Security cameras used to be analog devices feeding back into a room full of tiny screens and commercial grade VCRs. As technology moved forward, IP cameras began to proliferate. Early models simply presented a video stream and configuration page to the local network. Modern models aimed at the home market differ however. More often than not, configuration is through a strange smartphone app, and video is accessed through third-party servers. It’s all a bit oblique, and so [Alex] decided to take a look under the hood.
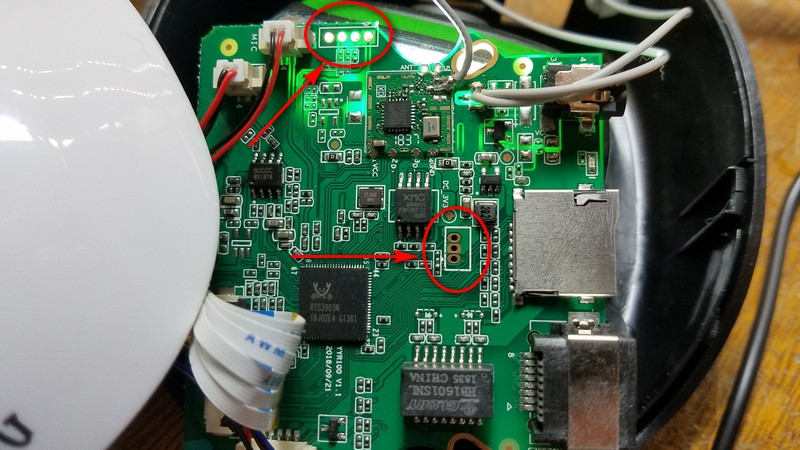
The exploration begins externally, with [Alex] capturing data sent to and from the camera with Wireshark. Straight away, red flags are raised. For as yet unknown reasons, the camera attempts to resolve Google, Facebook and Alibaba servers over DNS. Disassembly then follows, revealing that a serial terminal with root access is available. [Alex] uses this to probe around, uncovering the firmware update script and a way to decrypt said updates.
The work thus is a great example of how to approach hacking a given device from first principles. The overall goal is to find a way to gain complete control over the camera, reprogramming it to serve up video as [Alex] wishes, rather than to a distant third party server. It’s not the first time we’ve seen an IP camera hacked, and we doubt it will be the last. If you’ve got one cracked, be sure to let us know.















“the camera attempts to resolve Google, Facebook and Alibaba servers over DNS”
No need for camera hacking. Sounds like it came pre-hacked!
Not really, I’ve seen this lots of devices (IoT, TV, Cameras, etc.)
Just because it’s popular, doesn’t make it right…
Agreed,
This is not a acceptable evil.
A childish thing to say without providing an effective alternative.
depends on the customer, how much they want to spend and how much they care about privacy/security.
@Alex A childish thing to say that there is no problem unless there is a fix.
Resolve and ping to google and some other addresses can also be a quick and dirty method to say that « internet access is up ». It’s not a perfect method but I’ve seen that in many alerting scripts
Most likely this is a quick way to check if the internet connection is working. I did something similar in the past, but not for a product of course.
Except in this case any competent installer would make sure the camera doesn’t have a path to the internet.
Any competent installer wouldn’t be using this cam which is aimed at the home market.
You know this is the use case for this product?
Lol
More likely it’s confirming internet access. It’s unlikely anywhere in the world blocks all three. (I’m thinking places like Iran).
Of their own servers are/were less than relatable during testing this makes perfect sense.
Of the various IoT devices, IP cameras might be what I find most concerning. The low price combined with multitude of companies making then, lack of transparency, and capability for surveillance really bugs me.
I’m always interested to see what the hackers here turn up digging through these and I hope we might one day get to OSS firmware for these like DD-WRT but for IP cameras.
I would be interested in trying to design a low-cost, high resolution, open hardware, open software, IP Camera.
I started building one, but it turned out to be more of a time lapse camera. The project start is here, follow my blog for an update coming next month:
https://miscdotgeek.com/time-lapse-security-camera-raspberry-pi-zero-w/
Something based around a Pi Zero W might be a place to start. I’ve seen some efforts based around this. At least that would be more open than what is currently out there.
Yeah I forgot to mention that- mine is a Pi Zero W w/ Camera module.
Exactly what I’ve been doing for the last couple years. Tricky part is getting it to work well with the server software. This is what most hackaday devices seriously lack and is a huge programming commitment. I spent years of my life and over a $100k developing this software, to which I GPL for the world :)
https://github.com/physiii/open-automation-gateway
https://github.com/physiii/open-automation
Find a way to get hold of the hisilicon devkit.
This is the chipset of choice because Hisilicone prevoide you with an end to end solution to roll out your own cheap IPC clone with full schematics, software, and so on.
They also happen to be rather good at the job of streaming h264/265
The Pine64 guys are apparently making an IP camera. They’re shooting for the $20 or so range, like the Wyze IP Cameras. Most articles just paid attention to the Pinebook pro and other things like a tablet and a phone that they announced at the same time.
When I got into firmware development 20 years ago one of the first cameras I wrote a new image for was Toshiba IK-WB02A. Found the devs left everything behind including multiple UIs with dev comments. If you want a good camera it’s simple, buy a good one ie. AXIS, they pioneered JFFS, the filesystem.
“More often than not, configuration is through a strange smartphone app, and video is accessed through third-party servers.”
Thankfully I’ve gotten away from those kind of cameras. Pay a little more and firewall at the router and one doesn’t have to put up with as much.
This thread is old, but I’m searching for help. I have 6 bof these Zmodos which suck: interrupted video, adware and crap. I have pi and motioneye but I thought I would be able to find info on switching these six to usb. An info on that? I opened one up and found pads, started tracing them but thought maybe someone else has already done it. I hate to just toss them. convert from IP to usb? or just reuse the container and the IR with a laptop camera?
PiKrellCam, I can not recommend it enough.
post/pre capture triggers, full video and audio, support for ptz, night vision, emails, etc.
Cost: Free! [ as in speech and beer! ]
1xraspberry pi [zero w or Pi3]
1xUSB stick or mmc card
1xPi Camera NoIR [ 1920 x 1080 video and audio!]
1xIR Lamp
2xServos
1x3d printed servo bracket.
1x5V@2A power supply
I am in control of my data. It does not go to/through China.
I control the users, the parameters, everything.
I get emails when activity is detected. It supports multiple zones, thresholds, etc.
Best IP camera software I have seen, ever.
The Raspberry Pi Camera Module and built-in motion compressor make this a solution that can not be beat!
I use MotionEyeOS and store the data on my NAS (more durable than any flash storage). MotionEyeOS is optimized in size and reduces the writes to the µSD. I’ll look at PiKrellCam, tnak you !
MotionEyeOS is pretty nice too, but I find PiKrellCam offers much better resolution. As for writes, you can write the video anywhere. NaS, ftp, smb, /tmp, rsync, etc.
It uses a circular buffer in ram, so you can actually capture “pre” motion events up to 10-15 seconds before the motion was triggered, so you don’t lose frames.
MotionEye loses most of it’s functionality when using the CSI interface, which is a pity.
PiKrellCam installs on top of debian, or the Raspi image, so it can be a bit big, but well under 3Gb. It can be even trimmed down further with a little work.
I run my SD-Cards in ro, mode, and generally use ftp/smb/rsync or nfs/nas for storage of video.
with a 256Mb ramdisk, I can store a lot of clips before it gets full, and I can rsync or ftp it to my NAS.
PiKrell cam can use ftp/smb/nfs, rsync to transfer files. It can also run in “ro” mode, since is uses a memory circular buffer, and /tmp to store most everything, which on my system, is a ramdrive.
MotionEyeOS loses most of it’s functionality and motion detection when running on the CSI mode.
PiKrellCam however, does not, and has more functionality.
Not a developer of it, but it’s the best really OpenIPCam software I have seen in a while, including OpenIP cam. Too many crappy ipcams out there:
I have tried:
tenvis
wyzecam [ cheap, somewhat secure, but lacking in features ]
other ip cameras [ in the $50-$80 range ]
all of them either:
-send my data to china
-lack features
-lack security
-have a crappy phone-only app
-have a crappy web interface
-have no storage
-have very crappy single-zone motion detection, that either works or detects “everything” as motion
Wyzecams are rebaged Xiaomi cameras, notably the Xiaomi Dafang and Xiaomi Xiaofang. Unless they’re older cameras, they run Ingenico T20 processors that’ve been very well documented by the hacking community. It’s entirely possibly to do local recording to a USB hard drive, H264 RTSP streams to a local NVR, and use USB ethernet adapters with the help of custom firmware. Doing so also has the added benefit of stripping out all the cloud integration stuff that sends your security footage off to a server in China. ;)
Look up xiaomi-dafang-hacks on Github for more info. It really makes these cameras very, very cost effective indoor wireless security cameras with nothing more than a small microSD card and a little bit of your time.
I was looking into this once but I don’t know enough about it. If you use the MicroSD can you be absolutely sure that it’s not also running stuff that will send your data to China?
Not IP related, but security cam related… can anyone point to information on the AHD (analog high def) video format used in secuity cameras. I’ve searched for months but found nothing apart from same pretty vague wording that it is “an SD [PAL/NTSC] signal with a higher bandwidth”, intimating that it is squeezing more lines, of higher freqency content over a standard coax.
Seems like Nextchip makes some hardware.
http://www.nextchip.com/upload/PRODUCT/CONTENTS/CONTENTS7_E_133.png
Thankyou for that tip.
Ever come across any info on the AHD waveform itself?
Wikipedia strongly implies it’s subtly tweaked NTSC/PAL… maybe a reduced front/back porch, and officially widescreen.
AHD/CVI/TVI are all variations on a theme. They look on a scope pretty much like a NTSC signal. All were stolen from each oteher which in turn were stolen from SingMai
Read:
http://www.edn.com/design/analog/4402915/Transmitting-HD-video-over-RG-59-cable
Also:
https://www.youtube.com/watch?v=BTUJe-ABaIk
Thankyou.
Having brains in the camera (motion detection etc) seems very misplaced to me.
I have a dozen cameras on one system, that would be a dozen different locations to go to and several different UI to deal with, most highly inadequate.
I just want it to send video to my blueiris which is super powerful and all under one hood. RTP baby.
I do like for the camera to have a nice UI so I can alter parameters. But sometimes, for less money, I don’t even care about that so much.
IP cameras usually use the onvif standard which allow network video recorders centrally manage the cameras.
Love this project.
No cam should be calling China without my knowledge.
I’m looking for a simple way anyone can know if their devices are making connections without their permission, without learning wireshark.
wireshark is your friend. It’s not all that hard to use. You do need however, either a hub, or to run it from your router. Companies depend on the ignorance of the consumer to exfiltrate their data.
an alternative is, use the router, and disable all internet access to anything from China.
it can access anything on the lan, and I even restrict that to a guest network.
Basically, the function of any IoT device, is to exfiltrate your data, by any means necessary. Most include technology to go through firewalls, using http proxies , most located in China.
Best be safe and allow no internal/internet access to Chinese manufactured devices with untrusted firmware.
Slightly off-topic, but I recommend everyone with any interest in networking buy a WebUI managed/smart switch that supports port mirroring as a starter.
They’re a bit more expensive than the usual dumb switches, but you likely only need one managed / smart one that you can swap in or out as needed.
My personal preference is for the Mikrotik RB260GS, but the current versions of cheaper alternatives, Netgear (GS105Ev2 Smart Manged Plus) and TP-Link (TL-SG105E Easy Smart), are still great value (unless you need something specific to the Mikrotik).
They let you capture packet traffic at full speed (although heavily utilitized full duplex gigabit requires some improvisation or more expensive hardware, as that’s 2x1gbps if capturing ingress AND egress traffic).
It sure makes Wiresharking stuff easier.
>No cam should be calling China without my knowledge.
No cam should be calling ANYBODY without your knowledge! I do not trust my gouvernment more than i do with the chinese one…
Looking at Wireshark, if you just want to know how “communicative” a device is it is not really hard, just filtering for “http.request” (and DNS-lookups) gets you already a lot of info. The major problem is encryption. Not such a big deal on a computer you are root on, but big problem if you can’t modify your device to inject your own certificates to do MitM-attacks. However i’m not sure how common encryption actually is on “smart” stuff.
Brains in the camera is a good thing, if the brains are implemented properly.
That and nothing says you can’t have *both*
local and remote motion detection.
even a pi-zero w can do excellent multi-region motion detection with pikrellcam.
all-in-one centralization is good, and bad, it presents a single point of failure. Having some brains in the camera means if the network goes down, you have some local storage to deal with it for a bit.
Here is one Bad example of cheap China Ip Cams
300000 Unsecured Ip cameras.
https://youtu.be/gQQqWXQOKEE
http://www.hisilicon.com/-/media/Hisilicon/pdf/Display/Hi3516CV300.pdf
http://open.xmeye.net/en/
https://www.aliexpress.com/store/product/with-F1-0-Lens-StarLight-3-0MP-2048-1536-Sony-IMX291-3516C-E-IP-Camera-IP66/3631127_32931545823.html?spm=2114.12010615.8148356.4.1b7076c23VLwyI
It is not a standard. You need to license the technology from nexchip. It is just pal with a higher color subcarrier and higher pixel clock. If you attach a scope to the signal it is immediately clear how it works.
A defacto “standard” is still somewhat just that.
The good thing about “standards” is there are sooo many to choose from!
Did this one also upload files to a cloud bucket using shared credentials for all devices like mine: https://eriknl.github.io/reverse-engineering/2017/09/07/WiFi-camera.html ?
Great article and comments – very useful.
I’ve poked into a few IP cameras, but I was usually satisfied when I could find RTSP output that I could read right away without having to connect to the Internet and do the whole cloud configuration. I have one cheap camera (ZModo) that I haven’t yet figured out how to tap into. I might go looking for a serial port now.
I need to spend more time with Wireshark, too.
Hello guys,
Thanks for sharing your experience. I can tell you these cameras will stop working after some time if you do not pay the subscription. That happened to me and I fixed it redirecting some hosts to 0.0.0.0 in the /etc/hosts file on the camera, using an existing sd-card hack
Now I’m facing a different problem. If the camera can not connect to the internet, the rstp video and audio stream will freeze every few minutes, and go off after a while. This happens because the camera run a cycle to look for and reconnect to chinese servers every few minutes if there is no internet connection. I’m working on this right now and I hope I can contribute with the community providing the hack.
All regards
amazing guide