With millions of phishing attempts happening daily, we’ve probably all had our fair share of coming across one. For the trained or naturally suspicious eye, it’s usually easy to spot them — maybe get a good chuckle out of the ridiculously bad ones along the way — and simply ignore them. Unfortunately, they wouldn’t exist if they weren’t successful enough in the big picture, so it might be a good idea to inform the targeted service about the attempt, in hopes they will notify users to act with caution. And then there’s [Christian Haschek], who decided to have some fun and trying to render the phished data useless by simply flooding it with garbage.
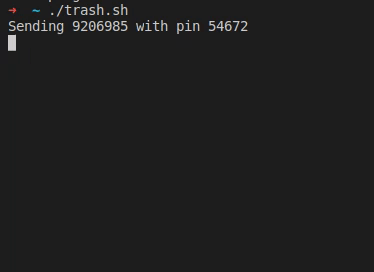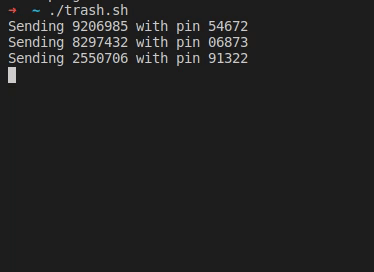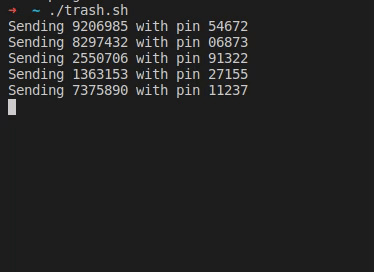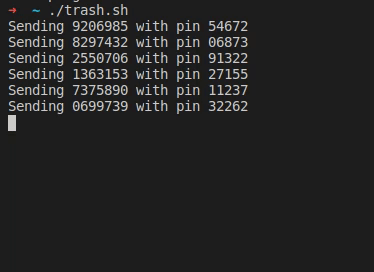 After his wife received a text message from “their bank”, [Christian] took a closer look at the URL it was pointing to, and found your typical copy of the real login form at a slightly misspelled address. As the usual goal is to steal the victim’s credentials, he simply wrote a shell script that sends random generated account numbers and PINs for all eternity via cURL, potentially lowering any value the attackers could get from their attempt.
After his wife received a text message from “their bank”, [Christian] took a closer look at the URL it was pointing to, and found your typical copy of the real login form at a slightly misspelled address. As the usual goal is to steal the victim’s credentials, he simply wrote a shell script that sends random generated account numbers and PINs for all eternity via cURL, potentially lowering any value the attackers could get from their attempt.
As the form fields limit the input length of the account number and PIN, he eventually wondered if the server side will do the same, or whether it would crash if longer data is sent to it. Sadly, he’ll never know, because after he modified the script, the site itself returned a 404 and had disappeared.
In the quest against phishing attacks, this should count as a success, but as [Christian] seemed to enjoy himself, he yearned for more and decided to take a look at a similar attempt he saw mentioned earlier on Reddit. Despite targeting the same bank, the server-side implementation was more sophisticated, hinting at a different attack, and he definitely got his money worth this time — but we don’t want to give it all away here.
Rest assured, [Christian Haschek] continues the good fight, whether by annoying attackers as he did with ZIP-bombing random WordPress login attempts or battling child pornography with a Raspberry Pi cluster. Well, unless he’s busy hunting down an unidentified device hooked up in his own network.
(Banner image by Tumisu)
















The complexity of these sites is all over the map, but my experience is the ones that get dropped on a hacked WP site just have a short PHP that emails the result to a free email account. Some don’t include anything but the scammed credentials, so this attack would work. More sophisticated sites have IP logging which would make filtering trivial.
Which makes me think a distributed agent that could send fake data to scam sites from many addresses would be useful. Using a botnet to make phishing unprofitable, hmm…
Or just pose as black hats selling stolen data on the darknets but the data is actually random numbers that look believable? Would need to change the laws regarding false advertisement to make it legal, although who would dare even mention to the authorities regarding something that’s illegal in the first place?
Dark net marketplaces are trust-based, you’d have a hard time getting enough trust to sell a big list and when you did and it turned out to be fake you’d have burned that identity. Making lists with real data but a higher-than-normal signal-to-noise ratio would work but you’d be perpetuating victims.
The optimal configuration would be to poison scammer’s data sets just enough to destroy that trust so they can’t sell – put enough fake data in, in ways they can’t readily detect, and you’ll quickly make it unprofitable for the sellers and the buyers.
Like most types of theft, it’s an arms race. To this point we’ve been using purely passive methods to prevent attacks – better firewalls, better filters, more keywords. IMO we need to start going on the defensive. The only reason this type of attack is profitable is the cost is so low. Drive the cost up by decreasing the success rate or poisoning the well and you’ll quickly see the number of attackers drop.
For how awesome and amazing this is, from a legal perspective according to most “decent” liars, err lawyers, tWo WrOnGs dOnT mAkE a RiGhT.
In all seriousness, thank you, keep up the good work.
Damn straight, anyone who hacks a scumbag phisher is a hero. And two wrongs don’t make a right, it takes at least 3.
I’ve done this since early 2000. My first experience with that was with a keylogger that sent the logs to a FTP server, and had hardcoded credentials. I logged there, deleted every log, and chmoded a-w the folder, so the other clients would not be able to upload anything…
Since that I used free proxies to avoid IP limits, randomized user agents, and reported them to the hosting company…
But just make sure your random strings don’t accidentally match yours to anyone else’s real accounts and PINs. That would be unfortunate.
What are the odds??? But that reminds me of the ATM’s with the sign “make sure no one can see your PIN”, so logically I have to paint over the keypad with black paint after using it?
Reminds me of James Veitch’s TED Talk in which he describes replying at-length to an email scammer…
https://www.ted.com/talks/james_veitch_this_is_what_happens_when_you_reply_to_spam_email?language=en
This reminds me of this series of videos i found on youtube. You know those fake antivirus alerts, you sometimes get as pop ups. There is a number you can call and they will do a “free diagnostic scan”. In the videos people let the scammer get remote access to their virtual machines and try and waste as much of there time as possible with out paying for them to “fix the virus”. some videos are a pristine new windows install. The ones i find the most hummorus is when the virtual machine is so loaded with malware and internet explorer ad bars, that the virtual machine barely works.
“The ones i find the most hummorus is when the virtual machine is so loaded with malware and internet explorer ad bars, that the virtual machine barely works.”
“[…] Jen, it’s infected! If this was a human being I’ll shot it in the face.” – Roy, IT Crowd