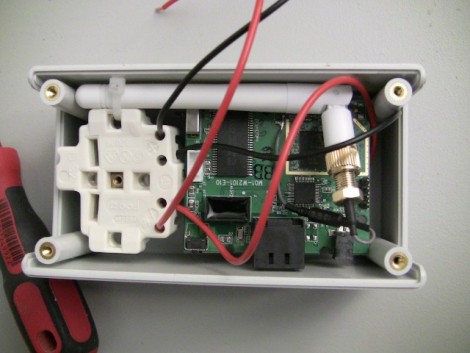
Yes this is an Abocom WAP2101 (Board number M01-W2101-E10 as per photo) – Google it for the product spreadsheet, top of the list of results.
Useful info can be also found here detailing the wireless chipset, OpenWRT compatibility etc (http://translate.google.co.uk/translate?hl=en&sl=ja&u=http://mizupc8.bio.mie-u.ac.jp/pukiwiki/%3FPlanex/GW-MF54G2&ei=W-9fTfC-CMPJswb_34y2CA&sa=X&oi=translate&ct=result&resnum=1&sqi=2&ved=0CB0Q7gEwAA&prev=/search%3Fq%3DM01-W2101-E10%26hl%3Den%26prmd%3Divns)
It has an atheros chipset, and so would be compatible with Karma and Jasager (http://www.digininja.org/jasager/) as was demonstrated on hak5 as Chris Muncy correctly mentioned and so there is a great possibility it is real!
I don’t understand the need for a device to ‘lie about the news.’
If you are talking about the media in this country, they quit any semblance of reporting ‘truth’ decades ago
Seriously? The site is obviously satire. There is an article about an outer space bong and yet you still question if is it ligit?
The device is most likely very real.
http://blogs.computerworld.com/17820/hackers_use_hidden_device_to_manipulate_news_at_wi_fi_hotspots
http://www.imperica.com/features/newstweek
Newstweek.com is their site where they advertise this device.
Never ever use hotspots.
This seems to me more like an art project or “prove of concept” to remind people not to believe every that they may read on the internet – by showing how easy it is to manipulate information. My guess: the device is real, the story behind it is not.
I think it is a Fake, you can only see 1 antenna on the device, but you need two because you need at least 2 network endpoints to be the man in the middle.
OK so if i read the page right. it injects or changes news? As far as making changes to a page, what good is this even if it were true? A random person looks at a random news page and see something not real. if he forwards it to a friend the friend is going to see the real story (unless the link changes also) and most people will Look at multiple sources of news for the “full story” thus any misinformation would stand out. This being the case it is a lot of work for iffy results.
On the other hand if it were placed there by someone (cia, kgb, police, others)to funnel targeted information to a targeted person who was known to come often to an establishment (we are creatures of habit) then it might be useful and true.
As for a wi-fi snoop .. all bets are off. I am sure if it is real it dose just that alone.
What is the point in making a real one if you can create your own false news stories about… using a device that changes news stories.
If this is real, and I’m guessing it’s not, it’s probably some kind of art piece/social commentary project.
Look into ettercap filters. This should be possible on any linux device with a wifi card. The card wouldn’t even need to support injection. It would even work over SSL, but the targets would get invalid certificate warnings that they would most likely ignore anyway. As far as modern routers having ARP table checksums like xorpunk mentioned, you’d be surprised how many modern routers this works on. A lot of new routers may have this feature, but I come across one yet.
I recognize the right-hand image at the bottom from this news story:
http://www.winnipegfreepress.com/canada/old-man-mask-used-to-get-into-canada-refugee-claim-made-upon-arrival-106814793.html
They swapped it for the rubick’s cube head guy?
@Adam, uh, Shark does no such thing. All Shark is is a frontend gui for tcpdump.
And this is like a Fonera running Pineapple, or Upsidedownternet. Funny, probably true, or if not, proof of concept.
Wait… having a host name related to the project, and displaying it in the prompt when connected to a shell there gives a strong sense of trolling? Have you guys ever actually USED Linux?
Is it possible to do this? Sure, but to work wirelessly most setups would need two wireless cards: one to listen and the other to broadcast the fake data. When I tried 802.11 hackery, most wireless chips would not allow you to send packets while they were in monitor mode listening to other devices that were not connected. On an unencrypted network, one wireless port listens for a request for a news site, the device crafts a packet to mimic what the AP should respond with, and broadcasts that packet over the second wireless port. Since this device doesn’t have the latency of a remote server, it gets to respond before the actual news.com server can, and the real reply looks like an echo.
But that website, with all it’s stock photos, looks pretty fishy to me.
Obviously a fake, if you check around in the newstweek website everything is fake except this article, if you follow the links and checkout the names you’ll discover that it’s two artists behind this site.
Yes, it’s possible. No the article (and possible device) is fake.
Site’s obviously bollocks but their tech looks pretty legit to me. Check out this video: http://www.youtube.com/watch?v=xL5ljrNInpM
It’s all there lads.
device is clearly real, so trivial to build it’s not even funny. website is a parody, if that’s not obvious upon reading it then the reader is a sucker. it’s another proof of concept that is getting good press because they have a good pr instinct.
@Quin, most wireless cards won’t, but embedded controllers will. Having Dual APs is a standard feature on those pocket routers (Look at Fonera or DDWRT), and it does it by interleaving the data.
@NatureTM: have you seen most browsers’ invalid cert pages? It’s like it’s warning you about the imminent end of the world.
SSLstrip would be much cleaner; they would simply get an HTTP version of the site.
So the point is to inject fake news stories into real news feeds. The fake news is, presumably, retrieved from the newstweek website. Yet some figure the project is fake because the news from the newstweek site is fake?
Interesting.
If it is real then it probably only works on feeds from one site (Newsweek) or at least a limited number. Programming a device and doing individual injections for a variety of sites would be a great pain the ass. The device probably isn’t specifically made for doing such things, but rather remote network injection. The author probably just wanted an interesting hook on their story, and probably only did this once as a proof of concept, or worse, a joke.
too bad this website doesn’t know the difference between new and knew…
It looks to be a real device. Probably a sheevaplug that has been repackaged with BusyBox Linux. Then using arp-spoofing like many of the hotels do. The can create their own news stories. Don’t know if this a proof-of-concept device but it has all the makings of a real item.
The antenna exhibits poor engineering. I question whether it would even present an acceptable swr to the transceiver. To perform within typical expectations it would need to be attached to a metal chassis, plate, or at least some counterpoise. If it works then range is less than expected.
If such a thing doesn’t exist, that just means we should build them. If it does, we should build more ;-).
I did a proof of concept to demonstrate the creation of disinfo articles that somewhat resemble the real thing, automatically, based on existing news feeds: http://namcub.accela-labs.com/stories/googleed.html http://namcub.accela-labs.com/stories/boinged.html
The above is the result of the original source piped through a sequence of sed commands. In other words, it’s so trivial your dead grandmother could write it.
@IceBrain
Yeah, I’ve seen those. They are pretty intimidating these days. Good point about SSLstrip. The thing is, when a person wants to say check their bank balance over some https site, they see the warning and probably have a little freak out, unplug their router, restart their computer, etc. When none of this stuff works, they usually just say, “f*** it, what could be the harm?” Then they accept the invalid cert, the site loads normally, and they forget about it. A lot of people seem care about security until it becomes a hassle. They disable their AV because it nags them to update. They disable UAC in Windows because it makes them click a button one or two extra times. You can warn people all you want, but if they get a little annoyed, you can usually expect them to do something stupid.