A particularly nasty 0-day was discovered in the wild, CVE-2021-40444, a flaw in how Microsoft’s MSHTML engine handled Office documents. Not all of the details are clear yet, but the result is that opening a office document can trigger a remote code execution. It gets worse, though, because the exploit can work when simply previewing a file in Explorer, making this a potential 0-click exploit. So far the attack has been used against specific targets, but a POC has been published.
It appears that there are multiple tricks that should be discrete CVEs behind the exploit. First, a simple invocation of mshtml:http in an Office document triggers the download and processing of that URL via the Trident engine, AKA our old friend IE. The real juicy problem is that in Trident, an iframe can be constructed with a .cpl URI pointing at an inf or dll file, and that gets executed without any prompt. This is demonstrated here by [Will Dormann]. A patch was included with this month’s roundup of fixes for Patch Tuesday, so make sure to update.
ForcedEntry
Yet another 0-click 0-day, this time in Apple products, CVE-2021-30860 was discovered as part of the NSO Group’s exploit toolkit. Citizen Lab refers to the vulnerability as FORCEDENTRY. It’s a problem in Apple’s image rendering code, that allows a malicious PDF to trigger RCE. Because Apple shares this library across devices, the exploit works on iOS, MacOS, and even watchOS prior to the patch. Basically all the technical details are from Apple’s patch notes, where they’re calling it an integer overflow.
ProtonMail Logging IPs
ProtonMail has been in the midst of a minor kerfuffle after giving up the IP address of one of its users to Swiss authorities. One of the understandable responses is disappointment that they even have the ability to do so, given their no-logs stance.
The reality is that ProtonMail is a Swiss company, and they are bound by Swiss law. It appears that when a binding request for information is received, the administrators at ProtonMail turn on logging for the specific account named in the request. They point out that had the targeted users used their VPN offering or TOR, they could have kept their IP private. ProtonMail also pointed out that their encryption wasn’t broken, so law enforcement was still unable to access the attachments or emails on the service.
Spell-check Plus Symlink
GitHub has the really useful Actions feature, where certain workflow steps can be automated. One such workflow is check-spelling, which does exactly what it says on the tin. A strange interaction exists, when a pull request contains a spelling error, as well as a symlink from .github/actions/advice.md to /proc/self/environ. Advice.md is intended to contain the instructions for how to proceed when a misspelling is found, and is posted as part of the automated comment on the pull request. The symlink in the pull request means that what actually gets commented is the environment information of the process runner, including a secret GitHub authentication token.
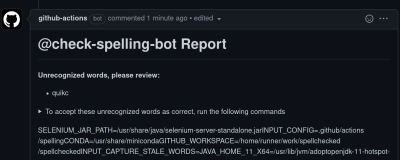
That token is invalidated very quickly after the workflow completes, so the trick is to win the race to use the token in time. The proof-of-concept demonstrates how to poll the comments, find the token, and make an “emergency release” that is actually an attacker supplied binary. The fix has been implemented — simply disallowing such symlinks when running the workflow.
This is actually a larger problem, though, as the workflow configuration settings are contained in the same codebase as the pull request. Put simply, any GitHub Action triggered on a pull request is potentially unsafe, and needs to be very carefully hardened against similar problems.
Router Leaks IP
Researchers at Fidus have put together a very clever attack to unmask the real IPs of users of some VPNS. The attack relies on the presence of an Simple Network Management Protocol (SNMP) web wrapper that is present on some consumer routers. SNMP is a useful protocol to programmatically get statistics and other status information from a networked device. The research was done on Virgin Media routers, which happened to allow unauthenticated requests to the SNMP wrapper. One of the data points accessible is the public IP address assigned to the router.
So all an attacker has to do is get the victim to load their web page, and use some JS code to do a GET request from the router’s IP, right? Except browsers have been adding security features to prevent exactly this sort of abuse. The trick that works here is DNS rebinding, where the DNS record for the malicious site is set to a very low Time To Live (TTL), and the record is changed once the page is loaded. This allows the page JS to make another request to the same domain name, and that request actually go to an arbitrary IP. The router’s web interface doesn’t have any safeguards against this technique, so it gladly gives up the IP address.
This doesn’t work against every VPN. Some clients block access to local IP addresses, probably to prevent exactly this sort of attack. Notably, TOR works this way. For a VPN that does not, however, this can leak the public IP. The other interesting wrinkle to this story is that this was first discovered back in October 2019. Liberty Global, the owner of Virgin Media, requested a full year to address the vulnerability. Rather than work on a coordinated disclosure, Liberty has “ghosted” the researchers ever since. There doesn’t seem to be any fixes rolled out, so this should be treated as a 0-day until proven otherwise. The workaround is to only use a VPN client that blocks access to local IPs, if you’re concerned about not leaking identifying information to sites you visit.
Microsoft’s Azure Linux — OMIGOD
Do you run a Linux VM on Microsoft’s Azure? You probably have vulnerable services running on that VM right now. The problematic service is the Open Management Infrastructure (OMI), which is automatically installed as a part of several Azure services. The worst of the vulnerabilities is CVE-2021-38647, a pre-auth RCE as root, requiring only access to an exposed HTTPS port. It is a simple authentication logic flaw, where a request without an Authorization header defaults to running as root. Updates are available, but it’s unclear whether patches will roll out automatically. Check for the omi package. If it is present, version 1.6.8.1 is the release containing fixes.
Bits And Bytes
I was recently made aware of the Gluu Server, a single-stop solution for providing your own OpenID authentication service. If you’re ever faced with needing to roll a Single Sign-on solution, Gluu appears to be a strong contender. We even interviewed the founder of Gluu on FLOSS Weekly, if you care to learn more.
Firefox has had enough of Microsoft’s shenanigans. You may have noticed how difficult it is to change program defaults in Windows 10. There’s a list of file types, and you have to set all of them to your preferred application — unless of course you want to default to Microsoft’s products. Then it’s a single click. Some very clever engineers at Mozilla have reverse-engineered the way Edge sets itself as default, and Firefox is now capable of the same trick.
















“Liberty Global, the owner of Virgin Media, requested a full year to address the vulnerability. Rather than work on a coordinated disclosure, Liberty has “ghosted” the researchers ever since.”
That sounds par for the course with Virgin, who I have just ditched after over a year of getting 60-70% of the bandwidth I was paying for. The salesman actually lied too on the contract termination call, saying I couldn’t port my phone number if I gave notice then and there, needless to say I did, and it ported fine.
“The trick that works here is DNS rebinding, where the DNS record for the malicious site is set to a very low Time To Live (TTL), and the record is changed once the page is loaded. ”
Noted my router has a “enable DNS rebind protection” which I assume some others do, as well as alternative firmware.
>”…, though, …”
Is this like the speakers “um” or “uh”, or was the though supposed to be part of the first or second phrase as opposed to a sentance on it’s own?
very interesting. it seems the time and position of your comment is on the users end not the servers… Time for someone to retroactively post “first” on every single had article?
As a ProtonMail user, I am disappointed. However, realistically, all companies will have to comply with the law. Even if they weren’t logging IP addresses before the warrant or subpoena or whatever it was, they could be compelled to add logging by law enforcement. And, of course, it’s basically impossible to prove a negative, so they can never prove they don’t log something. I don’t think this is a death blow to their business model or their commitment to privacy. But it should be a wake up call to people who care about such things.
Go to the utopia ecosystem. in a P2p system, you are not in any danger.
> The workaround is to only use a VPN client that blocks access to local IPs, if you’re concerned about not leaking identifying information to sites you visit.
the _solution_ is to not run untrusted code when you’re concerned about privacy. javascript from untrusted hosts is untrusted code.
that solves heaping piles of other security problems, too. past, present and future.
HTML from untrusted hosts is untrusted code. Pretty much everything these days is code.
The issue here is more the “untrusted” than the “code”.
> ProtonMail also pointed out that their encryption wasn’t broken, so law enforcement was still unable to access the attachments or emails on the service.
But that is not the only information in an email, you have a source address and a destination address in the headers and a record of the intermediate emails servers between the two. So it would be like not being able to see the contents of an envelope, but you can inspect the envelope.
Looking at the Microsoft stuff…. I find it humorous I just finished building a Linux computer to switch away from Windows. So long MS, it hasn’t been fun.