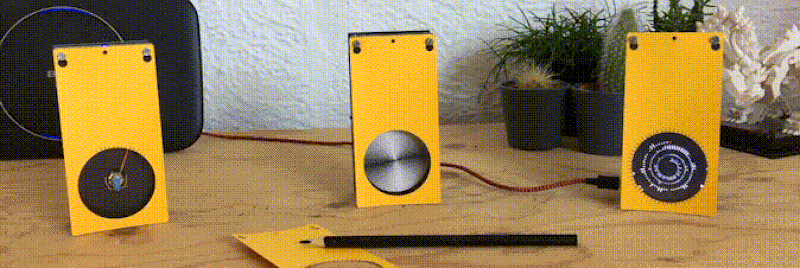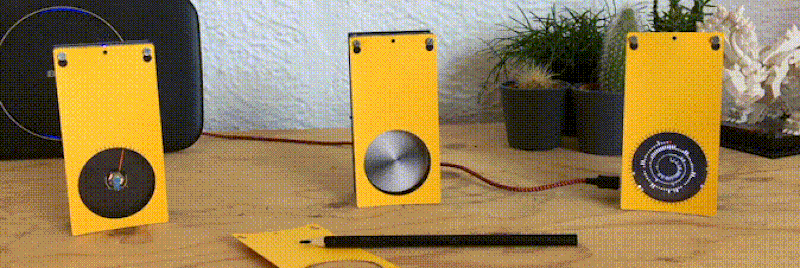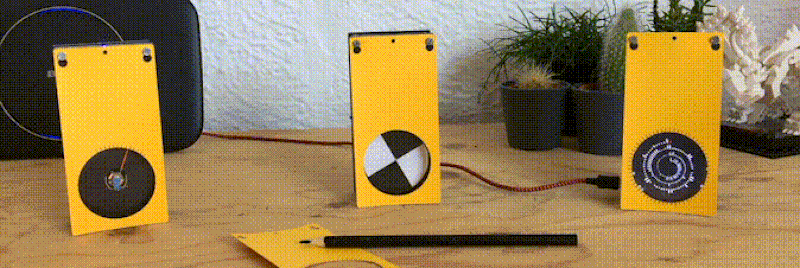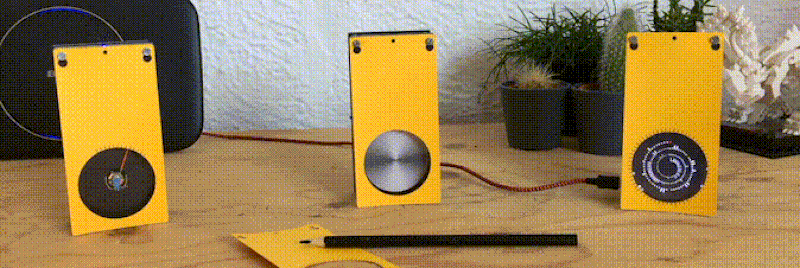
Like the “Three Seashells” in Demolition Man, this trio of bright yellow network monitors created by [David Chatting] might be difficult to wrap your head around at first glance. They don’t have any obvious controls, and their constantly moving indicators are abstract to say the least. But once you understand how to read them, and learn about the unique software libraries he’s developed to make them work, we’re willing to bet you’ll want to add something similar to your own network.
First-time configuration of the monitors is accomplished through the Yo-Yo WiFi Manager library. It’s a captive portal system, not unlike the popular WiFiManager library, but in this case it has the ability to push the network configuration out to multiple devices at once. This MIT-licensed library, which [David] has been developing with [Mike Vanis] and [Andy Sheen], should be very helpful for anyone looking to bring multiple sensors online quickly.

We’re also very interested in what [David] calls the Approximate library. This allows an ESP8266 or ESP32 to use WiFi signal strength to determine when its been brought in close proximity to particular device, and from there, determine its IP and MAC address. In this project, it’s used to pair the “Device Wheel” monitor with its intended target.
Once locked on, the monitor’s black and white wheel will spin when it detects traffic from the paired device. We think this library could have some very interesting applications in the home automation space. For example, it would allow a handheld remote to control whatever device the user happens to be closest to at the time.
Whether you follow along with the instructions and duplicate the meters as-is, or simply use the open source libraries that power them in your own project, we think [David] has provided the community with quite a gift in these unique gadgets.















I can see this being weaponized for remote delivery of a drone bomb to a particular cellphone. Just need the MAC address. It’ll sit there waiting for the device to be in range, then launch, get within a certain distance and detonate. Wouldn’t be surprised if governments don’t already have such a thing, but this would put it in the hands of any low tech idiot that wants to harm.
There are a million easier ways to cause harm than this. Just because it can be used for wrong, doesn’t mean that it’s inherently bad.
We all drive cars. It’s prety easy to run someone over.
We all have phones. Lots of illegal activity is enabled by access to communication.
We all can speak. Prety easy to slander someone.
We all can make choices. Prety easy to chose do harm.
Do harm vs do good is a moral question, not a technological one. Unless technology is built with a single use case of causing harm, it’s not right to criticize the technology. And even then, one ought to criticize the designer’s motives more than his creations.
I see no reason to find issue with this project.
Right! Sooner or later someone will fly an airplane into a building and that will be the end of air travel.
I’m nominating this for Internet comment of the year.
This would allow someone to leave a trap that kills a particular individual days or even weeks after they have left the area. That is different from being able drive someone over or using a phone for a drug deal. I’m not saying this technology is bad or good. Just that this is one potential use of it for evil. You can give the BS line that “[blank] don’t kill people, people kill people”, but in reality we as a society give the tools and resources to people to kill people. If we were more responsible with our tools, we could prevent deaths. I personally don’t like the idea that a bomb could remotely seek me out without any human intervention. I probably won’t be targeted in such a way, but I could see terrorists using this to take out journalists, military targets, or political opponents. If you’re not concerned about people dying using tech you develop, good for you. I personally would not like it.
From time to time, inventors regret inventing something. The K-cup bring the most recent i can think of. There are many more applications for this technology than the aforementioned single use
The 555 timer chip was potentially in the same boat.
It’s always application of technology which is the ethical question, not the technology itself.
A fork too is a deadly weapon. Perhaps we should go back in time and kill the inventor before it is misused. Any piece of technology can be misused. This does not mean we stop inventing.
Phones randomise their MAC unless on authenticated networks to prevent tracking.
If your attacker is already on an authenticated network with you, they’ve almost certainly got better ways to get you.
While this is true, many still don’t use that sufficiently. I have seen supermarkets still tracking people with this to build movement patterns.
Not to mention, big surveillance companies like facebook and google who lock will lock you out if they “don’t recognise this device.”
Cell phones do not constantly broadcast a wifi signal that can be used to measure the required signal strength. This is unless the cellphone users set up a wifi network with his phone and leaves it running.
So your fears might not really be necessary.
You would be surprised on how much data your cellphone sends around and how you can track people with it. Now they randomize those requests on the newest phones.
It would be still easier to track an individual over IMSI / SS7 Tracking
There was much debate on just how “the 3 seashells” were supposed to be used. “wrap your head around them” is a new one.
I’m thinking Harry Potter wand for every light in the house and more. :D
I’ve been at trade shows where every booth had its own wifi router and have often thought it would be cool to have a display of the triangulated position of each device and their relative signal strength.