This hack was revealed a while ago at DEFCON26, but it’s still a fascinating look into vulnerabilities that affect some of the most widely used IoT devices.
[Dennis Giese] figured out a way to modify ARM Cortex-M based firmware for use in customizing the functionality of devices or removing access to the vendor. Obviously, there are more malicious activities that can be done with this type of hack, as with any exploits of firmware, but they are (also) obviously not condoned.
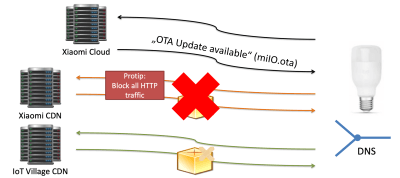
The talk goes into the structure of Xiaomi ecosystem and products before going into a step-by-step approach to binary patching the firmware. The first step was to acquire the firmware, either by dumping SPI flash memory (using JTAG, SWD, or desoldered Flash pins) or intercepting traffic during a firmware update and downloading the firmware. There’s also a possibility of downloading the firmware using a URL, although this can be more difficult to find.
The firmware can then be parsed, which first requires the format to be converted from a proprietary format to and ELF file. This conversion makes it easier to load into IDA pro, and gives information on the segments of the firmware and its entry point. Python tools luckily exist for converting binary files to ELF, which simplifies the task.
After loading the ELF file into the disassembler, you’ll want to find the key memory area, denoted by “TAG_MAC”, “TAG_DID”, and “TAG_KEY” in the example firmware (for storing the MAC address, device ID, and key). In order to prepare the firmware for Nexmon – a software that supported C-based firmware binary patching for ARM Cortex-A and ARM Cortex-M binaries – you’ll need to partition some space in the memory for patches and know the function names and signatures for the firmware.
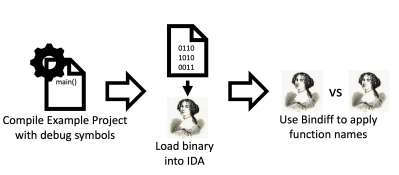
The latter is done by doing a difference comparison in the disassembler between an unknown executable and the example executable.
With the necessary information gathered, you can now use Nexmon to make your modifications. The fact that this can be done for smart devices at home means that smart devices you acquire – especially those partitioned by others – may contain malicious code, so take care when handling used devices.
Continue reading “Customizing Xiaomi ARM Cortex-M Firmware” →














