Many years of using televisions, monitors, and projectors have conditioned us into treating them as simple peripherals whose cables carry only video. A VGA cable may have an i2c interface for monitor detection, but otherwise it presents little security risk. An HDMI interface on the other hand can carry an increasing number of far more capable ports, meaning that it has made the leap from merely a signal cable to being a connector stuffed with interesting attack vectors for a miscreant. Is it time for an HDMI firewall? [King Kévin] thinks so, because he’s made one.
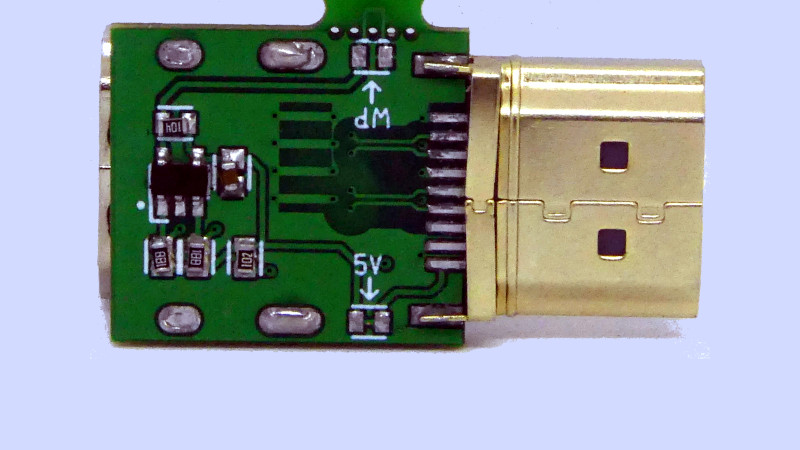
It’s a surprisingly simple device, because the non-signal capabilities of HDMI rely on a set of conductors which are simply not connected. This of course also disconnects the on-board EEPROM in the device being connected, so there’s an EEPROM on the firewall board to replace it which must be programmed with the information for the device in question.
The premise of HDMI as an attack surface is a valid one, and we’re sure there will be attacks that can be performed on vulnerable displays which could potentially in turn do naughty things to anything which connects to them. The main value for most readers here probably lies though in the introduction it gives to some of what goes into an HDMI interface, and in accessing the i2c interface therein.
It comes as a surprise to realise that HDMI is nearing 20 years old, so it’s hardly surprising that its hacking has quite a history.















I gave a presentation one time at a DoD building, in a room where Classified briefings were also held. Plugged a laptop directly into the big monitors on the wall, that were regularly plugged in to SIPRNet hardware. It would take a very targeted attack, but I could see it. If nothing else, a compromised display could be the relay to get data out of an otherwise air-gapped or SIPR only device.
Not sure it needs to be that targeted an attack – the displays have very common design in their electronics, at least for each brand/common panel and so even across the brands that are friendly with each other – so find a flaw and I’d expect it to be pretty easy to distribute, the hit rate of similarly flawed displays won’t be superb, but more than high enough to be scary…
Rather convoluted to use it as an air-gap bypass, but very doable.
Just please don’t find a flaw in the CEC, EDID handshakes on Windon’t, Mac or Linux as maybe it can then propagate to travel on its own and function a bit like an airgapped botnet…
Wonder if any of those big monitors were ‘smart’ in any official way, wouldn’t surprise me as finding ‘basic’ displays is actually getting challenging.
You sir have tapped on the the real threats mindset and approach. Well done 👍
A friend of mine propositioned every woman he could. He figured that even if he had a 90% failure rate that for every ten women he propositioned, odd are in his favor that he was getting laid. He could handle rejection. Same in your scenario, it’s the small wins that add up. Not the ego based losses.
The programmer contains a STM8 µC. I would love to see everything consolidated into a single device.
Short a contact when plugging it in to reset the EDID, and short it while in use to read the connected device’s EDID and clone it. Break a tab off and it can no longer be reset or cloned.
If you have the correct system, an app like rweverything cam program an EDID chip.
There are $4 HDMI edid emulator with Passthrough, just get that, cut or pull out any pins you don’t want, and write protect the i2c. Cheapest way to up and running
I was using it for a PC with long runs to multiple monitors, it would regularly fail the handshake from the splitter in the ceiling. Put one of these on and its been fine for months. Also set it to 720p (what most of the content is natively), had to dive into the driver utility to get it to actually /send/ 720p down the wire (scaling on display instead of GPU)
Those little rounded slivers of copper on the bottom layer ground plane look scary. I presume they are artefacts left in the polygon pour by a keep-out region around the differential pairs.
Seen it in the wild…
WAT? Can you describe more? Was it using the Ethernet channel HDMI can offer or CEC? Lemme guess CEC buffer overflow to execute code on a display’s control processor?
There are various communication channels apart from video transmission (that includes packet data, some of variants of variable size) and hotplug detect: DDC (approx I2C) that is usually for EDID transfer purposes and most noticeably HDCP sideband communication, the very short lived Ethernet over HDMI, Audio Return Channel (similar to SPDIF), CEC (packet distribution on all advertising interconnected A/V devices) and most recently eARC. In some cases, the HDMI port is also MHL compatible.
CEC is the most likely to be attacked. I assume that any device implements the CEC protocol in software. Unless there are backdoors somewhere else.
How long until we see a fake Chromecast with a payload?
I’m pretty sure my Sharp LC-52D85U has malware. Many years back I installed a firmware update from what I realized later was a questionable source. I can no longer upgrade or downgrade and the only answer my research found was to replace the motherboard entirely. But it mostly works. Linux misreads the sync parameters (Windows doesn’t) so I had to figure out how to re compute them and create a custom config. Every so often the tv will go into a boot loop, unresponsive until I cut and reconnect power, but that doesn’t happen more than once a month. Aside from that which was kinda my fault, no complaints. Over 13 years of heavier than average use, not one dead pixel, and a young James Garner looks real handsome as Maverick on it right now. It has fluorescent bulb backlights!
you possibly applied the incorrect firmware for a different version of chip or board ? Given the attack vector for a smart TV via firmware must be via a smart TV some packet sniffing of the ethernet would identify that. Most firmware I’ve applied to smart TV in the past has been hacked together with the best intention to increase the lifespan of an otherwise obselecent piece of hardware and sometimes the just run out of ran or are poorly compiled. Just my opinion.
lol at “break to write protect”. Now that’s security :)