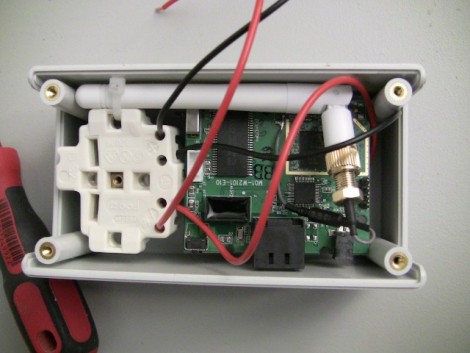
[Mike] sent in a tip about Newstweek, and we’re turning to our readers to tell us if this is real or if we’re being trolled. The link he sent us points to a well-written news-ish article about a device that plugs into the wall near an open WiFi hotspot and performs something of a man-in-the-middle attack on devices connected to the access point. The article describes the device above as it observes, then spoofs the ARP table of the wireless network in order to inject fake news stories in pages you are reading. Apparently once it boots, the small box phones home for commands from its maker over a TOR connection.
The box reminds us of the Sheevaplug so it’s not the hardware that makes us question the possibility of the device. But look at the Linux terminal screen readout. It shows a prompt with the word ‘newstweek’ in it. That’s the address of the site the article is hosted on, giving us a strong sense of being trolled.
What do you think, real or fake? Let us know (and why you think that) in the comments.