IoT devices rarely ever just do what they’re advertised. They’ll almost always take up more space than they need to – on top of that, their processor and memory alone should be enough to run a multitude of other tasks while not necessarily compromising the task they were built to do.
That’s partially the motivation for rooting any device, but for Xiaomi devices, it’s a bit more fun – that is to say, it’s a little bit harder when you’re reverse engineering its firmware from scratch.
Similar to his other DEF CON 26 talk on modifying ARM Cortex-M firmware, [Dennis Giese] returns with a walkthrough of how to reverse-engineer Xiaomi IoT devices. He starts off talking about the Xiaomi ecosystem and the drawbacks of reusing firmware across all the different devices connected to the same cloud network before jumping into the walkthrough for accessing the devices.
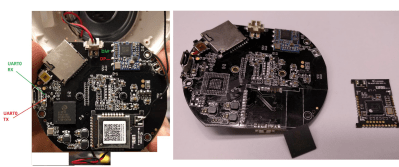
Targeting the Aquara Smart IP Camera, you first identify the serial port after bricking the device (a necessary step for connecting to the filesystem). Since the JFFS2 filesystem on the MCU (Zigbee NXP JN5169) wasn’t properly cleaned, a fair amount of credentials is leaked, which is essentially enough for rooting the device via telnet. Once you replace telnetd with SSH, change the root password, and change the camera software, you’ve got a modified smart camera!
For a different device, a WiFi network speaker, even the device teardown was unnecessary. No input validation was found on the firmware update over HTTP – no signatures, with the information packed into an XML format. This makes it even easier to simply overwrite the firmware OTA.
Finally, for a vacuum cleaning robot, a bit more circuitry was needed to root the device. In the usual method, the MMC data lines are shortcut, caused the system to fall into FEL mode. Using a USB connector and a load and execute tool, the MMC flash is dumped. The image can then be modified and rewritten to flash memory.
As it turns out, for many of the devices you don’t even need to resort to bricking the device in order to gain root access. While Xiaomi’s inevitably patched up most of the vulnerabilities since the talk, there’s invariably still more out there.
















This is why I diskile the whole IOT trend (and smaetphone apps for websites which pressure you to download the app by crippling the mobile site once they produce an app). It seems that not a day goes by where there isn’t a news story about an IOT device or mobile app surruptitiously phoning home with data not required for the user’s actual usage so the company who produced the app/device can monetize (sell to the highest bidder) or analyze the data (stalk their users).
It is hard to escape the impression that the more commercial closed source programs/devices with always on connectivity the more we bring about the dystopian world of Max Headroom.
I’d like to see how many of these apps and IOT widgets would still exist of they were required to release the source for their server-sode back-ends and allow users to run their own back ends so there’s no more phoning home to the mothership and no more sneaky data collection and monetization. (Things like how Android grew an impossible to disable weather widget once a critical mass of people stopped letting Google track their location in real time by othet means… now even of you turn off all other location authorizations Google still gets your location every 15 minutes or so to update the weather icon).
IOT devices are cool if I deploy, configure, and administer the device end and the server end with zero closed source components involved, and no encryption or signing keys that I do not also issue and maintain the ability to revoke. (They have to work for me, not for some shady corporation intent on monitizing my data behind my back).
Totally agree
It’s spoiling the potential of IOT and giving it a bad name.
I don’t see why a.n.other AliExpress camera/NVR/router/etc doesn’t have firmware available to download and enhance by the community. Why don’t they realise more sales would happen if their software wasn’t junk.
I don’t even mean to pick on Xiaomi or Google in particular (hidden microphone in Nest?) this goes for Amazon and all the other players. All those smart TVs which phone home to tell their manufacturers what you watch, when amd for how long? (some habe cameras and could even, if they desired, count how many pairs of eyes were looking their way and what part of the screen had peope’s focus). I don’t know that any _do_ this but with opaque firmware (DRM and all) and encrypted phone-home messages, how could we know?
How do non-geeks assess the risks? Or do they all just fall victim to all of these data harvesting schemes?
The approach I recommend to people that doesn’t automatically guarantee to leak their info or expose it is to go with a non-routable network for their home automation devices, such as Zigbee, Z-Wave, Insteon, or something similar. They can’t talk directly to a cloud server — they can only talk to a hub-type appliance. Then, find one of the few hubs that doesn’t leak to the cloud, such as OpenHab, domoticz, or Vera. (Avoid integrating them with the obvious data suckers, like Nest, Samsung Smart Things, Google Home, Alexa, and their ilk, of course.)
Such approaches are not for the novice, though. They require much more complex setups, and they still have to be careful to ensure they secure remote access to their hub. But their data will remain theirs.
Thats basically the goal of my research. I try to find ways to root the devices and to disconnect them from the cloud. This is also the reason, why I publish many local vulnerabilities directly without contacting the vendor in advance. That way they cannot immediatly lock their devices down and it gives advanced users some time to get root access to their own devices.
Even if you dont want to disconnect it from the cloud, it helps to understand what the device is doing and enables you to change the behaviour of it. But honestly, thats something for more advanced users and not for the typical IoT user :(
https://hackaday.com/2019/10/19/customizing-xiaomi-arm-cortex-m-firmware/
I thought the same thing at first but the links are for different presentations. Consider this a part 2 of the previous article?
I was confused myself for a second ;) I need to change my title slide a little bit more to make it more obvious.
This presentation was basically about exploiting Cortex-A based devices, while the other one was about Cortex-M based devices (which is completely different and more complex).
I don’t know whether I’m especially sensitive to it since German is my mother tongue,
but the German accent is a real pain to listen to.
It makes the speaker sound like 10x dumber.
English is my mother tongue, I don’t dislike a German accent, it doesn’t sound dumb to me. There are accents that really irritate me, I won’t name them, but I think they actively trigger my misophonia.
Dutch is my mother tongue, which is fairly close to German, albeit completely different, and I found Herr Giese to be perfectly understandable.
Hello, I found this site yesterday and thanks to you, I sill have hope to restaore my Xiaomi Network speaker ! I update it with new firmware, and the speaker does not wot with the multi room (upnp). I have to plug one chrome cast in the speaker. If I can downgrade to the old firmware, it would be perfect. Thanks by advance.
I found myself on the same boat. I stupidly updated the smart speaker and now it sounds so bad. Any advice how to factory reset or roll back firmware. Would love to hear too. I don’t mind sending my unit out to be a lab rat to all the other affected users around the world.
razorfish01@aim.com