Every week there’s new a new website that has been compromised and the passwords of a few hundred thousand accounts have been leaked to a pastebin. To protect yourself you can change your passwords often, not reuse passwords, and use long compilcated strings; all of these techniques are far beyond the capacity for human memory, or even a Post-it note. Thus the age of electronic password keepers began.
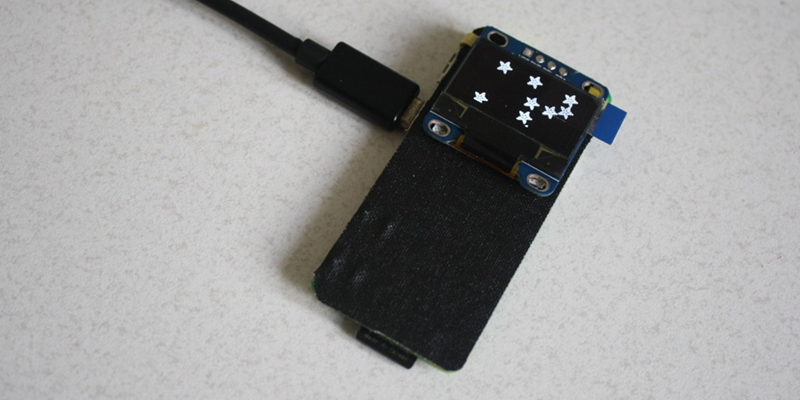
Electronic password keepers are simple devices that save your passwords and can recall them over a USB connection. The Raspberry Pi Zero functions perfectly fine as a USB device, leading [gir] to build the Raspi Zero WiFi Enable Hardware Password Manager for the Hackaday Prize.
This USB gadget uses pass, the ‘standard unix password manager’ to store all the passwords. Everything is controlled by a few buttons, a small OLED display, and of course the Raspi’s ability to become a USB HID device. This allows the Pi Zero to type passwords in just like a USB keyboard.
It’s a great project, and since the Pi Zero actually exists now, much to the surprise of its many detractors, the perfect entry for the Hackaday Prize.



















“…and since the Pi Zero actually exists now, much to the surprise of its many detractors…”
Brian you really need to open a window and stop breathing your own fumes.
Right? I got my first Zero the weekend after they came out (thank you random person who never picked up the one they reserved online at Microcenter), got my second (third and fourth) one because I was there, they were there… it made sense. Only paid more than $5 for one of them and that was only because I wanted a second set of adaptor cables.
Having had 4 of them and the majority of them were simply because we were in the same place at the same time doesn’t really sell me on the people that are butthurt they don’t have a retail store they can buy off the shelf and have to resort to online sales and aren’t realist enough to understand online merchants are in it to make money and can’t accept that things like shipping materials and packing labor cost money and no merchant is going to eat that cost so people can have a product with a very low profit margin at it’s advertised price.
Keep feeding the trolls Benchoff. Reinforce those fragile egos now so they grow up into the entitled pricks their parents always wanted them to be.
All I’m saying is that I’ve had Zeros for going on 10 months now… don’t see how someone can carry on about availability when I have direct proof of their existence.
Not talking about unicorns here. Theres been plenty of proof of existence all along. It’s like saying food doesn’t exist because you’re Ethiopian and haven’t seen much food in your life when the reality is that you are just unlucky enough to live someplace without much food. Meanwhile- in other parts of the world…. they throw that shit away by the plateful.
And yet they were rarer than rockinghorse poo in much of the world. Unless you wanted to buy one on ebay where they could be had for $40.
Incidentally that’s a good indicator on availability. If something is selling for 8x the retail price on ebay then there’s an availability problem.
You got lucky, don’t get cocky.
I had the same experience as him. I bought them at Microcenter multiple times, and I even passed on them multiple times. Sure, I had alerts set at online vendors, and in the 5mins after the notification they were sold out, but brick and mortar was easy.
Good for you, where can I find a microcenter in the UK?
Link to a person actually claiming they didn’t exist or STFU.
No. My complaint is with people that couldn’t accept that it was totally infeasible to get a $5 bare Zero ‘for the advertised price’. Shipping alone is more than the sticker. Online merchants have to make their buck too and the only way to really do that was to sell as a kit and spread the profit margin around to several individual items.
Plain and simple- early on it was hit-or-miss if my local MicroCenter would actually have any bare Zeros in stock, but outside those first few weeks there was never a time where there was less than 5 Pi Zero kits on the shelf for those that wanted to pony up an extra $15 for a wall wart, micro>usb adapter and mini>HDMI adapter.
They were out there- but just like everything else Pi… the price on the box isn’t all you’re paying. Pick up a Pi3 and you’ll need power, SD, HDMI etc. until you have what you need for your purpose. By the time you’re done it’s more like $50 than $30.
He’s actually correct – For the first time ever, I see they are in stock. (ordered one, FINALLY!)
He’s not right… see my comment up above.
He’s right, see my reply to your comment that you were in the right place at the right time.
Now everyone can finally get the things.
I live in a south-east Asian country. I ordered mine from the UK a few weeks after they were announced. I have ordered more since then. Now I have four. Bite me.
lol
This is a great start. A Pi Zero based password manager would easily exceed the capabilities of projects like the mooltipass at a lower cost due to more RAM and Flash, faster CPU, and the ability to use Open Source crypto software for Linux. Integrate it with some browser plugins from mooltipass or keypass and its good to go.
The mooltipass uses a smartcard – something I am quite envious about ;-P
You can’t use a USB reader for that, since you need it for the HID functionality.
If anyone knows a way to / a driver for interfacing a smartcard with the Pi’s GPIO – please let me know!
The smartcard used in the mooltipass project has an SPI interface, which the Pi also supports. It would be a matter of finding a good Open Source library for the card features, or writing one (not a big task). It’s also easy to add a small Oled or TFT display via the I2C pins on the Pi so you could implement a user interface on the Pi also.
Okay I see you already have an I2C Oled running :-). Fingers faster than reading comprehension.
#OccupyPiZero #WeAreThe99% #hashbrowns
Apart from the Pi-zero stock problems….
Is this a safe way to keep track of passwords?
It will work, however I have one sidenote;
Many of the password attacks on user machines, consist of keyboard loggers.
As a safety precaution this device is just as vulnerable as any keyboard interaction. Many PC’s in public places (hotels/internet cafe’s/schools) may have keyboard loggers.
I use a package like keypass to store my passwords and use ^C and ^V to reproduce complex passwords. A keylogger will log ^C and ^V, which isn’t of much use.
(And I know that this won’t work on a public computer)
The project however, is neat and nicely executed!
Any good keylogger can (and will) access your clipboard.
To eloberate: This of course only works for software keyloggers, it doesn’t protect against hardware devices.
However, If you are compromised to the point of a keylogger, you have to wipe your system. If it’s a software keylogger, they have compromised your machine. If it’s a hardware keylogger, they have ALSO compromised your machine, and if you take security seriously, the machine should probably be destroyed physically.
The reason I see copy-pasting as less secure than manually typing the password is that the passwords stays in the clipboard for some time, even if you “erase” the clipboard afterwards, and any app (and in some circumstances, if you forget having the password in the clipboard, websites also), can easily access the password while it’s in there.
The only real defence against this kind of attack is two-factor authentication, preferebly based upon a “dumb” device as a Yubi-key. I do however personally prefer to go one step further, and prefer “dumb” TOTP devices, as the Yubikey software requires authentication over Yubikey servers as far as I know.
You can use open source software from them to use yubi keys locally with pam.
Could always use a method like KeePass2: type part, paste part. Each password gets divided into part that gets pasted (always the same part, otherwise statistical analysis problems arise) and some keystrokes that use arrow keys, home, end, etc, to insert the rest of the password into the right place, and it might even delete extra characters.
But no password manager will work with a Ring 0 key logger. The only thing that works then is two-factor.
The pi password manager could insert some left/right/home/end keys to “type” the password in a random order, even insert some incorrect letters and delete/backspace/shift-select them out later. In theory, a keyboard logger could decode all of that, but how many currently do?
If a human reads the log file it is very clear what is going on. Unfortunately there is no easy way to address this in a portable way. I gave it some thought as well in the past.
`pass` stores the passwords as gpg2 encrypted files. this leaks metadata (depending on your format of choice, at least the website, maybe the username too), but not the passwords itself. Against software keyloggers, there isn’t much you can do, other than stay clean. modern ones won’t (just) read keypresses any more, but read out the fields from the browser – which voids the random-order / delete-chars method.
if you use another password manager, feel free to implement a wrapper around it ;-)
(the code on github works, but isn’t up to date – that will get fixed today/tomorrow)
I feel honored, thanks!
I pushed a new project log with renderings of the PCBs – both the version including an ESP-12e module, and one without.
Still haven’t received the recently ordered FPC connector, so the footprint for that is a placeholder.
If something like this also ran various 2 factor authentication programs and also typed those in, that would be very cool.
I got a Pi0 recently too, so it wasn’t just me, who couldn’t find them!