A while back we saw the MintEye CAPTCHA system – an ‘are you human’ test that asks you to move a slider until an image is de-swirled and de-blurred – cracked wide open by exploiting the accessibility option. Later, and in a clever bit of image processing, the MintEye CAPTCHA was broken yet again by coming up with an algorithm to detect if an image is de-swirled and de-blurred.
It appears we’re not done with the MintEye CAPTCHA yet (Russian, translation). Now the MintEye CAPTCHA can be broken without any image processing or text-to-speech libraries. With 31 lines of Java, you too can crack MintEye wide open.
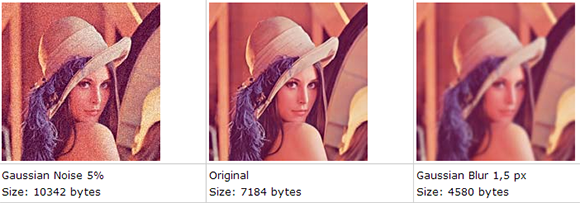
The idea behind the hack comes from the fact that blurred images will be much smaller than their non-blurred counterpart. This makes sense; the less detail in an image, the smaller the file size can be. Well, all the pictures MintEye delivers to your computer – 30 of them, one for each step of swirl and blurring – are the same size, meaning the ‘wrong answer’ images are padded with zeros at the end of the file.
There’s a 31 line program on the build page that shows how to look at thirty MintEye images and find the image with the fewest zeros at the end of the file. This is, by the way, the correct answer for the MintEye CAPTCHA, and has a reproducibility of 100%.
So, does anyone know if MintEye is a publicly traded company? Also, how exactly do you short a stock?











