If you’ve done anything with a modern Linux system — including most variants for the Raspberry Pi — you probably know about sudo. This typically allows an authorized user to elevate themselves to superuser status to do things.
However, there is a problem. If you have sudo access, you can do anything — at least, anything the sudoers file allows you to do. But what about extremely critical operations? We’ve all seen the movies where launching the nuclear missile requires two keys counter-rotated at the same time and third firing key. Is there an equivalent for Linux systems?
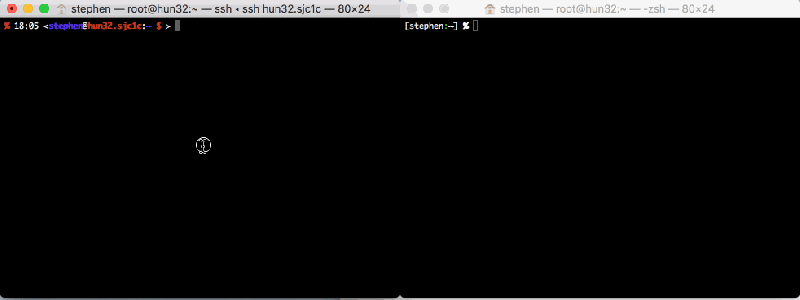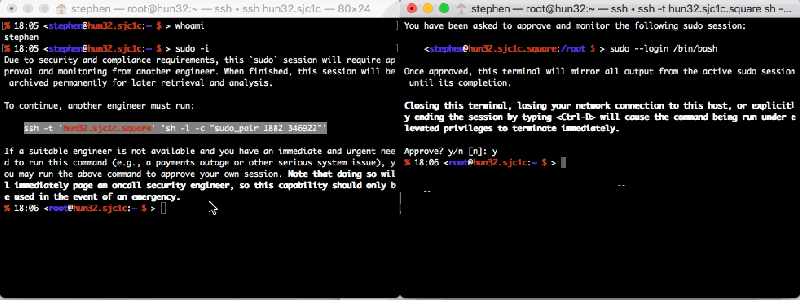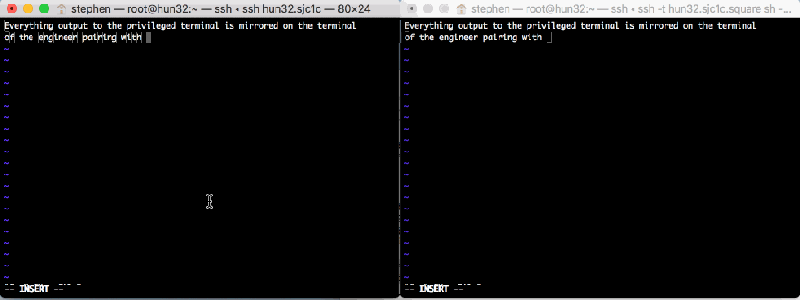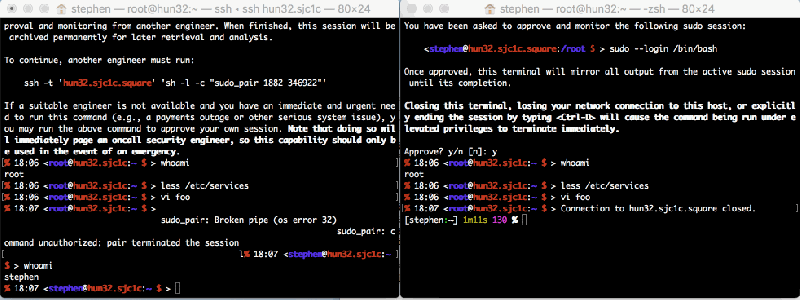
It isn’t exactly a counter-rotating key, but the sudo_pair project — a prelease open-source project from Square — gives you something similar. The project is a plugin for sudo that allows you to have another user authorize a sudo request. Not only do they authorize it, but they get to see what is happening, and even abort it if something bad is happening.
Actually, sudo is a little more complicated than most people think. If you read the sudo manual, you can authorize certain users or groups to have very specific access, if you know how to set it up. You just don’t see it done very often. For example, you can allow a specific program to run as root for any user (or subset of users) without granting access to everything. That means sudo-pair wouldn’t have to be used for total root access. You could use it to monitor usage of specific critical applications.
The easiest way to understand exactly what’s going on is to watch the demo below which shows two users’ screens. One requests a sudo and the other approves it (click on it to view full size).
The system is pretty flexible, but because it is in prerelease there are a few steps to setting it up that you can follow in the project’s README. A script checks to make sure you are not trying to approve your own session and can do other custom processing. This leads to a chicken-and-egg problem. You need to protect that script, but people do need to be able to run it. The system allows your session to execute the script without a pair. There are other ways you can exempt certain things, too. For example, an on-call administrator group can be exempted. Note that root is always exempt, but you really shouldn’t have many people with full root authority, if you are dealing with things sensitive enough to need this.
The code is in Rust and there’s nothing prebuilt yet. This is a very useful feature if you have multiple users managing something important, but it is a little early for a production environment. In particular, as the project warns, misconfiguring sudo can lock you out of a machine, so tread lightly and — of course — you have backups. Right?
If you are running something critical, you really need to understand sudo and configure it with or without sudo-pair. It is possible to restrict operations at the user and group level and virtually no one should have complete root access. Even if you are the only user on your Raspberry Pi, if it is controlling something critical you should force a hacker to at least break multiple passwords to get through. You might even consider multifactor authentication. You can even pull that trick with an Arduino, oddly enough.
















A tool I would have really loved 25 years ago when I was teaching *nix administration. It would have saved me much time in rebuilding/reconfiguring systems.
Today, not so much need for me since most all systems I work with now are single user and/or embedded, but it looks interesting.
seeeeriously? in modern teaching settings you use a vm that you boot from a snapshot… user hoses the vm? rollback and reboot, mistake gone.
The first exploit for this will be named WOPR.
How about a nice game of chess?
Turn your key, sir!
A solution in search of a problem.
Exactly. My employer has locked down permissions so tightly that it is practically impossible to do any useful work.
Yes, but just think how safe you are, doing things can be very unsafe.
One of my worst privileged-access experiences was when a co-founder came and sat next to me to work through fixing a database problem. I was up pretty late that night restoring things from backup. That lesson stuck with me – the problem often isn’t that it’s too easy for someone to do something wrong with privilege, the problem is often that you shouldn’t be doing some operations manually with privilege in the first place. Being able to reach in with sudo and manually fix things is a crutch which allows you to keep innately-brittle systems rolling, and this makes it feel safer without actually making it more robust.
I have always seen sudo as a needless pain in the ass. If I need to be root to do something I just su to root and get to work. Typing sudo in front of every command would have me ready to shoot somebody in minutes. On idiot systems that make it problematic to work that way, typing “sudo su” gets me what I want. The best protection and safety lies between your two ears. Sudo just fosters a false sense of security. The thing to definitely not do is to run as root when it is not actually necessary. I developed habits back on Edition 7 unix and see no reason to change them.
> Sudo just fosters a false sense of security.
No, it does not. The problem is that “sudo su” is usually allowed, and it should not be. Sudo is very useful for a DBA to run “service oracle restart”, to the backup admin to “sudo service tsm restart”, to the webmaster to “sudo service httpd restart”, and so on. You limit root access to a few needed commands, not every single possible command.
Other than that, it keeps audit trail. If you run “sudo su” and some other user did the same, who wrecked the system? It ran as root, so nobody can know for sure. But if you run “sudo fdisk /dev/sda”, and someone deleted the partitions on sda, anyone knows for sure who did it.
On our shop we almost implemented a rule that everyone running “sudo su” would have to pay a pizza for all the other coworkers. It would have worked nicely.
Was “sudo bash” OK?
C’mon, folks, you can do better. There’s sudo -s for that. It’s in the man page (I know, I know).
I’m definitely one of those old farts who don’t jump on every bandwagon out there (don’t ask), but sudo is one of those “new & shiny” I adopted pretty quickly. And Git. Sudo simply makes sense (e.g. allowing a “normal user” to invoke a backup script).
I always do sudo emacs, and m-x shell from inside there
I am totally with you. That tool sticks around for ages and maybe it’s use on single user machines is limited. Sudo has so many capabilities inc. safe fileediting for users which prevents shell escapes in popular editors.
Some people should definitely lower their voices, as they obvoiusly have too little experience to fully appreciate the potential of this tool. And by the way sudo -i is mostly superior to sudo -s as it brings up a full login shell (including all profile loading fun).
If you think sudo brings a false sense of security you’re probably right, but if you put more effort in configuring sudo you can get that fixed easily.
The one place where sudo has merit is where you want to open up a specific command, or a few specific commands to users who you don’t want to hand the root password to.
It’s a good thing that this sudo thing wasnt in older Linux systems.
Indeed. Back in those days you used the setuid bit and carefully wrote the commands that you then made available to non privileged users. Sudo just sucks, especially when crammed down your throat by some of these “modern” clueless systems. For the purpose of making a few specific commands it is fine and more convenient.
I see this implemented in drug dispensing hardware quite rapidly, among other things. Many policies require dual control of whatever supstance, material, or information is being used, administered, moved, transferred, etc. This is just one step more towards our software acting like our hardware. I’ll be surprised, for example, if SELinix doesn’t include this very soon.
This actually took place (and still does) on IBM mainframes. You know the fastest, most secure system in the world for those same 50 years. But you probably think health insurance, airlines, banks and credit card use sql variants. How wrong and under educated you are
This is the funniest thing I have read today! Thanks for the giggle!
I wouldn’t have much use for this on my Ubuntu PC, but it might be useful in ATM machines and cash registers, etc.