[Brett’s] girlfriend is very concerned about cell phone security — So much so that she used a PIN so secure, even she couldn’t remember it.
Beyond forgetting the PIN, the phone also had encryption enabled, the bootloader locked, and zero permissions for the Android Device Manager to change the PIN. Lucky for her, [Brett] had purchased an STM32F4Discovery Development Board a few months ago, and was itching for a suitable project for it.
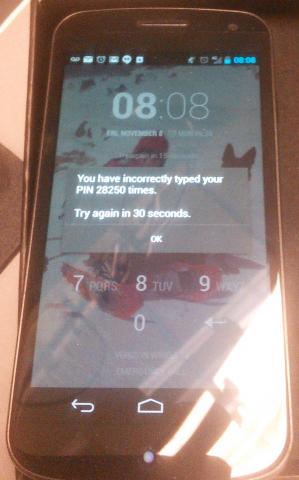
Now unfortunately, Android allows you to pick a PIN of anywhere between 4 and 8 digits, which as you can guess, results in a massive number of possible permutations. She was pretty sure it was only 6 digits, and that she didn’t use a 1, 2, or 3… and she thought it started with a 4 or a 7… and she didn’t think any of the digits were repeated… This helped narrow it down a bit, from 1 million possibilities to about 5,000 — assuming all of the boundary conditions she remembers are in fact correct.
[Brett] started by writing a C library to generate permutations of the PIN, testing the board on his own phone to make sure it works with a known PIN, and boom, they were in business.
28,250 PIN attempts later, they decided they were not. Did we mention you can only enter 5 PINs in every 30 seconds?
Head on over to his blog for the whole project, as its well worth the read!
http://www.youtube.com/watch?v=WTVO7_Sai9w
We‘ve covered lots of brute force hacking methods over the years, from the simplest solution of using a Teensy, to our favorite, an elaborate robotic finger that used servos and a DVD drive sled!
















Weak, it’d only take about 21 years to brute force all the 7 and 8 digit codes.
he could have unlocked it via something like cydia impactor within seconds if the device hadn’t been patched.
Doesn’t this belong under fail of the day? Valiant attempt, though.
The technology is working fine and the solution is still in progress. The point of failure here is someone else’s wetware…
Isn’t there an unlock service for, you know, actual purchased phones that you didn’t steal or buy from a thief? Or was it the data content on the phone that was the target? Photos and such?
They can still wipe the phone externally, but they’re not getting the data back from the phone.
actually you can recover the data
just get forensics device and recover it as if it contained some illegal stuff.
It won’t work as the data is encrypted. If you wipe the drive, you won’t be able to recover anything, and if you don’t wipe, you cannot access anything.
I’ve watched countless episodes of CSI – all you need to do is smash open the phone and put virtually any remaining piece of IC under a digital microscope that’s hooked up to a PC and boom! You can read the data back!
If you’re going to use a pin, have another way to get in.
https://www.google.com/android/devicemanager?u=0
On the plus side, her phone seems pretty secure!
They mentioned that android device manager was disabled. Ontop of that I have never once had it working
Just tested it on my nexus 4, turns out it was on automatically and it worked like a charm for locating my phone, however remotely locking and changing the password was not turned on by default
its turned on, tested on a nexus 7 and a sony Xperia M, fails to locate both devices every time. Ring button claims its successfully rung the device, it doesnt.
Confusing writeup at his blog.
First he says “This limited me to a guessing rate of about 510 guesses per minute.”
At the end he says “failure was due to simply having too large of a solution space to try with the rate limit of 510 guesses per hour. “,
What is it? 510 per minute or 510 per hour?
How did he get 510? 60 * 2 =120, 30 second blocks of time. 5 * 120 = 600 attempts?
What am I missing?
The 5 is a typo. He means 10 per minute (two lots of 5)
At least I thought he did. I didn’t see the bit at the end.
I guess it would be 600 except that inputting the pin is not instantaneous.
I now realize that time is spent issuing one guess and waiting for the Success/Fail response. That time, times 5, plus waiting 30 seconds after the fifth failure, adds to the overall time.
Sorry typo corrected that is 510 per hour (a little bit under 10 per minute). Could have made it faster but I had my 30 second delay set a little longer than it needed to be to make sure It didn’t start next round of guessing too early.
If you don’t mind voiding the warranty, the best way of breaking these is to get the CPU on jtag and watch what happens when you hit the okay button. At some point it must be doing a comparison between what you entered and the actual code, and you could either decode the actual code or twiddle the bits on the CPU to get it to let you in.
Nice solution, i like it.
jtag on hi-end ARMs has crypto handshake, no handshake no access.
Didn’t know that. I can see why they do it, but it still makes me sad.
If they did it well, that shouldn’t work. Instead of just comparing the PIN, they could/may have just generated a deterministic AES key from the PIN, and tried to decode the filesystem header with it. Failure to decode wouldn’t tell you the correct key. Twiddling bits wouldn’t have helped either.
He should have done a Factory Reset on the girlfriend. :-)
Is ADB disabled? If not then they could just manually extract or reset it from the command line.
ADB has to be manually enabled now. you have to go to settings, about phone and tap on the build number 6 times and you get a message that says “developer mode enabled” or something like that. then development options shows up under settings and there is a checkbox for adb in there.
You dont need any of this. Google Play gives you online PIN capture by installing applications to do it, like device manager. Even if you dont remember the PIN you could have access to the phone.
There are a lot of other ways to get around this, however none of them were available, I think short of JTAG which I read was locked on the Galaxy Nexus there was nothing we could do.
Can you still install software on the device through the Play Store website? If so maybe you can find an app that allows you to access your device remotely (without needing to set something up of course).
8 digits gives 100000000 combinations that is 100 million.
Next up, this guy will discover that after 50,000 consecutive failed attempts Android will announce that he has won the persistent looser award.
Volume Up + Power for factory reset didn’t work ?
Factory reset is easy, the goal was to not have to do that and not lose data which was unfotuneately not backed up.
It’s hard for me to believe that someone is THAT worried about the security of a phone. What is she worried someone will find? No one really cares that much about her selfies. :p
But he does specifically use the word ‘lovely’ a few times in relation to her… that might explain a few things.
My colleagues showed off a delta robot for doing this at DEFCON. Their presentation is posted here: https://www.defcon.org/images/defcon-21/dc-21-presentations/Engler-Vines/DEFCON-21-Engler-Vines-Electromechanical-PIN-Cracking.pdf. All of the files required to replicate their work should be available here: http://isecpartners.github.io/tools/ under R2B2.
I can see it now – guy spends days coding a solution to unlock her phone. Finally manages to get the phone unlocked, only to be dumped when he discovers she’s been cheating on him *insert Bad Luck Brian*. The PIN was obviously to keep him from going through her text history. Be an alpha and kick that bitch to the curb
Interesting, but wouldn’t “real” Alpha sense it was time to take action without further investigation? ;)
Lol, gotta laugh at the idea of the GF sweating bullets while pretending to be thankful. Of course, if that was the case she doesn’t have much to be afraid of because she was put in a position to give deliberately bade password guidance for shaping the attack.
I ever had was a standard inexpensive phone. I get a new one at a bargain price whenever the contract is renewed, because by that time the battery is getting tired. They transfer every thing from the old phone to the new one for me. I don’t know f t any PIN is copied or if it’s required to to the transfer or not, but if it isn’t would buying a new phone be a solution to get the data back? In the event it would it be a lesson to keep a copy of the PIN somewhere(not forgetting where), regularly transfer photos, have an old fashion address book you write in, newer ones even have a field for email too. Forward texts with important stuff to a web mail email address, if you don’t have email through a separate ISP In the event the phone has a hard reset that absolutely destroys all the data, you have a phone to sell to offset the cost of the new one. Or let your geek boyfriend to have to do something useful with as a small tablet computer.
Wow. I gotta commend the effort and add this helpful hint. If one is looking for an insanely long backup number look no further than under your phone’s battery ;) There is usually a serial # or Part # there that would suffice and it is right there if you are ever locked out. Seems like a rational concession to an overly eager phone encrypting life partner. Perhaps they should be the one doing all this though to begin with since they are sooooooo concerned about privacy and know everything else except the concepts behind it winky face. We have one around my house as well that is really great at breaking things and leaving them on my desk to fix. She really got to me with the laptop ac adapter ripouts until i forced her to use the modemplug trick. Kudos really, on keeping a level head with the whole ordeal.
What’s the modemplug trick?
Oh yeah sorry. The modemplug trick is just an extra layer of cord saving. Since we no longer use dial up networking, I take little bits of phone cord with the plug (less than 2″) and affix it to the power cable. When you have the power cable plugged in and the wire plugged into the unused modem it pulls on that useless thing and either breaks the wire or unused modem connector out worse case scenario. May not save the laptop from frisbeeing off to the floor but will save many an arse ;) Really any unused port will work as long as you don’t mind loss of function if all goes wrong but the modem imho is an easy and small connector. I actually got the idea from some guy that was selling them in the uk but it was like 10 bux for one so couldn’t really support the team on that one lol and just diy’ed it.
Can’t find the original but this guy uses a serial port on a quick search so you can get an idea of what is going on. Thanks and hope it helps, Edward :)
I am an overly excited idiot.
http://grandstreamdreams.blogspot.com/2009/02/laptop-dc-plug-protection-hack-safety.html
The link for the strain relief . God help us all lol.
Have you thought about building a magnetically attached power connection, ala apple laptop?
http://www.instructables.com/id/MagSafe-for-the-Rest-of-Us-A-DIY-Magnetic-Power-A/
Why not just ask the NSA?
How about doing a modified factory update? It doesn’t wipe the phone usually, and if you can get it to delete the correct file or run a command, you can disable the lock screen. He doesn’t list the phone model, but some phones let you load a factory update over USB once you boot up into download mode or the locked recovery. You’d have to find a way to fool the phone into running a modified factory update. Not the easiest thing to do but not impossible either.
This is a prime example of why you should always use a password you can easily remember, I myself use the length of my erect penis in millimetres, or course that’s only good for 4 digit passwords.
3 leading 0s; Thats not very secure!
Damn, and I was counting on nobody knowing the metric system!
If I use nanometers, I can use a 5-digit number. Not that I like to brag
Isn’t that the standard bluetooth password?
If she you, her, or others have not touched or cleaned the screen in the virtual-keypad area you might try a forensic technique to tell what numbers she touched. You need her face powder brush from her makeup kit and some baby powder from the baby’s diaper bag. Lightly dust the area and use a cheapish UV black light from Walmart sporting goods dept. to fluoresce the area (the black light baseball cap-light for $8). The finger tips should show up minimizing what characters to try and what not to try. It may even jog her memory if she knew what characters she likely touched. The order is not known however.
Failing that. Take her to one of those Hypnotherapy psychiatrists that does hypnosis for stop smoking and other things. They can have her regress back to when she last successfully logged in and she can read off out loud what numbers she touched that day.
I’d recommend a pad of Post-It Notes and a Nice Pen for her xmas gift. Is it really that hard to use some (any) method to remember passwords (keepass, sticky-note, etc)?
i used a pen and paper the other day to copy/forward/convert
the contents of an email (activation code, text)
from one end of the room to the other.
people were confused and suprised.
they had the genuine look of learning on thier faces!
i think they learned the ultimate compatibility hack;
if you can read it, then you can read it! simple!
take that you file-formats!
PS: quarter page of text in picture format embedded into DOCX
then embedded into PDF is stupid.
i dont care who the heck you think you are.
if you do this you are asinine.
PPS: thats loading the DLL files for THREE programs to view ONE file.
Does she work somewhere with a security camera? You could look over the footage (assuming at some point she unlocks her phone during the day there) and get some more information about the PIN, if not the PIN itself.
Six digits Eh? Hmmmm, a date perhaps, someone’s birthday or anniversary or whatever.
I guess the password wasn’t 8765309….
surely you mean 867-5309
oh its so funny how paranoid people are, whats the actual likelihood that anyone gives a crap about you, usually the perceived danger of “hackers” and “thieves” are way over proportioned compared to the actual likelihood of anything happening to you. Then you create some annoyingly stupid password/pincode that no one could every guess or remember and you write it on a post it not and place it next to your device for you to remember, completely negating the purpose of a frigging password/pin in the first place. then you turn to your boyfriend/husband for to play free tech support and rack thier brains trying to beat a dead horse because you want to save your selfies and text messages.
Somewhat OT, but certainly related.
Here’s a simple way to generate a PIN which is extremely easy to remember, but relatively difficult to brute-force guess.
Use an old obsolete phone number, something which you used so much in the past that you’ll never forget it, but something which you will never use again so it’s not something in your phone’s database. It could be your phone number while growing up, a former business where you worked, or something similar.
If you’d like something slightly more secure (although it’s barely worth the extra effort in terms of actual added security) add one to each digit. For example, use 867-5309 (the Jenny number) as a seed. The PIN becomes 9786410 – something you can easily generate on the fly and remember, but not something easy for somebody to guess – whether they know you, or by brute force.
Worst password advice ever – MetroPCS actually suggested that I use my birthdate as a password, one of the worst 8 digit PINs possible. The month only goes from 01 to 12, the days only go from 01 to 31, and the year is a maximum range of about 80 years. Not to mention that a person’s birthdate is relatively easy to find.
Eh… just use a USB Rubber Ducky to do the same thing… only a lot easier! http://hakshop.myshopify.com/products/usb-rubber-ducky
Is the PIN code not stored on the SIM card rather than the Phone? Try putting in a different SIM card with a known PIN and see if you can access the contents of the Phone that way.
No, these are different and separate PINs.
Can you brute force on screen locks like pattern lock?
Security or unlock PIN can be relatively easily guessed just by looking at the location of finger impressions on the mobile screen while it’s turned off.
It’s always advisable to check if your phone has an option to display the number pad (for entering the PIN) with random ordering of numbers every time it’s displayed.