There’s a lot going on in our wireless world, and the number of packets whizzing back and forth between our devices is staggering. All this information can be a rich vein to mine for IoT hackers, but how do you zero in on the information that matters? That depends, of course, but if your application involves Bluetooth, you might be able to snoop in on the conversation relatively easily.
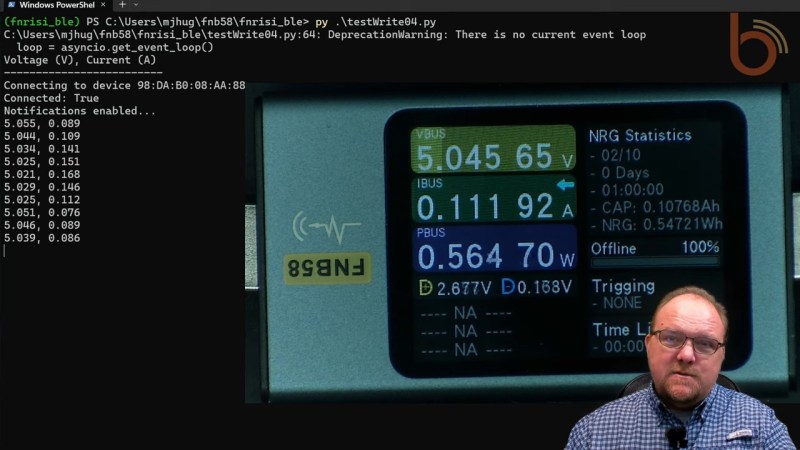
By way of explanation, we turn to [Mark Hughes] and his Boondock Echo, a device we’ve featured in these pages before. [Mark] needed to know how long the Echo would operate when powered by a battery bank, as well as specifics about the power draw over time. He had one of those Fnirsi USB power meter dongles, the kind that talks to a smartphone app over Bluetooth. To tap into the conversation, he enabled Host Control Interface logging on his phone and let the dongle and the app talk for a bit. The captured log file was then filtered through WireShark, leaving behind a list of all the Bluetooth packets to and from the dongle’s address.
That’s when the fun began. Using a little wetware pattern recognition, [Mark] was able to figure out the basic structure of each frame. Knowing the voltage range of USB power delivery helped him find the bytes representing voltage and current, which allowed him to throw together a Python program to talk to the dongle in real-time and get the critical numbers.
It’s not likely that all BLE-connected devices will be as amenable to reverse engineering as this dongle was, but this is still a great technique to keep in mind. We’ve got a couple of applications for this in mind already, in fact.
















I had to debug a BLE link for work, and I found Wireshark and the Adafruit BLE Sniffer dongle (https://www.adafruit.com/product/2267) very useful in debugging the protocol between our device and the PC. I notice there’s an updated version available, but I haven’t tried it.
Ohhh i got a ble story!!
I bought a volcano hybrid vaporizer, it’s got ble for turning on the air blower and messing with the temp settings and some other random settings, the Bluetooth died within 24 hours of owning the device lol, since I ordered it across the border, it was going to be ridiculously expensive to ship back for repairs, and the function isn’t that important for my medical needs. Just useful. After a year or so of hitting the air button manually like a caveman, I noticed that the display was blinking every time I randomly tried connecting my phone to it in hopes it might magically start working again. So I got it into my head to see what I could do to figure out how to get it working outside the official app.
I knew literally nothing about the protocol when starting out, but after 48 hours straight of pushing random hex bits (eventually figuring out that sending a zero was less effort and did the same thing) at every address using ble sniffer apps on my phone, I had every single function including putting it into “dfu” mode ( which consumers aren’t given access to via any official app), mapped out into their own function with these multiple sniffer apps that all gave me a little different set of information that built up the whole picture in my mind of what was going on. It actually terrifies me to know that it’s using heart rate monitor protocols (it’s just a generic set of commands that don’t really matter that much from what I read about the subject). But if a complete noob like me was able to get such deep access to the device in the most caveman brute force fashion, how insecure are Bluetooth medical devices that might be relied upon for more serious reason?
I also figured out why my phone could never connect (I think.) It relied on you putting in the serial number of the device into the app to access, and from all my bit banging it looks like the internal serial number address got corrupted.
Anyways. Literally a week after I got my own unofficial “app” figured out, the company released a web app for pc to connect to the vape that is far more convenient for my use case that didn’t need any serial number to connect.
Nice story. Was the DFU mode available in the web app?
Nope, I had to google what the heck dfu even meant lol
Should have used an app clip. NFC > BLE 😂❤️