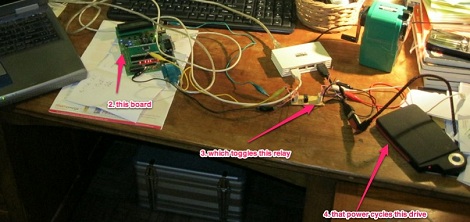
While at work one day, [Marco] was approached by a colleague holding a portable USB hard drive. This hard drive – a Freecom ToughDrive – has a built-in security system requiring a password every time the drive is mounted. Somewhat predictably, the password on this hard drive had been lost, so [Marco] brute forced the password out of this drive.
The Freecom ToughDrive requires a password whenever the drive is plugged in, but only allows 5 attempts before it needs to be power cycled. Entering the passwords was easy to automate, but there was still the issue of unplugging the drive after five failed attempts. [Marco] called upon his friend [Alex] to build a small USB extension cable with a relay inserted into the 5 V line. An easy enough solution after which the only thing needed was the time to crack the password.
The rig successfully guessed the password after 500 attempts, or after cycling the power 100 times. This number is incredibly low for getting a password via brute force, but then again the owner of the hard drive was somewhat predictable as to what passwords they used.















I have thought of that back in the days with IDE laptop drives, and need to power recycle every 3 fail password.
Just not sure if this is any good for the harddrive with constant power up and down.
According to the datasheet for the drive the data is protected by a 256bit password. So an 8 character password at a guess ?
Assuming that the 8 possible password characters are :26 lower, 26 upper, 10 numbers, 33 symbol
(26+26+10+33)^8 = 6 634 204 312 890 625
6 followed by 15 zeroes, my head hurts when thinking about numbers that big. Even after dividing by 5 (for reattempt power cycles) I can not see any hardware surviving that, not even the relay.
Brute force cracking the password after 500 attempts (100 power cycles) says more about the poor choice of password than the designed security of the drive.
EDIT: After reading the full article it says “the production of passwords based on the user’s common password combinations”, so it does not sound like truly pure brute force password cracking either.
But I will admit that having a relay in there does make it brute force in a different and somewhat unexpected way.
It’s a brute force with a carefully crafted dictionary.
Yep, likely not healthy but it worked long enough to mount the drive and copy the data off.
As highlighted in the original article, Alex Schutz put together the rig, as the electronics guy, and actually pushed to get it complete.
Might have been easier to find a way to persuade the laptop to disable VBUS briefly, possibly by removing and reloading the kernel module for the host controller.
maybe you could remove drive’s cover and mount it inside a PC
this^^
+1 on this too
These typically have a small uC handling the interface and “security”, while the drive itself is just a normal drive with a normal file system.
In addition, I believe there was an article about accomplishing the same thing on an OEM HD with a security feature that allowed the contents of the drive to be locked.
It seems that the manufacturer left a serial test and diagnostic interface available on the PCB, and someone easily exploited this to unlock and simply read the contents of the drive, bypassing the mechanism for encryption.
It may have been in HAD previously.
Unless you were not able to open the enclosure to try it, wouldn’t it have been easier on the electronics to tap into a board reset on the uC card? That should have spared the drive the power cycles while resetting the retry counter.
why not just pull the hard drive out of the case and use a separate ide/sata usb hard drive connector device
From what I’ve seen here, it doesn’t appear that the hard drive is insecure, but the password was.
This hack is nothing to write home about. That shit wouldn’t work in a normal scenario. Better off sending fw commands to the drive with MHDD… except in this case you could just pull the drive from the enclosure.