There’s pandemonium on the streets. You look down from your 4 story apartment and see hundreds of people marching and chanting. You pick up your phone and call your buddy, expecting it to link up to the nearest cell tower which will route your call to where it needs to go. Instead, without your knowledge, you link to a tricked-out police surveillance truck a few blocks away. They intercept your call and listen to the conversation in hopes of tracking the protest.
Dispatch: “CPIC [Chicago police’s spy ‘fusion’ center] on the air for a mobile”
Officer 1: “Go ahead”
Officer 2: “Yeah one of the girls, an organizer here, she’s been on her phone a lot. You guys picking up any information, uh, where they’re going, possibly?”
Officer 1: “Yeah we’ll keep an eye on it, we’ll let you know if we hear anything.”
Officer 2: “10-4. They’re compliant, and they’re, they’re doing ok now but she’s spending a lot of time on the phone.”
Officer 1: “10-4”
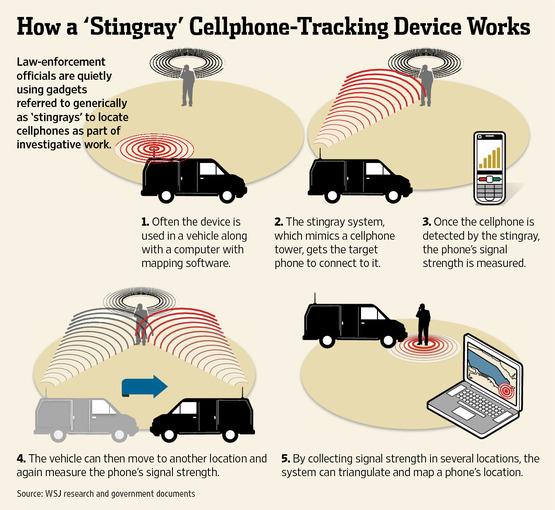 This scenario undoubtedly took place on November 28th of this year in downtown Chicago. People began to notice the truck following the protest, some even complaining that their cell phone stopped working when it was close by. Most probably had no idea that the police truck was equipped with Stingray technology. It forces your cell phone to connect to it as opposed to the nearest cell tower, allowing authorities to listen in on your conversations and track individual phones by moving and measuring the difference in signal strength. The hacking group Anonymous released some audio of a conversation between two officers and a command center (block-quoted above) which provides damning evidence that such actions indeed took place on Chicago streets.
This scenario undoubtedly took place on November 28th of this year in downtown Chicago. People began to notice the truck following the protest, some even complaining that their cell phone stopped working when it was close by. Most probably had no idea that the police truck was equipped with Stingray technology. It forces your cell phone to connect to it as opposed to the nearest cell tower, allowing authorities to listen in on your conversations and track individual phones by moving and measuring the difference in signal strength. The hacking group Anonymous released some audio of a conversation between two officers and a command center (block-quoted above) which provides damning evidence that such actions indeed took place on Chicago streets.
So here’s the question: Can it be fooled? Can you spoof the spoofer? Can you tell the difference between a signal from a Stingray versus a cell tower? If this is not possible, surely the cell network providers can add something to the signal allowing end users to verify that it is a legitimate signal from a cell tower. But can it be done in a way that a Stingray can’t replicate?
https://www.youtube.com/watch?v=QLpk2EB6LMo
Thanks to [John Tirelli] for the tip!
















You could just encrypt all communication with OpenVPN. It won’t work for standard phone calls or text messages, but iMessage or other apps would be encrypted. And using Skype or other VOIP apps would get you encrypted voice communications.
Sure, it won’t do much to stop them tracking individuals via location information, but lets face facts. You are visible, they can track you through eyeballs or FLIR.
You may be able to make the conversation private but you can’t easily hide who you are talking to.
That’s not true – They can see which server your VPN connection ends at but that doesn’t tell them *who* you are communicating with.
Not only that, but off all your traffic is going to a single location, it obfuscates what you are doing as well. They can see encrypted traffic, but they can’t see if you are using VOIP, iMessage, or any other application. They see traffic.
Stingray is more for use by local operators. Getting a feed directly from the phone network involves warrants and a “Federal” touch. The only reason a Fed would need this is if the job is totally off book.
It may not tell them who but it does tell them where. All the VPN does it slow down the process a bit
Just use redphone, textsecure, or ostel for full voice or text encryption, very easy….
RedPhone where do you get one ant links you can provide?Or images you can post?
The US Marshalls use it to locate wanted Fugives. If local is workknh joint task then they will get to use it also. But the primary purpose is to track not listen, and by the way encryption of not they can still see it
It is too late to help Steve Irwin!
Maybe you can stop a stingray it by sneaking up behind it and jamming your thumb in its butthole?
https://www.youtube.com/watch?v=a_1OVYsLqMU
I’m not offended; just puzzled at the dated joke.
It’s too late to help cheetos coated on the finger trolls ;who live under their parents’ house, from making stupid jokes.
A higher quality video: https://www.youtube.com/watch?v=xpdpjX8Vsfw
Higher quality video: https://www.youtube.com/watch?v=xpdpjX8Vsfw
Presumably, it’s easier with the fact that phone aerials are omni-directional so they’d pick up anything that’s sufficiently strong nearby.
If one could use a directional aerial (a lot of older phones allow an external antenna to be plugged in) and point that to the base station location (locations listed on the internet) – while not impervious to attack, it would attenuate any off-axis signals such that the ‘stinger’ van would need even even more power to take-over the connection to the base station.
Almost all modern phones still have a connector inside.
Not all phones have it easy to access, though.
On my 50-dollar LG I can just take off the battery cover, and the case already has threads for me to screw an extension right in. On a 500-dollar LG phone, I can’t even do that.
Farawaycage wood block all singnel.
Could signal strength somehow be used to determine if the ‘cell tower’ is moving, provided that the phone is not?
How about an app that uses the phone’s current GPS location/heading plus the signal strength to check against a database of known cell tower coordinates? Not sure any of that is even possible, but it would be fascinating.
This…. is a good idea. Have a database with all of the available towers, and just calculate what your signal strength SHOULD be from your location. Anything more should be warranted as suspicious or not trusted.
This is a good idea. Doesn’t sound like it would be that hard to implement. Jesus we are on to something
It will be somewhat difficult to implement, considering the distance to a cell tower is not the only factor that determines the signal strength. Buildings and other obstructions, multi-path signals, etc. all influence signal strength and quality.
Besides just measuring the actual signal strength, it might also be possible to measure the field gradient; that is, how fast the signal strength increases or decreases when you either travel a short distance towards it or away from it, or compared to the signal received from another phone nearby. Signal strength drops with the square of the distance, if we can ignore all other influences. A weak signal will drop significantly if you move from 80 meters away to 100 meters away, while the signal from a strong cell tower that is 1000 vs. 1020 meters away hardly drops off at all. I think the field gradient might be much more telling than the absolute field strength.
Obviously the communication with any other phones would have to be encrypted and authenticated, since it would either have to go through the stringray cell site, or via ad-hoc WiFi, and in both cases the stringray or other device could mess with the data if not properly guarded. On the other hand, anyone messing with data connections would probably be a dead giveaway.
I wonder if you could detect the presence of a stingray by measuring round-trip time? Since it’s an extra hop, and has to relay all the calls to a real cell tower, the extra latency might be sufficient for detection.
You could also have people live-updating in the background, data willing, the signal strength on different days, only info needed would be the site the phone is tied to, signal strength, and the most accurate GPS they’re willing to give, this way it gives a closer idea to the actual strength at any particular location, and if it changes, check if there’s an environmental difference(user interaction to indicate a weather difference?) or see if the tower itself has changed characteristics overall(infrastructure update/ upgrade?). Community data collection, heck, even the cell companies could get onboard and get a better way to fill signal holes, fewer dead spots if they knew where they were.
Again though, this is if people were willing to help with the basic info, and moreso if they’re willing to go the extra mile.
You could also have people live-updating in the background, data willing, the signal strength on different days, only info needed would be the site the phone is tied to, signal strength, and the most accurate GPS they’re willing to give, this way it gives a closer idea to the actual strength at any particular location, and if it changes, check if there’s an environmental difference(user interaction to indicate a weather difference?) or see if the tower itself has changed characteristics overall(infrastructure update/ upgrade?). Community data collection, heck, even the cell companies could get onboard and get a better way to fill signal holes, fewer dead spots if they knew where they were.
Again though, this is if people were willing to help with the basic info, and moreso if they’re willing to go the extra mile.
-> Buildings and other obstructions, multi-path signals, etc. all influence signal strength and quality.
luckily they are constant and can be matched with a ratio so that your phone performance is not important
I would suggest not trying to look for some difference between some constant value (such as a database of towers and your location in reference to them) and your current cell connection, but for the change in value between your connection you recently had to a legitimate tower and the stingray van when it goes to hijack your signal.
An app on your phone could log your location and any towers with which your phone interacts at that location along with the associated signal strengths observed during the duration of your presence at that location. Then, if in the future that app sees a change in a tower ID (or other identifiable information about any towers it is “used to” at that location) or a signal strength for that tower is significantly outside of its recorded range, the app could warn you that your signal might be getting hijacked.
This wouldn’t protect you in a new area, but it would protect you at home or work and any locations you routinely visit. A national database could be gathered from all the app users so that your phone could ask the app if the readings it is getting are within range.
Granted, then you would have to trust the database. :)
hmmm, use distributed computing with apps on protester phones to map the location of the stingray van on a google map in real time… cool :-)
Here’s your database http://opencellid.org/
Except this will only show you GSM sites and not CDMA (like Sprint or Verizon).
Not to worry, CDMA blows and nobody should be using it.
Easier than selectively blocking stingray somehow, just set up multiple disposable phones to make calls to other random phones and play a pre-recorded message. That way, they’ll end up with conflicting info and no idea what the real plans are. Other thoughts are to leave a phone somewhere else and communicate to and through it with another method, such as radio (encrypted) and/or a remote-control app like airdroid. Any way that has all data from you going to ‘the internet’ -> a computer next to your phone -> sound waves -> the phone -> the other activists phone. Or, have everyone use a decently encrypted VoIP app. Or throw jammers at any suspicious looking trucks cruising around. Or get the location of said trucks by getting signal strength from everyones phones and looking for a moving point of origin and doing your own triangulation. I think I’d make a good anarchist, apart from my tendancy to post all my plans in random, publically accessible hackaday posts :P Oh, and of course where I live the height of police tech is big sticks so my only useful attribute is a thick skull.
Or even more fun assuming that they are tracking your location by your phone, pass/swap the burnt phone around.
Posting updates on websites in coded phrases. They can still follow the readers, but not so easily in real time.
I think you miss the point here, which is that while they’re targeting suspect A, they’re sweeping up everyone else’s cell phone data – including the content of SMS messages and the voice call itself. It’s a 4th Amendment violation of all of us. And in most cases they don’t even bother to get a warrant. A case in Boston was almost poisoned because they refused to tell the judge anything about the Stingray, citing a confidentiality agreement with the manufacturer. The judge was not amused, saying the court had no such confidentiality agreement and demanding they produce the evidence. The prosecutor declined and decided to press on with the case without the evidence gathered as a result of the Stingray info.
Meanwhile, judges in Pierce County, Washington have recently learned that the warrants they were approving were not for the suspect’s phone as they were led to believe but rather were for Stingrays that gathered info on all phones in the area, and they were not amused either.
What’s worse, in a case in Florida the judge demanded the Stingray info so the Feds deputized the local cops as Federal Marshalls, who then turned the Stingray data over to the Feds taking it out of the reach of the state court. The bottom line here is that these devices are being used by local cops to gather data on EVERYONE for the Feds.
The solution to this is to shine a light on the cockroaches. The cops/Feds best weapon here is to keep the public ignorant about the Stingray, what it’s capable of, and how they’re using it. Our best weapon is an informed public.
There’s also the slight issue of any and all (no matter what agency or individual operates it) kind of cell phone jamming being a violation of FCC law (as far as I know). This is a clear case of do as I say, not as I do.
Of course, you could just get rid of the stupid cell phone altogether. There are plenty of other ways to communicate, and I’ve been perfectly happy NOT having a cell phone for the last few years, as they are no longer a job requirement for me (Yay retirement!).
I imagine the easiest way is to disable GSM. My phone was set to 3G only for months without me realising. Sure, get out in the countryside in a poor cell area and you have no reception but in if you’re worried about being tracked then surely this could help?
as far as i´m concerned stingray devices also work on 3G (heard of it a few years ago)
UMTS is not secure, or, atleast much less than previously assumed.
I may be ignorant here but it seems to me that a legitimate loophole would be to use 2 WiFi calling-capable cell phones, thus bypassing cellular signal altogether. Granted, it would limit your usage areas and be cumbersome, as you’d have to jump from public Hotspot to Hotspot but with as prolific as WiFi is these days you could probably get pretty far with a 1 day Boingo subscription or just sticking close to corporate coffee shops and bookstores.
All of the cell phone infra structures support legal interception as it is part of the specs and government requirement. So do not assume that it will be secured at all. Have you ever wonder why there are security clearance requirement in private sector telecom/network equipment manufacturer job listings?
The only secured part is against another casual user not for government agencies/foreign spies.
You know.. they could be watching her optically (with their eyes) to see if she is on the phone. There is nothing in the message that proves they know what she is saying on the phone. They only say she is talking a lot on the phone. I can sit here in my cubicle and tell when my cube mate is spending a lot of time on the phone by looking at him. I am not saying they weren’t listening … just proposing that you don’t need tech. to make the observations that are made.
Certainly possible but the question “You guys picking up any information, uh, where they’re going, possibly?” certainly seems to suggest they’re wanting to know where the phone calls are going – that is, who she’s calling.
Since it’s presumably a peaceful protest, they probably could just go talk to her as well. In fact, a smart organizer would probably just go tell the nearest officer what the plans are. Spying only seems useful if you think they are going to start a riot or something else illegal.
The cops ALWAYS think a protest is about to turn into a riot or something illegal. Any large gathering makes them nervous.
With good reason I suppose. We just had a protest go awry in Milwaukee, everything was going well till some dummy lead the group down an on ramp onto I-43. 50 plus arrests I think.
Not sure if either spying or talking would have helped, but some upfront communication couldn’t have hurt.
Except that Minneapolis had no problem with a similar protest a few weeks earlier. The main difference is that police didn’t decide to start attacking and making arrests, they just protected people and waited for the protesters to get out of the way.
There’s always the aggregate data route, of tracking ‘true’ cell tower information and controlling connections via app.
http://www.wired.com/2014/09/cryptophone-firewall-identifies-rogue-cell-towers/
I would think it could be done fairly easily IF the cell companies wanted to do it. You’d do something like SSL with asymmetric encryption, where the cell towers have a known public key and transmit a message encrypted by the private key. You could use this to exchange a symmetrical key to encrypt the conversation or as part of a system without encryption where the phone ignores the signal if it’s not broadcasting a proper authentication. The broadcasted authentication couldn’t be static, of course, or the Stingray could simply use a replay attack to broadcast the authentication signal. But it should be possible to incorporate the time of day and other information to constantly update the authentication message.
Of course this would be useless if the phone companies merely hand over a copy of the private key to the authorities. I doubt this would entirely eliminate the locating service you describe, as each cell phone transmits a signal which can be received by anyone and it’s probably fairly easy to fingerprint a signal and triangulate it passively. But without the cell phone actually connecting to the Stingray, it might be quite difficult to determine which of the many cell phone signals is interesting.
That wouldn’t stop spying, they’d just go an send a National Security Letter to the carrier and force them to cough up the keys.
I’m actually an ‘expert’ in this area. One thing that may tip off the user that this is occurring is that many of these systems work only for GSM. Additional systems are usually deployed to create interference and to force the user’s phone from 4G/3G service back down to 2G – GSM so the ‘Stingray’ can start intercepting / interrogating. An observant user can notice that cell-phone reception for 3G/4G has suddenly degraded as indicated on their phone’s signal bar and network indicator.
” many of these systems work only for GSM” — does that mean they can’t track Verizon and Sprint phones?
And are the stingray devices encrypting the channel or forcing it open?
IIRC from a blackhat convention a couple of years ago, they were able to spoof a tower but not the encryption, but most cell phones don’t (didn’t) notify you if you were on an “unencrypted” tower as it was supposed to be rare.
And if they are encrypting as a tower, is that legal as they would have to unencrypted it to pass on to a carrier’s tower, bypassing an encryption technology used to encrypt media (in this case, voice)?
And are they copying each phone’s signature/identity when they do pass on the information, and are they copying the carrier’s tower’s signature/identity when they talk back to the various mobiles?
My thoughts that I’m sure someone smarter and more informed than I has already looked into
0) Only connect to the second strongest tower
1) Force tower change every (arbitrary period of time, probably) <30s
2) Prioritise towers that have been connected to historically in that location
– Specific whitelisting the day before an event, corroberating against open tower id lists
– Blacklist towers that suddenly start
3) Modulate transmit strength by a random amount / an amount proportional to the tower signal strength
– Try to make it look like you're always the same distance away
– Kudos if you can reverse-triangulate and try to give them impossible results, like "in space" and "
4) Coordinate group tower selection, so that white and blacklists
– Have the group mass-migrate towers so that you can be sure that if there is any vulnerability, either everyone is vulnerable (on the false tower) or no-one is (or they can spoof multiple towers at once)
– This may have the bonus of causing the device to be unable to hold all the incoming connections, revealing a vulnerability, or masking important information through dumping noise on them
– To harness the surrounding non-targets, perhaps you could selectively cause interference with known towers in synchronicity to force everyone to try and connect to the same (blacklisted) tower at once. But that would be active ECM and illegal.
But the best course of action is probably to try and measure the output of one of these and get the FCC to ban them
To be honest, I can't understand why they don't just record every conversation and signal strength / ping for every mobile in a 8-cell perimeter around a target of potential interest, have the metadata soaked up including internet usage from the wired connection that you cut then sent a "repair" technician to bug and pair to your bluetooth-enabled toaster so they can work out exactly what time you'll step out the front of your door onto public ground so they can arrest your punk-ass'd self for a crime they will be able to prove you could have committed once they ask for a warrant using the evidence they got without a warrant to declare you an interesting person in the first place
– as opposed to the usual strategy of "if you're not american you're a (potential) terrorist and have no rights, and if you are an american (or an american overseas) we will ask a FVEY member to spy on you and then just ask them to hand it over"
Can anybody comment on the Android IMSI-Catcher-Detector? (https://secupwn.github.io/Android-IMSI-Catcher-Detector/) I know it’s in Alpha stage but is this fingerprinting they try to do the right approach?
What about using WiFi calling through a VPN connection? (Using a Wifi Hotspot you carry around with you.)
Satellite phones would work also, and the cost of those are coming down, even some unlimited plans available.
If 3G and 4G are being blocked locally to force phones onto GSM, what portable hotspot technology are you going to use?
There are unlimited plans for Sat phones? I’d be quite interested in seeing one. I travel internationally for work and AT&T’s international roaming fees ($20.48/MB) are enough to make a $1400 sat phone look goddamn cheap…
Plus being able to make phone call in the air would be pretty handy.
Holy hell. I just looked this up, and you’re looking at $72,000 per year for transferring 24 Gigabytes over satellite.
Better than $503,316.48 for AT&T International roaming for that same volume… But that is why I am wanting an unlimited plan. Plus I would no longer need to worry about national firewalls and all that crap. All my data passes through a couple servers that compress and encrypt the data anyway (I have a 1 TB look-up table on either end that does a bulk of the compression, then either the look-up ID, or raw data if the data block isn’t in the table, is then encrypted and sent along)
Nothing I do (big data analytical stuff) would be of interest to a government, just of interest to competitors and malicious hackers.
Avoiding triangulation would be tough, without having your own repeater system setup. Encrypting a voice call through data is relatively simple, but I’m sure they can drop the data communications if needed. There are analog encryption devices that could be used for the audio traffic, but since the guys who invented them are in the truck, that might be a long shot. I’m sure with advanced notice you could map out the details of the cell towers in an area and find out if they are not being used.
A jammer would defeat you and them, so not a good option. Spamming data/information might work. If you were able to generate enough signals with enough information, you may be able to overload the device, and then the real tower should take over, I guess it would depend what the capacity is on one of these devices [ ie 100, 1000 10000 devices]
If you had a way to triangulate the ‘tower’ and become aware that it was moving you would at least be able to know that the fuzz is on to you.
I wonder how it works with sat phones?
Anyway, just some thoughts.
Trilateration is the process they are using for location processing… http://en.wikipedia.org/wiki/Trilateration. Some draw backs to using signal strength as a measure of distance is multuipath return (one signal can take multiple routes to get back to you) and some wireless technologies reduce power output to save power (when the signal is good) and when the cell tower is congested.
When cellphones allowed full control you could set your phone to connect to a specific tower only. Now phones dont let you have that control. But how about turning off all roaming, unless the feds are faking an AT&T tower it should not connect.
You can spoof credentials to look like the local tower
http://youtu.be/xKihq1fClQg
Build a robot (a drone, perhaps) to home in on their signal and then jam it at short range.
Or just wrap the van in tinfoil. ;)
It can be done, or at least made unnecessary. The trick is doing it legally.
Jammers are illegal. And dangerous. If someone really needs 911, then a jammer could kill somebody. That’s a really bad time in court for the person who used the jammer.
Directional antennas are a help until the cell tower is taken out of service. Unless you use them to bounce your signal off of something to force it to use a different cell tower. But that really isn’t practical. Carrying around a 4′ dish is pretty obvious.
Anything you put on a cell site to make it legitimate is going to be incorporated into a mobile listening post such as a stingray. Harris, the company that makes the Stingray also builds cellular sites for deployment by the military. Cell site protocols are open and available for anyone to build equipment to.
Using various apps like firechat or the like can solve the data networking problem. It’s voice that gets tricky. As pointed out, a VoIP app with VPN is a good defense. But that only protects the content. You still need to eliminate the traffic analysis problem. To do that, use a VoIP app, don’t hang up the phone and everyone dials into a conference bridge. Combine that with an app that sends random bursts of data or a constant stream and the traffic analysis problem is reduced, but not eliminated. It all depends on the quality of the surveillance you are trying to defeat.
That still doesn’t eliminate the triangulation problem. It makes it easier. To eliminate the triangulation problem, you have to stop emitting a signal. That means pulling the battery from the phone, moving, and making the next transition. Keep it short. The more time you transmit, the easier it is to find you. Just ask a Wild Weasel.
As was pointed out, far easier is don’t use a monitored channel of communication. Better still, use several. Bounce the signal between systems, rf, light, line of sight, etc. But that requires pre-planning, etc. And using RF without a license (even with if committing a crime) crosses you into a whole different realm of potential federal felonies.
It can be done, or at least made unnecessary. The trick is doing it legally.
Jammers are illegal. And dangerous. If someone really needs 911, then a jammer could kill somebody. That’s a really bad time in court for the person who used the jammer.
Directional antennas are a help until the cell tower is taken out of service. Unless you use them to bounce your signal off of something to force it to use a different cell tower. But that really isn’t practical. Carrying around a 4′ dish is pretty obvious.
Anything you put on a cell site to make it legitimate is going to be incorporated into a mobile listening post such as a stingray. Harris, the company that makes the Stingray also builds cellular sites for deployment by the military. Cell site protocols are open and available for anyone to build equipment to.
Using various apps like firechat or the like can solve the data networking problem. It’s voice that gets tricky. As pointed out, a VoIP app with VPN is a good defense. But that only protects the content. You still need to eliminate the traffic analysis problem. To do that, use a VoIP app, don’t hang up the phone and everyone dials into a conference bridge. Combine that with an app that sends random bursts of data or a constant stream and the traffic analysis problem is reduced, but not eliminated. It all depends on the quality of the surveillance you are trying to defeat.
That still doesn’t eliminate the triangulation problem. It makes it easier. To eliminate the triangulation problem, you have to stop emitting a signal. That means pulling the battery from the phone, moving, and making the next transition. Keep it short. The more time you transmit, the easier it is to find you. Just ask a Wild Weasel.
As was pointed out, far easier is don’t use a monitored channel of communication. Better still, use several. Bounce the signal between systems, rf, light, line of sight, etc. But that requires pre-planning, etc. And using RF without a license (even with if committing a crime) crosses you into a whole different realm of potential federal felonies.
“Anything you put on a cell site to make it legitimate is going to be incorporated into a mobile listening post such as a stingray. Harris, the company that makes the Stingray also builds cellular sites for deployment by the military. Cell site protocols are open and available for anyone to build equipment to.”
I don’t disagree with much of what you said but I will point out that there are lots of open protocols that support secure communication. If you’re relying on the details of the protocol to provide security through obscurity, then yeah you’re not going to have much luck with that. But it’s quite possible to build authentication into an open protocol.
I wholeheartedly agree. But essentially impossible if one end of the communication is compromised, which you have to assume in the case of the cellular companies. Especially if the cell tower is a spoof of a non-existent company.
There are devices you can buy for sub $2,000 on ebay that will spoof a GSM, CDMA, PCS, or even 3G cell tower (more $). There is pretty much one to be found in every wireless carrier phone center with a repair desk, and they get surplussed regularly.
Sure but if we’re incorporating things into the cell phone tower, that necessarily implies that you’re altering the current technology and protocols. That means you can build an authentication signal using asymmetric encryption that relies on the tower having knowledge of a private key. Yes, if the remote end is compromised such as the cell company handing the police a copy of the private key, that’s not going to work. But if that’s the case, then the cell company can simply hand over the info to the police anyway and then what’s the difference in connecting to a cell tower and a Stingray?
The difference is real time data. Stingray is on scene and can provide tactical information Right Now. And over a smaller area. Towers cover larger areas and take longer to get triangulation, if only because of organizational interaction.
The connection between the communications companies and the government in the US is legendary. In other countries, they are often one and the same. You have to assume the key is compromised.
The false cell tower can also have it’s own key. Remember it just has to get your phone to prefer it over the other tower. Unless you manually lock your phone to a single tower, it just has to be closer/stronger and your phone will switch over.
I really like the idea of a tower map app that alerts you to new towers or sites. Even just one that tells you what tower you are connected to. Then new towers can be mapped. Modern sites usually provide GPS information too, so you could use that to map them as well as they map you.
warrants?
Android programs like Llama can detect cell phone tower IDs. They can be saved or mapped to ‘areas’.
If you have been in the area before you can map the surrounding towers to an area, and create an ‘event’ when you are no longer in the area. This would be triggered if you connect to a new tower that has not been mapped. This could be due to travel, or a stingray. (If they have a unique tower ID)
It would seem fairly simple to create an app that gets your location via GPS or other method, searches a database and sees what legitimate towers are in the area and provide their ID to the phone. That wouldn’t stop the Stingray from using one of the local IDs but if you receive conflicting signals with the same ID, your phone knows not to use that connection. The police could shut down a tower and impersonate it but that would require either a court order or close cooperation with the phone company and if you have the phone company freely cooperating with the police, there’s not much you can do anyway except not use that service. You could use some sort of end-to-end encryption to hide the contents of your call, but that wouldn’t do anything to stop metadata gathering or location tracking.
annonymous. Proof that college students will back terrorists if they think it will fight “the man”
What comes in, must go out.
Degrade the stingray’s uplink sufficiently, and it can’t handle traffic.
With reasonable intel and quick hands, this could be done with a piece of aluminium foil.
You’ll risk a whole bunch of charges and evidences that they would rather not have for nailing you if you are attempting to do anything physical or electronically to the van(s).
If you are in their line of sight, a directional mike or similar tech can still pick up what you are saying. Talk or better still tweet/post in predefined codes phrases to pass the information. It doesn’t have to be unbreakable, just needs to be minutes ahead of them.
Also you can go low tech… not use cell phones. People protest long before cell phone became wide spread.
If the cops want to use a Stingray to bust a drug dealer, I shouldn’t have to talk in code or use Twitter as my sole means of communication to avoid being swept up in their gross violation of the 4th Amendment. You’re talking as if the idea is to aid the criminal under investigation. I want a tool to protect the innocent not named in their warrant – assuming they even bothered to get a warrant.
This is not about drug dealers. This is about excising what’s legal under the law. You might want to read what the context is all about and not to drag it out of topic.
This is why I always use my shoe phone.
What about passive jamming? What side of the legal line does that fall on?
Have people on bikes towing a large, but lite, reflector that covers the correct frequency range. They transmit with such high power that they should lose any weaker signals in their own interference. Being 2d, they should not block the majority of cell traffic.
Keeping up with a truck could be a problem, but they want their truck to be where the protest is, so it shouldn’t be to difficult. The reflectors can be painted up with protest stuff to make them look a little better, but the cops will quickly figure out what they are when you pull up by them.
” If this is not possible, surely the cell network providers can add something to the signal allowing end users to verify that it is a legitimate signal from a cell tower. But can it be done in a way that a Stingray can’t replicate?”
The ISP’s have absolutely no desire to stop law enforcement form doing this. The telecommunications act gave the Feds all kinds of unconstitutionally abusive powers that they should not have and this is just one example of many of how they have abused those powers.
I suspect a legal attack would be the vest way to get these shelved. There are laws against snooping on people who are not breaking the law aren’t there ?
+1 funny.
LOLOLOLOLOLOLOL
Uh, there is no advanced RF equipment (AKA Stingray) deployed in that Emergency Management vehicle.
Looks like someone continues to perpetuate an incorrect assumption about a vehicle they don’t understand a thing about, in this case making a silly youtube video out of a couple still shots. It’s really making rounds on the internet and it’s sad to see so many folks willing to ride along when this is clearly not the Droid they’re actually looking for.
Those of us who have worked in this field will recognize that as not much more than a standard VIDEO surveillance vehicle, clearly lacking in any indications (though these horrible photos) of the required antennas/equipment to support a cell-tower-faking/wiretapping equipment.
Also please note, if Law Enforcement were deploying such a device, I highly doubt it would be in such a high profile vehicle. Cloaked vehicles (zero visible antennas or equipment) is the name of the game when doing RF wiretapping (for example, covert undercover w/ wiretaps). They’re driving among us constantly though usually just with basic VHF/UHF/800Mhz gear on board.
Lets see some proof of the equipment actually being inside this vehicle? I have no doubt they’re using a ‘Stingray’, but am growing extremely weary of seeing some terrible camera stills of this vintage Excursion with a camera/hydraulic tower assumed to be some sort of voodoo mystery cell-phone listening tool.
Cheers,
Also, I didn’t see anyone mention it (yet?) but if you’re seriously concerned about having secure OTA communications and don’t want to go to data/voip/VPN route (which is an excellent idea) I would start by digging into some custom PRL definitions for your flavor of phone.http://en.wikipedia.org/wiki/Preferred_Roaming_List
There are also secured phones in existence but they do come with a hefty pricetag because that sort of equipment doesn’t usually fall off the Feds trucks onto ebay.
Cheers,
the easiest solution is a cellphone jammer on the stingray. been meaning to order a couple of those from china anyhow
There is more than one problem here:
1. Tracking the individual.
2. Tracking a moving protest group.
3. Eves dropping on conversations.
The first and third are of greatest concern since tracking a medium to large group of folks is pretty easy even without the sting ray.
The first, tracking the individual in the group can be solved by using a mesh network based on wifi or bluetooth. The trick is getting enough of the people in the group to use the mesh instead of the cell towers. Message addresses not found in the mesh could be routed to the tower (or the sting ray). If the connections appear randomly from the crowd, that should foil tracking an individual, as long as they stay within mesh net distance from the crowd. I am really only mildly familiar with mesh networks. In other words, I looked at the OLPC implementation. In a sense, the TOR project has a mesh type structure with the routes of the signals being disguised.
The third problem, preventing eves dropping, can really only be handled with encryption.
Introduce PIM (passive intermodulation) into the system. A section of rusty fence or a board with diodes glued to it would work. You could also get a surplus TMA (tower mounted amplifier) power it up and put an antenna on it. Leave the input disconnected. The signal from the the stingray (and real towers) will enter the amplifier and get reflected back. All these things can introduce enough PIM to mask the signal from cell phones. The TMA method is probably illegal though, since it’s not actually passive.
to many comments to read them all..
but on XDA there is someone who made an app that can block/prevent your phone from connecting to one of these…
I’d go for hiding in plain sight. Give the system all the information they want. Just don’t give them an opportunity to make it useful.
what about an app that could encode messages into another format – text. then upload it to for example pastebin. Now you’d need the right paste and maybe a decryption code.
Let the app swap between 2G and 3G, and go into a ‘standby’ mode where the airplane function is activated (no radio activity). The app should also create a portable hotspot, so nearby users can use the connection.
Another option could be to record the message and encrypt it locally on the phone and then transmit it over the normal voice. again, without the key the encrypted message is useless.
The latter is much more easily said than done.
You have to remember that you don’t transmit voice packets (except in modern LTE networks with VoLTE), but compressed speech directly.
This means your voice connection has a very low datarate (6 kbps to 12 kbps usually), it is will go through a number of voice codecs (one on your side, 2-4 in the network, one on the receiver side), maybe even go through a VQE (voice quality enhancer) and thus any non-voice signal transmitted will degrade drastically. This leaves you with datarates of far below 5 kbps which effectively makes it impossible to transmit a usable voice signal over it.
Also, you cannot even make assumptions on what datarate you might get, even if you chose a strong 12 kbps codec on your side, the network might decide to transcode it to a weak 6 kbps codec.
It is thus a huge challenge to implement a data transmission system over such a voice transmission system.
Just spitballing some random thoughts. Pinging the tower or pseudo. using a phone, can you discern a difference in time?
think of like pinging a wire to locate a damaged section.
Can the same software that listens to your music for DRM data (think DVDaudio) or bootleg mp3s listen for an extra “echo” from bouncing from stinger to to tower. think of how old land line repeaters used to sound.
How about doppler shift?
if you walk 25 ft, the distance to
likely makes that a tiny percentage.
But with a stinger at maybe a 150 ft
then it becomes a larger percntage
or better yet, if the stinger is rolling
then it should provide the shift.
But bottom line? most everything in this section will evevntually be classified as obstructing an officer and interfering with an officer in his duties aid and abetting the commision of a crime. and will all become “extraordinary event” categorized offenses.
What the heck ever happened to good ol fashioned semaphore flags or morse blinker lanterns??? Sheesh… kids these days…
smoke signals, balloons, kites, pigeons, drums, old fashion passing notes, fortune cookies etc :P
IPv6 compliant and easily expandable bandwidth; but the latency and packetloss are technological challenges
I am sorry if this sounds a bit harsh, but I just have to say it: the whole premise of this article is ridiculous and the technical details either false or outlandish.
Lets start with every CSI viewers favorit tech-term: triangulation.
It is claimed, that the “StingRay” moves location to perform triangulation, but that is not the case, because that is not how triangulation works.
To triangulate, you have to receive the signal from at least 2 locations – but you have to do this at the same time. So moving location and measuring again (or even measuring constantly) does not allow you to triangulate a position. The only thing it tells you is if you are getting closer or further away and if you’re lucky it gives you a very rough estimation of the direction (not location!). That is if you are using an omnidirectional antenna.
If you have a directional antenna, you could get a slightly more accurate direction (again, not location!), but you would need to be stupid to move the car to achieve this because you could get the effect much more easily and quickly by just changing your antenna direction.
Radio communication systems are far to fragile and dynamic to make this useful, especially when the target is moving which drastically alters the received signal strength.
The more basic misconception is, that a “StingRay” device would be used to locate handsets and their users.
Well, is it? Certainly not.
As has been explained, these IMSI catchers work by offering the mobile station a better signal than they already have.
This means that they need to either send an extremely strong signal which will cause interference in a large number of base stations and require a lot of power – or it will require a strong signal in the vicinity of the target, which will require you to know where the target is beforehand. Why would you “triangulate” if you already know where the target is? I’ll take that one: you wouldn’t.
In a densely populated area the raster of base stations is usually 500 meters or less (and getting smaller all the time), which means, due to the line-of-sight advantage of the base station, you will need to be closer than that, even if your signal is much stronger.
In rural areas the transmission power of the base stations is higher and their line-of-sight advantage much higher, so your transmitted power would need to be enormous to steadily force a target with unknown location to connect to you (and you better don’t have any hills around).
So why would you even use a “StingRay”? There are basically 2 scenarios:
1) Military: you’re in a foreign country and have no possibility to access the mobile network, so you spoof it to get to your target.
2) Civilian: you’re doing illegal surveillance and have no possibility to access the mobile network, so you spoof it listen to your target.
Basically, there is one possibility to actually triangulate using an IMSI catcher: Your target is stationary for a long time, you have really good mapping data including 3D landmarks, you have a pretty good idea of the location already, and nobody will care if you’re degrading the service for a very large number of users.
Now, let’s get to the actual questions:
Can you tell the difference between a IMSI-catcher and the real base station?
Depends.
A good IMSI catcher will provide the same identification of network, cell and other parameters, so you won’t be able to tell it is one.
However, if you’re location is not precisely known and the IMSI-catcher in the close vicinity, the catcher will need to force your handset to increase its transmission power (which it can do). So if you have that data and you have good coverage, it will tell you that you’re likely not talking to your real network.
Lastly, if you’re using a modern data service like UMTS or LTE, the IMSI catcher will need to transport a lot of traffic from all the “caught” handsets – and it can’t.
So data service will degrade by a large margin and cannot recover for a long time. If your data rate permanently sucks – and usually doesn’t in the area you’re in – it might be a “StingRay”.
Next: Can it be fooled?
Depends on what you mean. Can you just not allow it to send? Certainly not.
But you can reasonably easily render it unusable.
There are a few scenarios:
1) Just set up your own IMSI catcher or downlink jammer. This is expensive and requires you to have proper equipment a stronger signal then they do – and they will have a strong one because they need to.
2) Kill all uplink traffic in the vicinity. This is expensive and requires you to have proper equipment and a reasonably strong signal, but is doable.
3) Kill _their_ uplink only. This requires some equipment (can be basically any radio on the frequency), a directional antenna and a knowledge of their location. This renders the IMSI catcher unusable. While you’re not directly disturbing the other handsets in the area, you will still effectively kill the network, because the “StingRay” can’t handle the incoming traffic anymore, but still jams all outgoing traffic in the vicinity.
4) DDoS. You need to create some high-priority traffic (calls), to a degree that they can’t handle it any more. You can either do enough calls so they cannot accept any further calls (this will result on a DoS for all users handled by the IMSI catcher). This will require a software defined radio with enough capacity, or a large number of modems.
And another question raised in some comments: Can the network operator make sure that you don’t connect to a rogue network?
Nope. 2G and 3G systems don’t offer authentication of the network to the user, so there is nothing the operator can do.
LTE however does have a PKI in place, so in theory the handset could chose not to trust unknown public keys offered by a LTE IMSI-catcher. In practice, likely no handset will do that.
And the last one from the comments: Can the operator detect a IMSI catcher and do something about it?
Yes they can. IMSI catchers like a “StingRay” will be immediately detected, monitoring infrastructure for that is available in any operators network. The strong downlink signal might or might not trigger alarms. But the uplink signals in the area will get much stronger and traffic much lower, which is a serious degradation any operator will catch, so if they are looking, it will be obvious what is going on. Good operators will quickly check their online monitoring or even send a tech on site and be certain that either a jammer or a IMSI catcher is in place. Then they would call the authorities, which might, or might not care.
What effect might a femtocell have on a stingray?
When hurled with sufficient speed and significant accuracy, you could probably shatter the windshield of the vehicle hosting the stingray. Or is that not what you meant?
Actually, if you could break out an antenna connection from the femtocell and then run the output into an amplifier (be kind, don’t go too broadband) and then run it into a very directional antenna aimed squarely at the stingray antenna pod, you could bake out the input amps pretty quickly (I’m guessing they’re not as hardened as they should be). Of course, that would break several laws several times over, so I don’t condone it… but for strictly academic purposes, sure, a femtocell could be an important part of a such a system.
Having done loads of experimenting with OpenBSC and GSM NanoBTS’s, I would say that it’s easier with GSM to intercept than CDMA – mostly because CDMA has fewer resold connections while GSM is all about interoperability. I also know that 4G/LTE is a huge want from Law Enforcement for a next generation of Stingrays as the technology just hasn’t been made small enough to fit into a van.
First thing about it I noticed was how it would route GPRS/Data packets. It’s going to go out whatever route it can which might not be the normal exit point for your normal provider. Second is that inbound calls from the outside world won’t work because it doesn’t seem likely that a SS7 connection back into the MTN is going to be wherever a stingray van is. Another is that since these are smaller cell sites, they will overload once you get over 6-7 simultaneous calls – so have lots of phone calls running and it’s likely that unless they have additional BTS transceivers, they will begin to run out of capacity unlike commercial cell nodes that have much larger capacity. Roaming is another part… if you’re all over the place, unless you see dark vans with antennas and steamed windows all over the place, it’s not going to take much to get away from said bogus cell and pick up the stronger commercial carrier. All of it works on the capture effect – just with that extra spice of authentication. You can also dial special cell carrier codes like *611 or whatever and see if it passes it.
All it takes is an awareness of your normal operating state to know whether or not you have a deja vu situation in the matrix.
Hey. Hope you see this message. Reply back ok?
Great for people like us but do you expect your average citizen to be proficient in operational awareness? Likely not.
I’ve noticed a lot of people saying that switching off GSM is an acceptable solution. For whatever it’s worth, there’s an upgrade for Stingray called Hailstorm designed to support 3G and 4G networks.
Maybe use redphone for android?
While this is a solution, a modern IMSI-catcher might just use DPI to detect that you are using a encrypted voip system, and simply drop its packet, which is a DoS that might either make you very nervous or simply force you to fall back to a standard call to which they can listen. They still know who you are, what you are doing, where you are, and who you are talking to, though.
These comments are going in the wrong direction.
Use the cell signal booster that you can buy from your cellphone provider. It basically just turns your phone into a VOIP handset by doing just what the Stingray system does–spoofing a tower. The signal will be stronger, so your phone will connect to it. There are plenty of ways to get an internet connection to it.
That is not necessarily true.
Those boosters come in 2 varieties, none of them actually spoofs a cell tower.
1) Repeaters: Those are “passive” boosters, they take a signal from a cell tower and repeat it towards you, and they take the signal from your phone and repeat it towards the tower. This is _not_ VOIP.
They have however limited transmit power. Large repeaters will do up to 30 dBm, but those are not used for home installations. The latter never go over 20 dBm. Only for a home installation with internal antennas a IMSI-catcher won’t be the stronger signal, but you might as well just use a landline or actual VOIP.
2) Femto Cells: Those are full blown base stations that are integrated into your providers network, thus they have their own allocated resources including their own cell ids and channels. They do not spoof anything. Their transmit power is very low (under 20 dBm), and a IMSI-catcher might just be stronger. Note that it does not actually “turn your phone into a VOIP handset”, even though it is usually connected to the network over a partial IP connection. Also note, that the IMSI-catcher might still be able to listen in nonetheless (it will receive your transmissions and might be able to decrypt them even though you are not connected to it).
If many protesters (in the same place) downloaded an app that would crowdsource the signal strength in the area, assuming that the Stingray can’t intercept more than half of everyone there (especially useful if people had been recording the area before the protest for lots of “clean” results), it could easily take background samples of the signal strength. It could “calibrate” the phone when it first starts up, assuming you know you’re not being tracked at the time, and scale up or down the signal strength of the “heatmap” based on the measurements for nearby areas. It would effectively crowdsource what the signal strength SHOULD be, and probably generate some pretty maps at the same time. If the current signal strength is off by a certain threshold for the current average signal strength of others with the app in the area, it could notify you, saying your signal strength is irregular compared to that of others around you.
all 4-wheel vehicles needs all 4 wheels in order to move forward…
assuming the vehicle speed is at walking speed;
the right hand side wheels bolts are easier to take off when moving forward…
assuming the wrench is (excessivly) longer then normal…
One thing I haven’t noticed anyone comment on is that the IMSI catcher doesn’t necessarily have to be a device which looks only at layer 3+ data. It could go all the way down to layer 1. Who’s to say that it also can’t talk directly to your phone’s baseband (or instead of a IMSI catcher, they may have deployed a different device). You have no control over your baseband code, and there may be vulnerabilities there.
If it can exploit your baseband to get access to your phone, anything you do at higher layers is moot — it could theoretically see your data pre- and post-encryption, for example.
I would say that the only way to not talk to such a device is to turn off your cellular radio. Use a different medium which doesn’t have the “if I talk louder, you’ll blindly communicate with me instead” vulnerability.
Frequencies
Uses a mobile cell an unusual frequency, like a guard band that should be questioned. And strong interference at other frequencies indicate the additional use of a jammer that will drive the target device on the frequency of false, non-perturbed cell.
Appearance of unknown mobile cells
, in reality change identification numbers in mobile networks only very rarely. When suddenly a previously unknown cell appears, perhaps even with an unusual indication of the location area, caution should be exercised. And especially short-lived cells are possibly IMSI Catcher in the identification mode.
Downgrades
The mobile connection is downgraded from UMTS to GSM, and / or encryption is turned off or reduced to unsafe methods? Stay away! Even if part of the network suddenly all the usual functions (such as GPRS, EDGE or HSPA) offering, or technical parameters from the rest of the network are different, that’s obvious.
Hold the phone in a cell
, an attacker in camping mode will attempt to tie the phone itself. One trick: the phone is informed that there are no neighboring cells, or it will not be available neighboring cells reported. Another approach is the manipulation of signal strength measurement values.
Abnormalities in cellular transport
The route incoming calls and SMS provides many IMSI catcher before problems. But also for outgoing connections there may be problems, like a sudden no caller ID is transmitted. A particularly sophisticated man-in-the-middle attack is hard to debunk this way: If the IMSI-Catcher emulates the terminal of the victim and the GSM-overs unchanged from the ends or in the real network.
Source: http://www.heise.de/ct/artikel/Digitale-Selbstverteidigung-mit-dem-IMSI-Catcher-Catcher-2303215.html
I’m curious, what’s the legality of these? It counts as eavesdropping, which is illegal without at least one of the participants knowing about it (all participants in most states). Without a warrant, the cops are committing felonies, correct?
Whenever we talk over the phone,voice goes through a digital signal
processor and turned into a bunch of 1s and 0s …if a
”key” were to be applied to this stream of bits the
resulting bits would be ”scrambled” .assuming the
processor on the device were fast enough this would
happen with almost no latency so there would be no
breaks.assuming the network is digital and only works by
these digital values and the network is symmetrical…m
eaning that the reverse happens on the receiver end….but
before the stream of bits is decoded by the DSP it is
decrypted using the designated key…the original message
would be otained on the receiver end…and if it were
tapped along the way it would make no sense.All what
one would need to do this is make an app that did this
with root permissions on both phones…I assume that
most mobile OS frameworks really abstract the hardware
for one/standardizes the method by which you interact
with the hardware irrespective of the manufacturer…all
what one needs to know is how to impliment the
algorithms in form of an app with the right permissions and share the keys…but I stand to be
corrected.
And what about a software defined radio, it could create many fake imsi’s and make them connect to imsi catcher, and overload it?
Also, the imsi catcher also has to connect to the normal network, would it be possible to catch their own signal and feed it back to them? Create a feedbackloop of some kind?