Some of our dear readers may already have an infallible system to remember different complex passwords for the different websites they visit daily. This is why they may have not been following the offline password keeper that the Hackaday community is building.
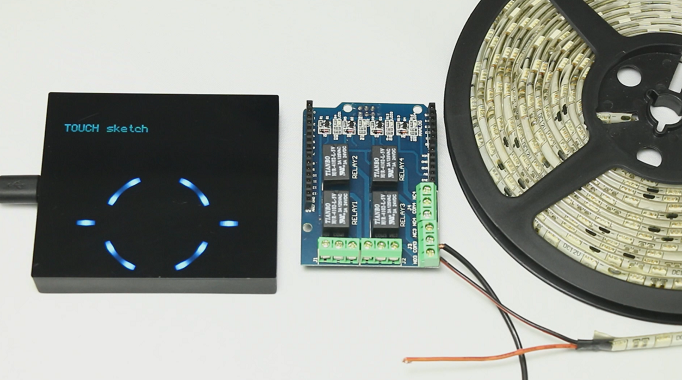
The Mooltipass has a characteristic that may regain their interest: it is possible to connect Arduino shields to it. In the video embedded below you can see the Arduino conversion process our development team imagined a few months back. The operation simply consists in using a knife to remove plastic bits on top of standard Arduino headers. We also embedded a few use cases with their respective sketches that may be downloaded from our official GitHub repository.
As with stacking several shields, a little tweaking may be required to keep the functionalities from both the Mooltipass and the connected shield. We therefore strongly welcome Arduino enthusiasts to let us know what they think of our setup.
In the meantime, you may want to subscribe to our official Google Group to stay informed of the Mooltipass launch date.













Sorry guys but as a security engineer, your device is horrifying.
Are you seriously just storing the key on the card, as I believe from the presentation in your github? Then your device is close to bullshit since the avr device contents can be hacked and observed (to steal the pin, save the key, etc).
The AVR cannot be trusted.
Wake up, DPA/SPA attacks are a reality, running the AES alg on the AVR is a mistake, again, an AVR is NOT a trusted platform.
You have to KEEP the key INSIDE the card, and use card APIs to cipher data, preventing any key read.
Without this feature your security is reduced. You can just avoid costs and store the PIN and key in an I2C EEPROM: just xor the key with the pin digits. Wrong pin means wrong key value.
At the moment, you are using a smart card just like a magstripe card!
I hope the presentation is obsolete and you improved your design.
Hello f4grx,
I wish your feedback was more constructive and polite. The key is actually stored _inside the pin protected_ smartcard. We are therefore _not_ using the card as a magstripe card.
Our device is safe as long as it isn’t torn open (same as your cash machine, smartphone and pretty much every security device out there).
The scenario you offer doesn’t prevent an attacker from sniffing the card unlocking PIN.
We therefore invite you to take a few more moments of your time to have a look at our design, and come in #mooltipass on freenode to discuss this.
We look forward to your constructive feedback :)
Paleeze, Mathieu! Compared to some of your replies to folks who’ve criticized any part of this project, [f4grx] was down-right ghandi-like.
“the Mooltipass is composed of the main device shown above and a smartcard.
On the device are stored your AES-256 encrypted credentials. The smartcard is a read protected EEPROM that needs a PIN code to unlock its contents (AES-256 key + a few websites credentials). As with your credit card, too many tries will permanently lock the smart card.”
Well I’m afraid I have to agree with @f4grx : why do you use a smart card just as a protected eeprom.. ?
I use for my password : Keepass (open source ) + Truecrypt (open source ) + Sdcard on usd + smart card with PKCS certificates.
So it works like that : on the sd card( or a usb memory stick) I created a crypted volume thanks to truecrypt. That volume can only be mounted if the smartcard is inserted and pin code is entered. The pin code only ables you to activate the certificate : it’s more than juste unlocking some data , then the certificate is used by Truecrypt to mount the volume ( the private key NEVER appear in my computer memory as the whole decoding is made on the microcontrolleur of the smartcard). Then access is given keepass to the crypted file inside the crypted volume.
After few minutes or if the smart card is taking off, the volume is unmounted.
Now of course the security problem here is that once the volume is mounted the computer has access to the crypted file on the usbkey(sdcard).
So the best way to do it would be instead to use a usb/sdcard , use a system like yours. So I’m afraid the guy is right when he says the smarcard eeprom seems out of context.
The best of the best way to do it is then to use a raspberry: install truecrypt on it, install smarcard middle driver for your pkcs card ( you can use Myeid smart card for example) and so the whole decoding is made on the smartcard, the keepass job on the raspberry ( isolated from your computer) and then do some code to pass to your computer only selected credentials.
but so you know you can combime data + deciphering engine on same smart card : exemple :
Truecrypt can allow you to mount a little volume thanks to private key on smartcard , and the actual volume can also be ON the same smardcard! you need those with 128k or 256 memory . Also usually on those card you can have multiple certificates / keys / ciphering engine, and space that is unlocked or locked based on special pins.
And then of course you can use famous BASICCARD ( those are use to emulate debit/credit card for ..fun.. ) and programm a whole system on them ( they include ciphering devices). Same goes with some JAVA cards.
All in all. nto meaning any disrespect, but, improving the use of the card could be on your todo list for V2.0
Exactly…you dont need to be a dick and start shooting off things when you obviously do not have all the facts. I hope you dont go around in your daily life like that. You gonna get your ass kicked quite a bit.
Some of our dear readers may already have an infallible system to remember different complex passwords for the different websites they visit daily.
its called a ‘brain’
I admire your brain :).
Me & the beta testers have more than 50 credentials sets. if you choose at least 10 random characters per password that leads to a total of 500… we may be too busy remembering other things!
So, now this could work with a bluetooth shield?
yes, but keep in mind that once the mooltipass i opened you can’t have the guarantee that your fw hasn’t been compromised.
These are 2 distinct working modes.
So the mooltipass lets you attach shields. I assume this means it’s easy to reprogram the mooltipass. How can a user be sure their unit isn’t running compromised FW?
by checking it hasn’t been opened
That is only sufficient protection for the most casual of attackers who are armed with a big screwdriver and/or hammer.
Does this mean that you can’t easily update the firmware in the Mooltipass?
You could make a hole on the side and fill it with resin.
Updates will be allowed using passwords unique to each device in order to prevent firmware tampering.
On a side note, reprogramming the mooltipass using the non-bootloader way will erase some of your data, making it impossible to decrypt your passwords anymore.
Ahh okay. If you’ve got a system for doing user authorised updates then that is much better.
You’re limited by the smartcard since it doesn’t support running programs on it but something that would make it more secure is a zero-knowledge proof as part of the handshake. The card would be able to detect that the Mooltipass has been replaced or tampered with as it wouldn’t pass the ZKP check and it could then refuse to perform any operations. The easiest method is probably for the card to generate the necessary secret when you first initialise it in a Mooltipass. You’ll have to trust that your original Mooltipass hasn’t been tampered with but there is very little you can do to avoid that.
That would be extremely nice indeed.