This “security” is so outrageous we had to look for hidden cameras to make sure we’re not being pranked. We don’t want to ruin the face-palming realization for you, so before clicking past the break look closely at the image above and see if you can spot the exploit. It’s plain as day but might take a second to dawn on you.
The exploit was published on [Mark C.’s] Twitter feed after waiting a couple of weeks to hear back from TP-LINK about the discovery. They didn’t respond so he went public with the info.
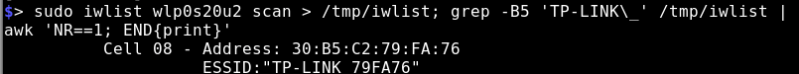
Shown in this image is the WR702N, a nice little router that’s popular in a lot of hacks due to relatively low power, low cost, and small size. During the design phase someone had the forethought to make a WiFi AP password that isn’t merely a default. But that’s where this went off the rails. They did the next worst thing, which is to assign a password that gets broadcast publicly: the last eight characters of the MAC address. This will be unique for each device, but it is also promiscuously broadcast to any device that cares to listen. The obvious next step is to script a scanning routine which [Mark] took care of with a one-liner:
We know what you’re thinking. Users should always change default passwords anyway. But our devices need to be secure by default.
[thanks Caleb]

















Damn it…
How can one be so ignorant, it almost feels like these systems were engineered by the famous workers of the “Wun Hung-Lo Factory”…
Oh…. wait :P
I’ve seen this on many devices, often on modem/routers provided by ISPs.
This right here, this is a pretty common thing for most ISP’s to do. Nothing new or earth shattering about a company using a mac address as a password.
…and partially the SSID?
is there any possible way to hack tp link i try this in my neighbors wifi but is was doesnt work
FYI, Orange in France has the same policy for default WEP on its LiveBox. Most of the orange customers are old people not even aware that they can change the default password.
This has nothing to do with “Old People”. What a Biggot.
He’s a bigot for showing concern for senior citizens who may not realize their networks are insecure?
No for assuming that age have anything to do with it – “digital natives” tend to be as clueless as older people.
So true… I know many “old” people that could blow my mind talking about tech security, and I know many 20-somethings that dont know that they can change a wifi password. Age != ignorance
Lets all just be politically correct here… and be ignorant trolls simultaneously. Age definitly has a factor in who learns and adapts to new tech. I know some tech savey seniors, but not nearly on par with the younger generations. Calling out a trend that does belong to a group of people does not make them a biggot, the person that assigns that trend as a rule to everyone in that group is. Some of you need to lighten up and realize trends exist within age,sex,nationality, whatever. Acknowledging these trends does not make you a racist or a biggot. Not acknowledging that is doesn’t apply to everyone dose. S10gregg@gmail.com
As opposed to a Smallgot.
As someone who has dealt with ‘twelve o’clock flashers’ of all ages for over 30 years, I have to disagree somewhat. OTOH, I have found a *VERY* strong correlation between age and technological cluelessness.
So, what dark magic can extract the MAC address from a physical device on another network? I suppose, that might need to be a skill testing question to enable posts/questions on a site like hackaday…. (I gave up after a couple minutes of googling – only Windows related answers and comments about MACs getting dropped via gateways)
The fact that’s it’s WiFi and broadcast in the air is enough.
Some kid halfway around the world finding the MAC address so they can use your WiFi is pointless.
Reported for the lulz
Missed that the default SSID also contains the MAC id.
If I’m not misinformed, the SSID doesn’t matter; WiFi in scanning mode broadcasts the entire MAC as well. That’s also what the output from the “one-liner” looks like; it displays both the entire address and the SSID.
Jolly good! That way we don’t even have to brute-force the 256 possible variations left to guess the 8ch pwd from the 6ch SSID.
Yup, in monitor mode you can easily see AP’s MAC address. You can also see clients’ MAC addresses, which is why MAC filtering option in router/AP is useless. You just grab some connected client’s MAC and apply it to your network card and AP lets you in.
Thank you. I’ve wondered that before but never looked it up.
MAC address is a protocol layer below TCP/IP.
The ESP8266 displays sniffed WiFi AP’s MAC addresses using AT+CWLAP.
When connecting to a wireless network, the SSID you choose is more properly called the ESSID. Your computer associates not to an ESSID, but to a BSSID broadcasting the selected ESSID. This is how multiple APs using the same ESSID work, your devices chooses the “best” BSSID broadcasting the ESSID you select. That BSSID is the MAC address of the AP.
This is what the second image is showing, that the ESSID “TP-LINK 79FA76” is being broadcast by Address 30:B5:C2:79:FA:76, which matches the MAC address on the first image, as well as the WPA key which is a substring of the BSSID/MAC.
So to answer your question, the MAC is being broadcast by the router/AP itself to everyone in range.
Thank you. I’ve also wondered how multiple accesses points share an ESSID but never found something that makes sense.
ARP Cache poisoning…..
What? Not required in the slightest. Beacon frames sent by the router to advertise it is there, contain the MAC address as the source address and SSID. Any ordinary Wi-Fi scanner will see this in less than a second.
Every wifi scanning tool will do this. MAC addresses of APs are broadcast unencrypted. No dark magic needed. Even 15 year old Netstumbler will do this.
Sorry, but “We know what you’re thinking. Users should always change default passwords anyway. But our devices need to be secure by default.” doesn’t fly…
It should always be assumed that ‘factory’ is not secure. When you buy a home, the first thing you should do is change the locks! Devices are no different.
Security is not a binary concept. That would be like saying that when you buy a house the locks will not be secure so you may as well make them out of cardboard painted to look like metal.
I think this is more like buying a home, turning up at the front door and finding the key taped to the door next to the lock.
Exactly!
I’ve seen this on a mate’s wireless router; the only difference being they used the ENTIRE MAC address as the password. Can’t remember what manufacturer/model of router off the top of my head (it was a fairly well-known brand though) but it appears TP-LINK aren’t the only ones to do something like this.
I’ve seen such things in D-Link, ZTE and other (based on same chipset) routers. Some are more clever and use simple algorithm to calculate password but it is also usually based on MAC address so someone reverse engineer algorithm and publish it on the Internet very quickly. Probably it’s the simplest to manufacture, MAC is the only variable you care about.
Funfact: They say this on their website
* Advanced Security
TL-WR702N provides WPA-PSK/WPA2-PSK encryptions, which
can effectively and efficiently protect the wireless network.
What makes the nano router more powerful is its
Pre-Encryption function which sets the initial SSID and
Password for users to protect their wireless security.
*
> Pre Encryption
Oh my. I can’t read that with a straight face. I wonder how could they even WRITE it
To be fair, although it’s mentioned here that many users are clueless about encryption and technology, that also means they can’t figure out how to grab the MAC and to then set that as password.
Or in other words such ‘security’ albeit poor will at least prevent those clueless neighbors from soaking up your bandwidth, which would happen i many cases if every device came with encryption switched off completely out of the box.
So although it’s a piss-poor implementation it’s at least something.
But from a manufacturing perspective, it would have been downright trivial for them to take the first four bytes of the MD5 (and, yes, I’m intentionally picking the very worst hash they could have) of the mac address instead, which would have been orders of magnitude better than what they did. The firmware could still be written such that it’s default key is based solely on the mac address (modulo the perturbation). Everybody wins.
Epic fail on security by TP-Link!
I have 4 TP Link routers of 3 models, none have a password that resembles the MAC. So, is it just this model?
Maybe not just that model but I grabbed my TP-Link TL-MR3020 and checked and the default password doesn’t match the MAC.
Guys, it’s not the MAC, it’s the SSID…put away those packet sniffers and just check your WiFi.
The password appears to be the last 8 digits of the MAC address.. please refer to the above article.
Combine with this https://www.shodan.io/ and lolz ensue
I don’t know what you all are getting so uppity about. That’s just the password to get on the network.
They’ll never guess the admin credentials, printed in light grey on the lefthand side of the same sticker.
No More Secrets! :-)
Then strike it out with a sharpie, so only you know what’s written there.
Hello!
Sure they will. It’s the classic one that all routers start with just to get into the box. Oh and sorry about hitting the wrong entry before getting here…..
Welcome! You must be new around here.
Me? Not on any of your lives.
In terms of security, that is worse than setting a password to carriage return.
Entering a carriage return into a HTML form without submitting it prematurely would definitely count as a test of skill.
\r
…unless you used carriage return as your SSID. Then it would be just as bad.
I think more intersting for me is : What linux used it to wrote the linux command ? Because he used ‘sudo’ the area of interest falls to some versions of Linux … I think is Ubuntu (also this remind me about blue $ from Slackware) … or maybe is Kali :)) ?!
sudo is pretty common on many distributions these days. On a multi-user system, it really is a more sensible system than having everyone share one root account and gives finer-grained control than su did. It also is a little friendlier to use, making it useful on single-user systems.
Repeat after me: Linux is a kernel, Linux is a kernel..
Ubuntu and Slackware are not Linux. They are a GNU/Linux distribution. Android uses Linux too, ypu don’t ser people calling it Linux, do you?
http://andreicazacu.com/2015/06/12/first-look-at-romanias-new-defence-and-security-strategy/ best hacking google map … “Repeat after me” :P
Just check my wireless network. The default password is the name of the SSID plus 4 secret additional characters. I just checked the MAC address of the router and the 4 “secret” characters are the 4th and 5th byte of the MAC address…
Neighbor must have the same ISP as me (TWC) because their SSID has the same format as mine and guess what. I’m posting from their network ;)
i have a small TP-link access point runnig and the default password is simply the SSID and 2 Charackters added. i havent checked the mac for these charackters. but its easy eough, when you only have to guess 2 charackters for a wifi password.
Interesting…
Another slick idea some people have had is the so-called SmartConfig or AirLink protocol by which you can send the SSID+PW to an ‘IoT’ device (originally TI’s CC3x00-based) without them being connected to that AP to start with.
The idea is very clever, in short they use UDP packet length (content is encrypted) to encode the protocol…
Drawback is that any other device listening to that will potentially be able to grab the PW too, defeating the whole purpose of WPA-2…
No, Users need not change the password on their wifi AP. A random password, printed on the device, should be good enough for most consumers.
* Good entropy, 32-40 bits is readily achieved. (here 0).
* easy-to-use for the user (just look it up on the device).
* Use a decent encryption that even with weeks of passive listening the key cannot be deduced.
This.
That complicates manufacturing, because you now have to record something in the device besides just the mac address. The mac address is less problematic, because many Ethernet or WiFi chipsets will have a little bit of config flash somewhere that can store that. If that space doesn’t have extra room, then there’s no place to store this random value, which needs to be printed on the label.
Better is to use a secure hash of the mac address. It’s security-by-obscurity, sure, so if the secret gets out, then it’s only marginally better. But it would have taken substantially more effort to discover that and it still raises the bar from doing nothing at all.
One solution: During the manufacturing stage, have the router print the sticker out on a printer over ethernet?
Looks like that router is also intercepting DNS requests. Wonder if it’s local or connecting to a DNS host.
Beautiful. Those databases of WiFi AP SSIDs and locations has now become a password database.
This doesn’t appear to affect my TP-Link MR3040.
Not sure which version you have, but my MR3040v2 sure is; just with a slight tweek to the stupidity.
SSID = TP-LINK_MR3040_
Default Password = P/N or 39893543
P/N for every MR3040v2 sold will be the same, so not much improvement but still better than the one reported above.
Guess you can’t use greater/less than symbols. SSID trailing value should have read “last-6-char-MAC”
tplink 3836 what is the password
I beg respectfully I want to hack tp link wifi password without wifi connect
You don’t even need to look up the MAC to get the password, the router is shouting it out loud in its SSID. Just prefix it with “C2”, the last two digits of their OUI.
My impression is that people more quickly personalize their SSID than the rest of the settings though.
Clear WiMAX APs used to have the same setup. I suspect it’s far more common than I’d like to ponder.
I’m not sure, should the router be secure by default? I like the idea that if I bought one 10 years from now at a flea market and the writing was all rubbed off of the label I could still get in after a full reset. I assume it’s as easy as any other router to fix the password after that.
Ok, so many ignorant computer users will never bother to change it. I’m sorry but that ignorance is willful. I have no sympathy.
TP Link: You have got to be Sh***ing me.
Thing is, the device requires programming to put it’s MAC address in, and requires a unique label for those details. So to add a randomly-generated, really random, and print that out, wouldn’t take any extra steps or hardware, just a tiny tweek. They could limit the used character set, to reduce ambiguity.
I suppose when you have millions of customers, and opportunity for a misprinted password label ends up costing money, but even so. At least this way there’s a fairly foolproof way of tech support knowing the machine’s password. If that lays the whole thing open to hackers, that’s the user’s problem, but is it necessarily TP-Link who’ll get the blame? They ought to, but the public have the “evil hackers” idea stuck in their stupid heads, so TP-Link will quite probably be able to shrug their shoulders and get away blameless.
Even if you explained it to a user using metaphors of keys and locks, for many people it falls under “computers” and is something they won’t take an interest in, even if it does make their lives worse down the line. No telling ’em. Some people treat their right to ignorance like a precious thing. To naturally curious people, like most of us here, it varies from baffling to infuriating!
EC:08:6B:56:89:08
What is the default password for TP-LINK_329C?
I gate wifi password fahad-Nat
I gate theatre wifi password fahad-Nat
Can you help with password for TP LINK AD3034 please
Is there any way for hacking router setup page password and username if connected without root