There are thousands upon thousands of papers discussing various aspects of embedded hardware security, and dozens of books covering the same subject. The attacks discussed in the literature are very cool – things like side-channel power analysis and clock glitching used to extract keys from a system. The experimental setups in these papers are extraordinarily expensive – you can buy a new car for less. [coflynn] was disheartened with the price of these tools, and thought building his own would make for a great entry to The Hackaday Prize.
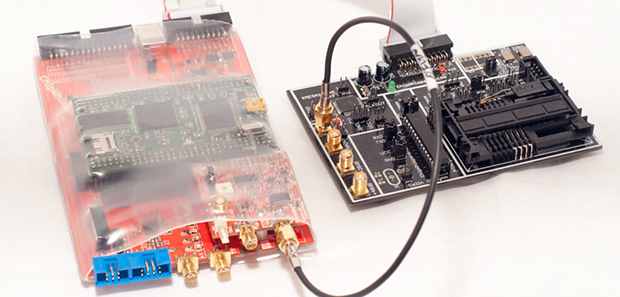
The hardware part of the ChipWhisperer includes a breakout board with an FPGA, ADC, and connectors for a lot of different probes, adapters, breakout boards, and a target board, With all these tools, it’s not unreasonable to say that [coflynn] could carry out a power analysis attack on a lot of embedded hardware.
Open source hardware is just one part of this entry. The biggest focus of this project is the open source software for analyzing whatever the probes and target boards record. With this software, anyone can monitor the power used when a chip runs a cryptographic function, or glitch a clock for some unintended functionality in a device. In keeping with the academic pedigree of all the literature on these attacks, there are a ton of tutorials for the ChipWhisperer for all those budding security researchers out there. Very cool stuff, and arguably one of the most technical entries to The Hackaday Prize.
Video below.
![]() The project featured in this post is an entry in The Hackaday Prize. Build something awesome and win a trip to space or hundreds of other prizes.
The project featured in this post is an entry in The Hackaday Prize. Build something awesome and win a trip to space or hundreds of other prizes.















Boring, I’d rather see some green energy hacks or some cool gadget.
You are useless and contribute nothing to the world.
Want to see something that interests you? Make it, instead of whining like a child.
This *IS* a cool gadget!!!
What is this large grey-black thingy on the target board (on the right)??
looks like a smartcard socket.
Wow, that video was fast!
I recently watched a documentary on YouTube regarding the Cray architecture and within the section on gate coupling there was mention of using differential connections between each gate, to keep a constant power profile during computation. Could this be an answer to this type of attack?
On small geometry, the leakage current can get to 30-50% of power consumption (the rest being the dynamic, I/O etc). So do exact opposite of what the rest of the industry do and skip out on all the fancy stuff to keep out the leakage current small and power management and you got yourself a chip that consumes heaps of power whether it is busy or not.
Not sure if anyone would want such a chip as you can’t implement lots of stuff if you can’t dissipate huge amount of heat from a small area.
ECL is one of the oldest integrated logic families and employs differential signalling–it’s also an analog (non-saturating) logic family, which makes it very fast. On wire-wrapped prototype boards, it’s not unusual to see twisted-pair used for logic signals.
Before ECL, there were other differential signalling logic families.
The best answer to this type of attack that I’ve seen is to write constant time algorithms, i.e. no branch or jump is taken/avoided based on secret information. They use this approach in NaCL, http://nacl.cr.yp.to/
Constant time might be sufficient for webservers etc., i.e., when the response time is the only observable side channel. However, it can counter only basic Simple Power Analysis (SPA) attacks and offers no protection at all against Differential Power Analysis (DPA). Actually, constant time makes DPA much easier (-> trace alignment).
Cool project! Would this stuff work with Red Pitaya/Parallella/AnalogDiscovery etc.?
Cool project and congrats on the kit :) It looks like there are a wide array of attack options and points that can be tested with this device.