One can only imagine the wonders held within the crypto labs of organizations like the CIA or NSA. Therein must be machines of such sophistication that no electronic device could resist their attempts to defeat whatever security is baked into their silicon. Machines such as these no doubt bear price tags that only a no-questions-asked budget could support, making their techniques firmly out of reach of even the most ambitious home gamer.
That might be changing, though, with this $500 DIY laser fault injection setup. It comes to us from Finnish cybersecurity group [Fraktal], who have started a series of blog posts detailing how they built their open-source reverse-engineering rig. LFI is similar to other “glitching” attacks we’ve covered before, such as EMP fault injection, except that a laser shining directly on a silicon die is used to disrupt its operation rather than a burst of electromagnetic energy.
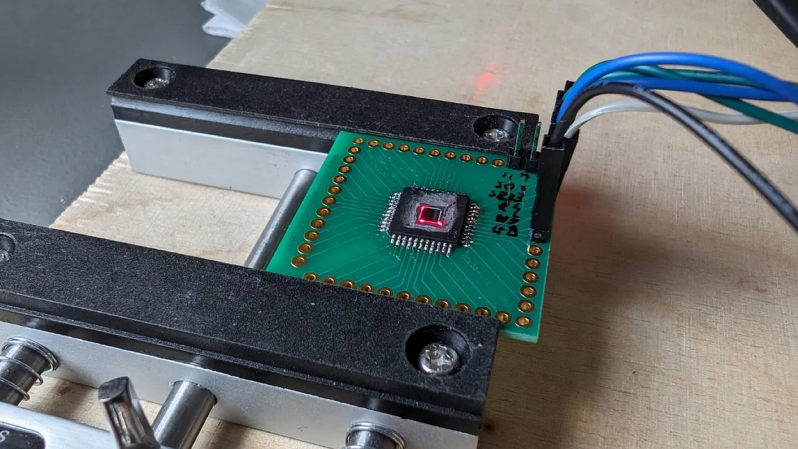
Since LFI requires shining the laser very precisely on nanometer-scale elements of a bare silicon die, nanopositioning is the biggest challenge. Rather than moving the device under attack, the [Fraktal] rig uses a modified laser galvanometer to scan an IR laser over the device. The galvo and the optical components are all easily available online, and they’ve started a repo to document the modifications needed and the code to tire everything together.
Of course, this technique requires the die in the device under study to be exposed, but [Fraktal] has made that pretty approachable too. They include instructions for milling away the epoxy from the lead-frame side of a chip, which is safer for the delicate structures etched into the top of the die. The laser can then shine directly through the die from the bottom. For “flip-chip” packages like BGAs, the same milling technique would be done from the top of the package. Either way, we can imagine a small CNC mill making the process safer and quicker, even though they seem to have done pretty well with a Dremel.
This looks like a fantastic reverse engineering tool, and we’re really looking forward to the rest of the story.
Thanks to [gnud] for the heads up on this one.















Erm, laser is also electromagnetic energy.
The laser source and optics are far more complicated than the positioning. What makes this implementation interesting over standard fault injection is the use of a continuous scanning of the target, instead of a grid search (location, power, and time). The author describes this as a probabilistic attack. As in, there will be a moment where the laser hits the right spot at the right location if the test is executed enough times. I expect that most targets with a high success probability will also be glitchable with other methods like voltage, EMFI, and BBI. (All which are accessible to hobbyists)
With chips including glitch detectors, and other defenses against electrical attacks, this has potential.
Of course the chip maker can also deploy some defenses against this too, but it’s probably more difficult to defend against. The pins are like corridors or defiles which can be defended heavily, while life goes on within the walls. This is a direct attack over the defenses.
Eh… your writeup’s use of “nanopositioning” is a wee bit misleading. The protocol that these galvo scanners use, XY2-100, uses 16-bit position data, or 65536 possible values. The smallest working area f-theta lens I’ve seen is 70mm, so that’s 70mm/65536 = about 1 micrometer resolution. Of course, it will be worse than that because of settling etc. However, the bigger issue is the size of the laser spot. I don’t know about a diode laser source, but I have a couple of fiber laser engravers and with a 70mm lens the focused spot size is maybe 10-20 micrometers diameter. So you’re never going to illuminate things on the nanometer scale, a few tens of micrometers at best.
Unless you have an iPhone.
Do you have reason to believe this?
Yes. All the times the government has said they need encryption backdoors because they couldn’t get into someone’s iPhone.
They often say that as a way to affect long term technology policy and laws. Notice how after they grandstand about it for a while there is always a unlock provided by some third party company. Of course the unlock isn’t a media talking point like the initial inability to unlock the phone is.