Back when we started The Hackaday Prize, security, big brother, and the NSA were making headlines every day. Since that time, there has been enough bread and circuses in the news to wipe the consequences of these leaks out of the public consciousness, but work is still being done by hackers and tinkerers the world over to give you the tools to protect your data.
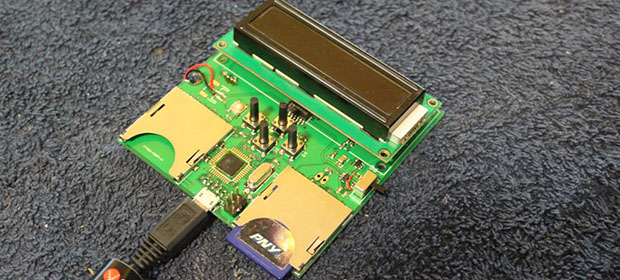
NSA Away is one of these tools. The first part of the project is a standalone key generator that writes the same random bits to a pair of SD cards simultaneously. With their random number generator, this is perfect encryption. The only way to crack the one time pad the team is using for encryption is to 1) use parts of the pad more than once, 2) have a terrible RNG, or 3) do something really stupid like sell the one time pad in a store.
The other part of the build is an Android-based encryption device with a camera, keyboard, SD card reader, and a USB port. This device reads the ‘OTP SD cards’ and reads data with the camera using OCR and decrypts it on the screen. Provided the OTP doesn’t fall into the wrong hands, this is a perfectly secure way to transmit data to anyone.
As far as progress goes, the members of the team have a fully functional pad generator, writing random data to SD cards. This device can also output random bits to a computer as a USB HID device, should you want to transmit your pad over unsecured mediums.
It’s an impressive bit of work, especially in the RNG department. The team is using eight avalanche noise generators in the circuit description. This part of the build isn’t quite working yet, but that’s really not needed for a proof of concept.
 The project featured in this post is a quarterfinalist in The Hackaday Prize.
The project featured in this post is a quarterfinalist in The Hackaday Prize.















Interesting…but can they make security less of a pain in the ass?
move your keyring to your front pocket
He said “in the ass”, like the way a proctologist would inspect a sphincter.
Additionally, I doubt one would want such a key ring on thier person after being recovered.
We see it as a continuum, with human verifiability at each step an important aspect to nail in the initial prototypes. Eventually it could become a single product that would handle everything, but then human verifiability becomes a lot more difficult. The product we’ve been working on is the first step towards the end goal, and proves that the concept is possible and viable and human verified. Then comes the single device.
So, it does a lot, except the random number generation bit is not working yet? So cool device that does not do it’s core function? (which is, generating true random numbers)
Maybe you should learn the correct use of the English language before you use it to nitpick.
Volgende keer zal ik m’n native taal gebruiken.
Thank you
I really need to learn Dutch… or is that Germanic?
@F: be nice, your comment contributed nothing to the conversation. Thanks.
perhaps we could make an infinite series of posts, each indicating the pointlessness of the previous post
your point is remarkably pointless… srsly?
Hahaha. Prima. Dan gebruiken we toch onze moedertaal?
To be fair, this was the first revision of the board, and I hit 90% of the functionality on the first try. The random number generator DOES technically work, but not at voltage levels that I can discern with the microcontroller. I’m using the pseudo RNG or the watchdog jitter library as stubs for now to demonstrate it working end to end. The next revision will improve the circuit so the hardware RNG works at digital logic levels.
Designing, and testing, a good HRNG is very difficult.
“Android-based encryption device”
I fail to understand why they choose a slow and not that secure OS. Ok, they disabled all networking in hardware, but its still sluggy compared to all true Linux distros out there. A faster OS would bring same results on less powerful hardware which would translate in lower costs.
“translate to lower costs”
You do realize that using commodity hardware IS the lowest cost way to go? Do you REALLY assert that a hacker project is going to have lower production costs than a factory production line?
@qwerty
You’re missing the point. The cost savings comes from the fact that *you’re going to have a cell phone no matter what.* It’s like all those hacks that are free IF you have all the required parts on-hand.
We chose an Android device because we wanted to quickly develop a prototype that had a camera, keyboard input, SD card reader, and could do OCR. The long term plan is to have a single device that has the hardware RNG built in and handles all the features on the android device, but for now we’re implementing it in two separate parts.
The initial implementation uses Android as a convenient prototyping platform. Android may be slow but is more than sufficient for prototyping purposes. Ultimately there are a spectrum of potential solutions ranging from continued use of commodity hardware to a dedicated encryption/decryption and key generator device to a pager-type device with integrated transport.
@qwerty
We’re using an Android phone right now in our prototype because it’s (relatively) cheap, and easy to develop for. We never made any claims about speed or security, and Android’s not going to be used in the finished product.
Liam
why not based on the transistor junction, it’s already a good RNG, and easy/widespread design.
My bad I didn’t see that’s what they try to use.
It’s good that such a device exists.
But despite OTP being a theoretically “perfect” cipher, maintaining this perfection requires maintaining drastic opsec.
Basically, avoiding anything computer or electronics related would be necessary.
What if the device itself is compromised at some point ?
Security of past transmissions relies purely on efficient destruction of the used pad bits.
Deletion of data on a SD card cannot really be relied upon.Even if you wiped the used data bits, the internal mechanisms involved in wear leveling in the memory chip itself might just rewrite some other totally arbitrary area of the chip while retaining your original pad section somewhere on the chip.
Using an android device in the mix also adds a lot of unknown variables to me.
But as always, useability and security are mostly exclusive.
Don’t get me wrong though, I find this device drags the cursor the good way by a significant amount against many potential adversaries.
Having a no-computer hardware RNG generating your data in the first place is the first step towards achieving reliable high level privacy.
And exploiting the scenarios I evoked might require significant dedication from a potential adversary.
More good info on otp usage and opsec here:
http://users.telenet.be/d.rijmenants/papers/one_time_pad.pdf
it depends on the time value of the data
if the data needs to be private today and public tomorrow then you don’t need to worry about future discovery
for instance apple can use this to hide their product plans because this information is vitally secret today, but 10 years from now it will be written up in college textbooks.
What about using a little bit of radioactive material, like americium from a smoke detector, and a pin diode as a random number generator?
hackaday comments are a great source of random noise
The noise is biased due to all the posts that are just “How is this a hack?” or “What’s the pont?”
this
One important part about random number generation is speed of entropy. With our current device we have 8 RNG circuits in parallel to get enough entropy fast enough. With a small batch of radioactive material, you have to compromise; too little material and you don’t get enough radiation to have fast RNG, too much material and nobody can use your device.
Seems like a lot of trouble just to watch porn.
RF atmospherics is a good source of noise, especially with a narrow bandwidth. It’s basically all background static with bits thrown in here and there.
Until someone places an RF transmitter near the device
Yep. We don’t want the RNG to be compromised by nearby RF, and there are a lot of periodic, bias-creating signals on RF.
Best. Rickroll. Ever.
Doesn’t matter with a one-time pad.
I am sure a secret court order has been passed to make this type of development illegal. This is essentially making tools to assist in breaking the law, especially the laws that are classified
We haven’t been contacted by any government organizations yet. We believe we’re on pretty safe ground here, as we’re just generating random numbers and using the OTP algorithm, which is well documented. We shouldn’t have to worry about ITAR or export, and there are many uses for this technology that are completely legitimate, just like bittorrent.
Not to worry Bob. This stuff is considered as “educational”. Just like Amateur Radio and other electronic hobbies this stuff is viewed by USG as “helpful” as it prepares future “employees” to be prepared for this kinda’ stuff. The BLACKHATS are doing stuff that is light-years ahead of whatever you can come up with. It’s called Quantum Cryptography or QKD. Now if you had a hack for QC then yes someone with a badge would be knocking on your door.
And the run-of-the-mill Blackhats like the late UBL* only used 3.5″ diskettes with clear text on them run by couriers to dead-drops. They also may have uploaded them at Internet Coffee Houses in Pakistan too. Still in clear text (albeit in Arabic)
*Source: reference in the news USN ST-6 operation at Abbotabad Pakistan
So don’t be worried about being misidentified as a Blackhat. HaD is viewed as a creative educational source for future WHITEHATS. And anything TRULY illegal will be caught anyway. Did you forget about the CLIPPER CHIP? Not a dead issue even today. Computer manufacturers quietly moved forward on that. If THEY really need to check what your up to there is a whole cadre of undocumented/sneaky SIGINT/ELINT tools to “look up your skirt” quite easily without your knowledge.
As Edgar Allen Poe once suggested, the best place to hide is in PLAIN SIGHT. Just bury yourself in the random loud philosophical background noise of the “Internets” (George W. Bush reference).
:-)
A good source of random noise can be gleaned from the NSA’s own museum website. We totally fooled the Germans in WW2 with the SIGSALY machine. It was a voice encryption machine for POTUS and PMUK as well as one or two of our SRO Generals. This gadget was way ahead of it’s time. It used encryption that was even better than German ENIGMA. Alan Turing (breaker of ENIGMA & Japanese PURPLE et al) helped develop it.
He used OTP sampled RNG from a mercury arc lamp. The sound could be digitized with a ADC. The only problem is synch-timing. Just like Spread Spectrum you need an accurate timing synch-source to know when to start synch. They used the US NAVAL time source in WW2. But that’s for live voice communications. A static data source does not need a timing source as you just start at the beginning of the clear text and the beginning of the OTP. It’s not being transmitted live nor changing modulation like live voice.
If you can’t find a surplus Hg arc lamp you could get access to an ancient DEC VAX (or better) at your local college and generate pseudo-random numbers with a FORTRAN math sieve that looks for very large number non-prime factors (standard laptops and desktops would take hours or days to generate – a VAX or better could do it in seconds). Then convert them to 5-digit grouping to look like a real operational OTP (to further confound your adversary). This could serve as your OTP and you can generate it on the fly if you transmit the scientific notation as a number pair. That would be your PRIVATE KEY. Or one number could be your Private Key and the 2nd number (the exponent or indices) would be your PUBLIC KEY – or vice versa.
Of course the other side would need a FORTRAN compiler and a mainframe (or a mini-supercomputer) too to generate it on the fly. It would be better to just postal mail or dead-drop the OTP on a SD chip like the OP is suggesting. However, the sieve output looks truly random but really it is not as the numbers are actually mathematically reproducible. The NSA (et al) would only need access to your Private and Public keys and they could break your code. But that would mean deploying CSS *g.o.o.n.s. to ransack your flat like in that movie Enemy of the State with Will Smith and Gene Hackman. :-)
*g.o.o.n.s. – government official overt nondescript sneaks
P.S. – Why FORTRAN? Because very long numbers are easily handled with it. Why VAX+? Any computer that has the MIPS to beat a VAX 500,000 instructions per second (i.e. RISC) will do. VAX’s are still generally cheaply available to universities and surplus market. I guess a Beagle Bone Black running at 2000 MIPS/MHz or Raspberry Pi at half that could do it? But can they run FORTRAN or at least do very large number math?
Furthermore, SIGSALY used two one-time use LP phonographs (old fashioned records) with the RNG sounds on it. In this case the two SD Cards are a parallel idea I guess.
When the SIGSALY technicians needed to test the system they would not use the precious RNG records.They rigged up a Rube Golberg setup of stepping relays that fired at seemingly random times. But that was an electronic trick that is really very non-secure.
If you want an easier non-PITA (pain in the azz) methods of Pseudo-RNG you could just use the random number math commands in say JavaScript, C+. VB, etc. to generate at least 28 days worth of numbers. It seems that those math commands tend to recycle same numbers in about 28 days making then unreliable. But still quick & dirty enough for people NOT in the IC biz like you guys.
Also, you could make your own RSA style of private key generator like that snazzy key-fob they used to have (or still do). Using MS Excel you design a spreadsheet or macro that uses today’s date and/or time to encode a seemingly randomly changing private key. Your buddy operates the same program on his side. No randomize commands are used at all. Just straight math based on the encrypted time-stamp-seed. They are in synch as they use the correct time from time.nist.gov for your PC’s clock and the constantly changing number on the screen is in step with your partner’s. You can use this as a rolling password or a rolling private key you DON’T have to privately transmit to your partner.
However,this only works for LIVE text chats and voice. If you want to do archived data you’ll have to devise a way to archive the seeds and sending the archived-time-stamp somehow to your partner as a private key.
Also found a neat way of sending almost-good-resolution images via text. You can Google it (websites that convert JPG to high-resolution text images). But imagine sending images as text saving tons of bandwidth. You can encrypt it too.
With OTP the danger is with interception of the pad going undetected, so you should probably encrypt and sign it just in case it is intercepted, and then that will give the NSA something time consuming to do buying you time for your communications to devalue.
Just a crypto noob question, why have the encoded message OCRed? Why not just decrypt the received encrypted text? (Would be great for e-mail!)
Because one of the biggest pains for NSA (et al) is people who send their code in JPEG format. It can’t be picked up with PRISM and other ELINT/SIGINT programs if text is a picture image. The only thing that can read a imaged text message is OCR. And OCR is not 100% foolproof. It misreads a lot. However, Google is trying out a new image search engine that is showing a lot of promise regarding scanning images against a image database.But JPEG-text is still a problem child. Blackhats also use to embed text in JPEG porn images too. Somebody will figure it out I guess. Maybe somebody at inQtel will break it. They work very closely with Google.
Since you prefer email text coding here’s a very old trick using email that uses HTML or real formatting. Wont work with text only email. It’s not a big deal and is super-simple to defeat but usually over looked by some. Simply highlight the text at the bottom of your message and make it white on white background. It looks like a lot of white-space and can be easily revealed by highlighting the area. Otherwise it’s a quick and dirty method of hiding a part of your message in plain sight.
Great question. We assume that the computer the user receives the email on is compromised because it’s connected to the internet. Therefore, we don’t want either the SD card with the one time pad file or the decrypted message to appear at any point on a compromised system. We also wanted the transmission method to be completely open, so you could print off the encrypted message and send it via snail mail or even printed on a billboard. We used OCR because it’s a verifiable way to get data across the airgap and into our secure device with no potential for compromising it.
Oh I get it, very clever, can’t wait to see the project done!
All the encryption is already broken before implementation, and no one has too care anymore. Really only a faulty compression mechanism the moment.
;-)
There’s a 70 year old message from a British spy within NAZI Germany during WW2 that was sent by Carrier Pigeon. They found the pigeon’s skeleton in a British chimney where it died in 1944. The message in it’s leg cartridge is STILL almost unbreakable to GCHQ, MI5/6, CIA, and NSA. Nobody can break it. Why? It was written with an old WW1-style OTP key.
Also another encryption that is hard to break is one invented in ancient Greece. President Thomas Jefferson exploited it by making a wooden multi-layered wheel cipher with it. It helped US to beat the British in 18th century. Its called Stenography.
Google: Unbreakable code message found on WWII carrier pigeon
Google: Thomas Jefferson Bazeries Cylinder
How about this RNG concept/circuit: http://www.jtxp.org/tech/xr232web.htm ?