We’ve always been a fans of wargames. Not the movie (well, also the movie) but I’m referring to hacking wargames. There are several formats but usually you have access to an initial shell account somewhere, which is level0, and you have to exploit some flaw in the system to manage to get level1 permissions and so forth. Almost always there’s a level where you have to exploit a legitimate binary (with some shady permissions) that does more than what the regular user thinks.
In the case of CVE-2017-8386, less is more.
[Timo Schmid] details how the git-shell, a restricted shell meant to be used as the upstream peer in a git remote session over a ssh tunnel, can be abused in order to achieve arbitrary file read, directory listing and somewhat restricted file write. The git-shell basic idea is to restrict the allowed commands in an ssh session to the ones required by git (git-receive-pack, git-upload-pack, git-upload-archive). The researcher realized he could pass parameters to these commands, like the flag –help:
$ ssh git@remoteserver "git-receive-pack '--help'" GIT-RECEIVE-PACK(1) Git Manual GIT-RECEIVE-PACK(1) NAME git-receive-pack - Receive what is pushed into the repository [...]
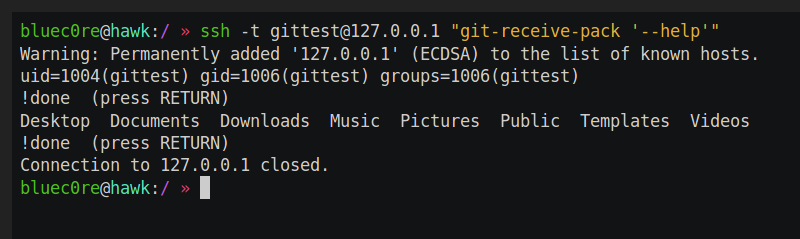
What the flag does is make the git command open the man page of git, which is passed on to a pager program, usually less. And this is where it get interesting. The less command, if running interactively, can do several things you would expect like searching for text, go to a line number, scroll down and so on. What it can also do is open a new file (:e), save the input to a file (s) and execute commands (!). To make it run interactively, you have to force the allocation of a PTY in ssh like so:
$ ssh -t git@remoteserver "git-receive-pack '--help'" GIT-RECEIVE-PACK(1) Git Manual GIT-RECEIVE-PACK(1) NAME git-receive-pack - Receive what is pushed into the repository Manual page git-receive-pack(1) line 1 (press h for help or q to quit)
Press h for help and have fun. One caveat is that usual installations the code execution will not really execute arbitrary commands, since the current running login shell is the git-shell, restricted to only some white listed commands. There are, however, certain configurations where this might happen, such as maintaining bash or sh as a login shell and limit the user in ways that they can only use git (such as in shared environments without root access). You can see such example here.
The quickest solution seems to be to enable the no-pty flag server-side, in the sshd configuration. This prevents clients from requesting a PTY so less won’t run in an interactive mode.
$ man less LESS(1) General Commands Manual LESS(1) NAME less - opposite of more
Ironic, isn’t it?















There’s a LESSSECURE environment variable intended to deal with precisely this sort of issue. (Or you can always use a less featureful pager.)
When setting up a restricted account of any sort, you should think about sanitizing the environment (especially the PAGER and EDITOR environment variables) and if you decide to set less as PAGER, you should probably set LESSSECURE to 1.
That said, I think the git help mechanism can also be told to open documentation in a web browser, so securing less may not be enough.
I get why it’s called that…but setting a variable called LESS SECURE to true just feels wrong.
Ha, We use to use the same tricks back in the 90’s to pop universities, well that and LD_LIBRARY_PATH via telnet, or tcp sequence number guessing, or vi, oh the sendmail uudecode bug was cool too. Nice to see!..
On the war-game subject you should check out https://game.hacker.nz/ Its a war-game where you hack a power plant with the goal of shutting down the reactor, well once you have hacked the other 30 hosts in the different network segments.
Should be blamed on SSH really.. These kinds of lines should not be needed:
no-user-rc,no-pty,no-X11-forwarding,no-port-forwarding,permitopen=”127.0.0.1:80″,permitopen=”127.0.0.1:21″,command=”/bin/echo one command”