When Microsoft released its first entry into the video game console market with the Xbox, a lot of the discussions at the time revolved around the fact that it used a nearly off-the-shelf Intel CPU and NVIDIA GPU solution. This made it quite different from the very custom consoles from Nintendo and Sony, and invited thoughts on running custom code on the x86 console. Although the security in the console was hacked before long, there were still some open questions, such as whether the secret boot ROM could have been dumped via the CPU’s JTAG interface. This is the question which [Markus Gaasedelen] sought to answer.
The reason why this secret code was originally dumped by intercepting it as it made its merry way from the South to the North Bridge (containing the GPU) of the Xbox was because Microsoft had foolishly left this path unencrypted, and because the JTAG interface on the CPU was left disabled via the TRST# pin which was tied to ground. This meant that without removing the CPU and adding some kind of interposer, the JTAG interface would not be active.
A small issue after the harrowing task of desoldering the CPU and reinstalling it with the custom interposer in place was to keep the system integrity check (enforced by an onboard PIC16 MCU) intact. With the CPU hooked up to the JTAG debugger this check failed, requiring an external injection of the signal on the I2C bus to keep the PIC16 from resetting the system. Yet even after all of this, and getting the secret bootrom code dumped via JTAG, there was one final system reset that was tied to the detection of an abnormal CPU start-up.
The original Xbox ended up being hacked pretty thoroughly, famously giving rise to projects like Xbox Media Center (XBMC), which today is known as Kodi. Microsoft learned their lesson though, as each of their new consoles has been more secure than the last. Barring some colossal screw-up in Redmond, the glory days of Xbox hacking are sadly well behind us.








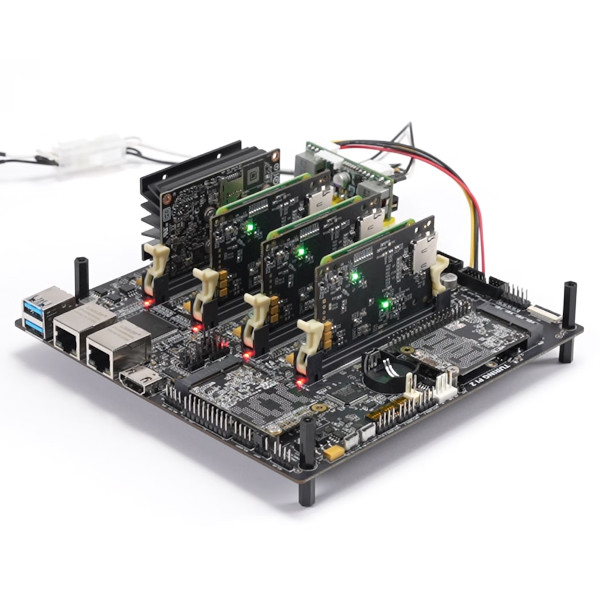








I wonder if it would have been possible to disconnect TRST by CNC-drilling from the other side. Some research suggests, og Xbox was 4 layers with GND and Power on L2&3. So that might be possible. The question is, if floating would be sufficient or if if has to be tied high.
Yes, that idea is discussed in the linked write-up and – due to the concerns you mention – was dismissed in favor of building the intercept layer board.
From the original Post:
“While yes, in theory drilling out the connection to release TRST# may allow us to drive the JTAG state machine, I had no clue how the CodeTAP / hardware debugger might respond to TRST# not operating as expected.”
Later: “With Intel JTAG on Xbox now fully functioning, there is less uncertainty in refining this work by eliminating the arduino and likely even the CPU interposer.”
So maybe it would work…
In theory, if the pin was assessed by drilling, there’s no reason why a connection to it can’t be made through the hole in order to supply the voltage to pull it high.. Either a fine wire or perhaps some molten metal.
It wouldn’t be the first time an xbox was hacked with a drill, the Kamikaze hack on the 360 involved literally drilling into the DVD controller chip to cut two specific leads that controlled the “read only” setting for the drive’s firmware. Drilling being necessary since the entire chip was potted in resin.
Bought the OG Xbox when it was released, specifically to chip it (softmod wasn’t a thing then IIRC) so I could run XBMC. Good times
XBOX1 had an LPC connector on the board, like the PCEngines Alix board.
Flashrom has support for it via an stm32 board:
https://github.com/wosk/stm32-vserprog-lpc
Ah, the original Xbox and Microsoft’s amazing hubris. I worked for a company who made the anti-copy protection for most A-list PC titles, and we offered the technology to MS. They declined, confident the Xbox was secure.
… We’d shown them a demo of our system, running on an Xbox.
We’re all glad they didn’t take you up on your offer.
;__; In 2008 I’ve used my old and working Xbox as a .22 LR plinking target.
That was so stupid.
eevblog on youtube did a cool video about JTAG boundary scan a few years ago, little known feature of JTAG that’s often deployed to digital IC designs by default, that lets you slurp out the pin states of near any IC by messing with the clock signal
the book, ‘Hacking the Xbox: An Introduction to Reverse Engineering’ by Andrew (Bunnie) Huang details the remaining step of extracting the Xboxes encryption keys from the hardware.
Little known feature?
It’s literally the whole original purpose of JTAG and every introductory text starts with boundary scan!
If I worked at Microsoft you would dump a ROM and find…
https://www.reddit.com/r/pics/comments/d79p45/did_you_know_that_this_is_bill_gates_sexy_pose/
Ok, maybe it would be a short career but it would be worth it.