One of the many fascinating fields that’s covered by Hackaday’s remit lies in the world of hardware security, working with physical electronic hardware to reveal inner secrets concealed in its firmware. Colin O’Flynn is the originator of the ChipWhisperer open-source analysis and fault injection board, and he is a master of the art of glitching chips. We were lucky enough to be able to welcome him to speak at last year’s Remoticon on-line conference, and now you can watch the video of his talk below the break. If you need to learn how to break RSA encryption with something like a disposable camera flash, this is the talk for you.
This talk is an introduction to signal sniffing and fault injection techniques. It’s well-presented and not presented as some unattainable wizardry, and as his power analysis demo shows a clearly different trace on the correct first letter of a password attack the viewer is left with an understanding of what’s going on rather than hoping for inspiration in a stream of the incomprehensible. The learning potential of being in full control of both instrument and target is evident, and continues as the talk moves onto fault injection with an introduction to power supply glitching as a technique to influence code execution.
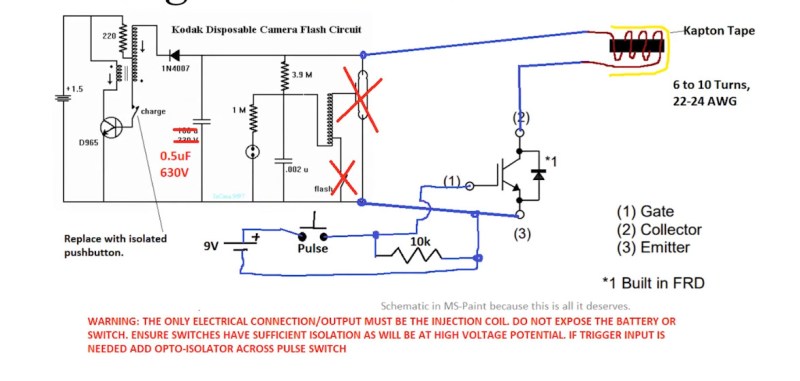
His final trick is to take a look at glitching by EM injection using an electromagnetic pulse. Here he takes us into a much lower-tech direction, as while he shows us his ChipShouter product the main thrust of the segment comes in demonstrating a much more rudimentary but cheaper EM injector built from the parts of a disposable camera flash. From an electronic design perspective the interesting part comes in the probe and its trigger, an IGBT is used to pulse a small coil mounted on an SMA plug. Here the target is a Raspberry Pi running repeated RSA signing test code, and even the simpler EM injector is able to crash it and extract the keys. He wraps up with a few smaller examples of the same technique on microcontrollers, and even mentions that the same technique can yield results from such rudimentary tools as an electrostatic gas lighter.
Whether this talk inspires you to break out the piezo lighers, cobble together a simple glitching rig yourself, to invest in a ChipWhisper, or none of the above, Colin’s talk sheds some light on another of our community’s Dark Arts.
















One improvement for sending a glitching pulse is to have feedback from the device and a variable delay. So you can say, cycle the power and then send a pulse at a specific time during boot and then if you don’t see a signal saying boot finished, you don’t try again. Then you can make several tests automatically with different delay times, record the results and sort them later, say you leave it running in a loop overnight and it spits out good options to try in the morning.
This is literally what I did when I was dumping code from 68HC705s the other day. I hooked an Arduino up to a CPLD and had the CPLD generate glitches a specific number of cycles after the CPU reset. I think the ChipWhisperer can probably do something similar.
It doesn’t explain why a power or calculation glitch would give you the private key. Nor why a password could be guessed when trying char by char.
If I understand correctly, most password system will hash the password (at least once for bad system, but it can be numerous iterations for PBKDF2 systems). So when you try to brute force the password byte by byte, you are very unlikely it’ll match with the real hash, so there should be no measurable power difference here.
That EM injector is overkill. The flash tube itself is a very capable high speed switch, no need for that IGBT stuff.
I would love to connect about this . I’m very interested in this please reach out .