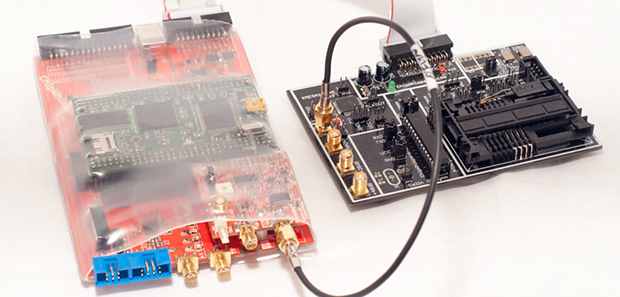
There are thousands upon thousands of papers discussing various aspects of embedded hardware security, and dozens of books covering the same subject. The attacks discussed in the literature are very cool – things like side-channel power analysis and clock glitching used to extract keys from a system. The experimental setups in these papers are extraordinarily expensive – you can buy a new car for less. [coflynn] was disheartened with the price of these tools, and thought building his own would make for a great entry to The Hackaday Prize.
The hardware part of the ChipWhisperer includes a breakout board with an FPGA, ADC, and connectors for a lot of different probes, adapters, breakout boards, and a target board, With all these tools, it’s not unreasonable to say that [coflynn] could carry out a power analysis attack on a lot of embedded hardware.
Open source hardware is just one part of this entry. The biggest focus of this project is the open source software for analyzing whatever the probes and target boards record. With this software, anyone can monitor the power used when a chip runs a cryptographic function, or glitch a clock for some unintended functionality in a device. In keeping with the academic pedigree of all the literature on these attacks, there are a ton of tutorials for the ChipWhisperer for all those budding security researchers out there. Very cool stuff, and arguably one of the most technical entries to The Hackaday Prize.
Video below.
 The project featured in this post is an entry in The Hackaday Prize. Build something awesome and win a trip to space or hundreds of other prizes.
The project featured in this post is an entry in The Hackaday Prize. Build something awesome and win a trip to space or hundreds of other prizes.
Continue reading “THP Entry: Embedded Hardware Security With The ChipWhisperer” →













