If you haven’t been following the Nintendo Switch hacking scene, the short version of the story is that a vulnerability was discovered that allows executing code on all versions of the Switch hardware and operating system. In fact, it’s believed that the only way to stop this vulnerability from being exploited is for Nintendo to release a new revision of the hardware. Presumably there are a lot of sad faces in the House of Mario right about now, but it’s good news for us peons who dream of actually controlling the devices we purchase.
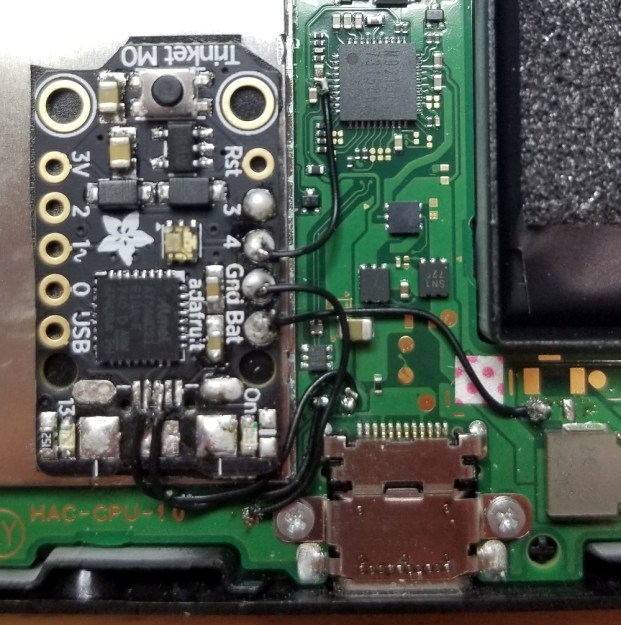 To run your own code on Nintendo’s latest and greatest, you must first put it into recovery mode by shorting out two pins in the controller connector, and then use either a computer or a microcontroller connected to the system’s USB port to preform the exploit and execute the binary payload. It’s relatively easy, but something you need to do every time you shut the system down. But if you’re willing to install an Adafruit Trinket M0 inside your Nintendo Switch, you can make things a little easier.
To run your own code on Nintendo’s latest and greatest, you must first put it into recovery mode by shorting out two pins in the controller connector, and then use either a computer or a microcontroller connected to the system’s USB port to preform the exploit and execute the binary payload. It’s relatively easy, but something you need to do every time you shut the system down. But if you’re willing to install an Adafruit Trinket M0 inside your Nintendo Switch, you can make things a little easier.
Stemming from work done by [atlas44] and [noemu], the final iteration of this mod was created by [Quantum-cross]. The general idea is to strip down the Trinket M0 board to as small as possible by removing the USB port and a few capacitors, and then install it inside the Switch’s case. By wiring it up to power, the back of the USB-C connector, and the controller connector, the Trinket can interact with all the key components involved in the exploit.
You can even use the Switch’s USB port to update the firmware on the Trinket to load different payloads, though in his walkthrough video after the break, [xboxexpert] mentions eventually this won’t really be necessary as the homebrew software environment on the Switch matures. Indeed, there will almost certainly come a time when performing this exploit on every boot of the system will be made unnecessary, rendering this modification obsolete. But until then, this is a pretty slick way of getting your feet wet in the world of Switch hacking.
It was only six months or so back that we were reading about the first steps towards running arbitrary code on the Nintendo Switch, and just a few months prior to that we saw people experimenting with controlling the system with a microcontroller.
















” Presumably there are a lot of sad faces in the House of Mario right about now, but it’s good news for us peons who dream of actually controlling the devices we purchase.”
A short term “I got mine”. Long term learn lessons and future customers have it harder.
Except we’ve already been through this dance a few times. Making a perfectly impenetrable consumer device whilst still reaching release deadlines and prices is thankfully intractably hard.
True, which is why security has never been about absolutes, but long enough til what’s being secured is no longer economically viable, for either party.
Making things nearly impossible to run third party software on actually shortens the lifespan of the hardware, which is part of what any manufacturer wants–for you to have to buy a new thing. At the same time, making homebrew development possible gets more people interested in the platform. The PSP has a bunch of amazing homebrew stuff and people are still developing for it. The Vita never got a meaningful foothold in the US market, and it’s partly because Sony locked the platform down so tightly.
The reasoning is almost always, “prevent piracy.” Locked-down hardware does that for awhile, but it’s eventually cracked, and once it is, the manufacturer has far fewer cards to play. Forced software updates? Well you’ll just get more and more elaborate firmwares/hacks/whatever.
On the flip side, if the manufacturer carves out a third party development niche in the ecosystem that allows people to write general purpose software, or homebrew games, or ports of DOOM or what have you, then you can appease a great deal of people while still keeping control of the platform.
Basically, if you lock the place down iron tight, you create a huge incentive for people to break your system, and the more hardware-bound you make those locks, the fewer options that you’ll have to change the system later. That means that when the people who are trying to break in–and they will, they literally always do–aren’t going to care whether their hack ultimately enables piracy or not. If you the manufacturer create a walled garden of sorts within which anyone can develop in, the impetus for piracy hacks applies only to people specifically interested in piracy rather than homebrew. There are far fewer people out there who are looking for that specifically than there are people who have an interest in homebrew.
Nintendo devices have relatively low-hanging-fruit security. No ASLR and NX or compiler security in a lot of places.. Zero isolation for most of the memory-map.. Mostly it’s just signature checking and chain of trust starting with the poorly written Nvidia bootrom which from what I read was defeated shortly after release by failoverfl0w. Others have actual entire exploit chains to root from lowest privilege memory..
Meanwhile Xbox One and even the 360 has encrypted and hashed RAM and anti-glitching.. PS3 even had hardware isolation..
The switch has NX, ASLR, heavy code signing, a very well hardened boot chain, a surprisingly effective trustzone implementation, and an extremely well built microkernel with a small attack surface. The flaws being exploited are due to Nvidia mistakes, Nintendo made very very few.
“in some places” + “Mostly it’s just signature checking and chain of trust starting with the poorly written Nvidia bootrom”
fail0verflow published details of their exploit and have a CVE.. There was a earlier team who escaped from lowest privilege mode and gave a talk on the entire design at CCC.. T.E.E. does nothing but PKI service just like it does on Android phones and the OS for it is written by third parties just like everywhere else.. Every time ANYONE fuzzes the service interface for one mounds of buffer overflows and dumping come from it..
By the way 100% of my living comes from bug bounties and I have houses on opposite sides of the planet..
Yes, I am aware of that talk, because some of my work and the work of others in my team went into it. fail0verflow doesn’t have a CVE, we do. We were the ones that disclosed it. See: https://github.com/ktemkin/fusee-launcher, and more specifically https://github.com/ktemkin/fusee-launcher/tree/master/report for the report that got us CVE-2018-6242. We worked closely with fail0verflow during the disclosure process as they discovered the vulnerability separately.
You might want to check those URLs, both come up 404… Only one project comes up for ktemkin and it’s not this. Fusee-launcher comes up here->
https://github.com/Cease-and-DeSwitch/fusee-launcher
Every time someone feels the right to brag about ridiculous stuff like “having houses on both sides of the planet” I just dismiss their entire comment as bullshit. You just print general knowledge stuff that everyone with a little interest can find on the internet.
Like said below, version 5 brought KASLR, secure TrustZone, as well as some pretty heavy server-side stuff for when it does inevitably get cracked. Nintendo has handed the homebrew scene on Switch commendably. It’s Nvidia’s fault for these holes in the system.
Thankfully I am no console player. But it would make me angry to know, that my money as a buyer of this stuff goes so much into development of anti-features, features that prevent me from having full control over devices I bought. It is not lend, rented or leased but SOLD.
why spend so much on a trinket when you can use a digi spark for 2$. aliexpress has a ton of them and they have enough i/o for this project.
Why stop there, just deadbug an attiny85 and save another dollar!
But like why spend time bitbanging usb and fitting everything into memoy when you can have an abundance of it plus a nice rgb led and reset button?
Because that’s the way of Real hackers? ;P
Because the community was asking me to do something in a short amount of time and getting it from outside of the USA was not an option
“getting it from outside of the USA was not an option” – so it was a requirement to spend more money then necessary? Like fans of overpriced Apple products?
It was a requirement for me to jump on this modification prior to someone else because I like to be on the bleeding edge of everything as to now lag behind in the times. I also have been really wanting to get my hands dirty inside the switch as far as locating the points needed to deploy the correct code from the m0. Nothing else needs to be said as to my methods of acquiring the chip as an extra $15 bucks did not bother me, the amount of time I would have waited for a parcel to pass customs however did bother me.
Thank you,
Aliexpress takes ages to get something. If you want it now, it’s worth the premium to order it from within the country. Adafruit sells trinkets for $7, the $5 difference is worth it to start on the project by the weekend rather than next month. It’s not like this guy is going into production with the part, it’s just for a one off build.
You’d be better off just leaving the website and never returning.
You’d be better off just leaving the website and never returning.
Funny how your post is still here, and this project was made by an independent third party. How does HAD being owned by SupplyFrame affect the component choice of some random tinkerer?
Poor trolling effort, try again later.
They actually only removed one LED and its resistor. All the capacitors are still in place on the photo.
I actually only removed the leds resistor the led remained
It says in the installation notes the caps were replaced with physically smaller ones.
Yes at first if you want to replace the metal shield you will need to do that however after I left it off it doesn’t matter.
If anyone has any questions on doing this or performing this modification on your system this is xboxexpert and I am here to help you just ask on the YouTube channel and I’ll try to respond to each question as fast as I can.
Good work :)
:(
Don’t frown. Mine’s worse.
Haha, I think the SMD stuff is (always) forgivable, but your GND and pin 4 on the trinket are very cold solder joints, just let the wire heat up a bit more and it’ll look great :)
I would put a thumbs-up icon but I’m not sure how haha
Then why even post a comment that’s not relevant to the subject
This is an amazing mod that will work wonderfully
for a few weeks until nintendo patches it
If they could they already would have.
Unpatchable
*Literally* unpatchable :)
you sure? sounds like something easily patchable with a firmware change
Yes, it is literally unpatchable. The flaw is not in the “firmware”, it is a bootrom vulnerability. It exists in maskrom burned in at fab. Nvidia included fuses intended for patching the bootrom but they can only be burned prior to the chip leaving the fabrication site. This means that any switch using one of the vulnerable chips is vulnerable permanently, full stop. This bug also does not exist in just the switch, it exists in almost every tegra chipset shipped for the last decade.
Unpatchable. :)
This is the equivalent of going into the boot selection menu of a PC and selecting a new boot device for that one boot, except this loading boot bios process is baked into an ASIC that isn’t flashable to protect from this attack vector. If I understand it all correctly.
Only way Nintendo can patch this is create a new Hardware revision of the Switch. Current version can’t be patched.
So in other words don’t send one’s unit in for repairs. ;-)
Was news to me, it must be hard being so far on the bleeding edge, that you have no input other than “I knew about this before it was cool.”
Welcome to being a technological hipster.
Story of every dying console system since the use of CD in consoles, This is just a selling point for Bintendo to get rid of excess stock and cash in then release their next iteration “INSERT RANDOM BRAND” has never played this game before.
I am all for being able to use your hardware the way you want but the vast majority WILL use this to play stolen games….
Most games now are just rubbish with lots of ART and Music Quicksaves and Checkpoints, remember persistence and skill ….. Everyone gets a trophy now….
Piracy should be falling off then since everything is now…”junk”! *wink* *wink* *nudge* *nudge*
Participation Reward Awarded…!
Thankfully someone released.
There is a “hacker” going around calling themselves the wizard queen of the switch going on and on about exploits like this without releasing.
Honestly people like qwertyioup, smea are becoming Kim Kardashian famous (name is known and nobody is really sure why).
It’s getting tiresome. So I welcome an actual release.
check out my switch at https://www.youtube.com/watch?v=O90mQOZm5nU
the whole story that I bought it off of ebay as way it was. I am planning to mod my other switches with trinket m0.