It’s quite common to have a timed lockout after entering several bad passwords. This simple form of security makes automated brute force attacks unfeasible by ballooning the time it would take to try every possible permutation. The lock screen on iOS devices like iPad and iPhone have this built in. Enter your code incorrectly several times and the system will make you wait 1, 5, 15, and 60 minutes between entries as you keep inputting the wrong code. But there is an exploit that gets around this. [Pierre Dandumont] is showing off his hardware-based iPad lock screen attack in the image above.
He was inspired to try this out after reading about some Mac EFI attacks using the Teensy 3. That approach used the microcontroller to spoof a keyboard to try every PIN combination possible. By using the camera kit for iPad [Pierre] was able to do the same. This technique lets you connect wired keyboards to the iPad, but apparently not the iPhone. A bluetooth keyboard can also be used. These external keyboards get around the timing lockout associated with the virtual lockscreen keyboard.
We’re of the opinion that this is indeed a security vulnerability. If you forget your passcode you can simply restore the device to remove it. That wipes all of your personal data which can then be loaded from an iTunes backup. Lockscreens are paramount if a device is stolen. They will give you the time you need to change any online credentials which might be remembered by the device.

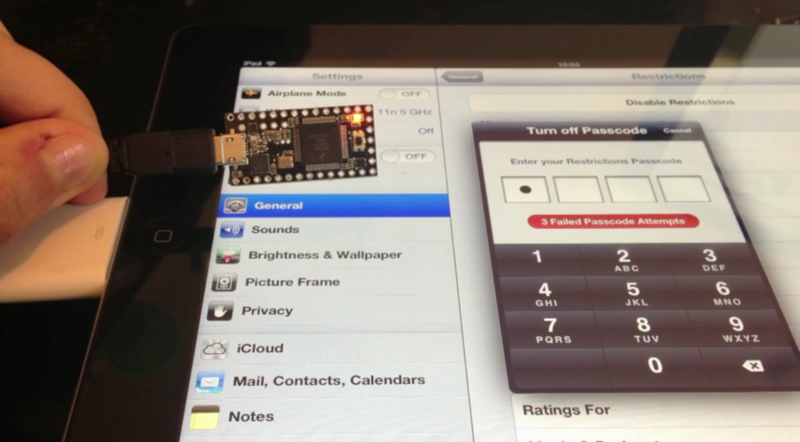















Does this also work on the main login screen, or just to disable the device pass code? If it only works in the settings menu, then this has much fewer practical applications.
>I first tested the password of the home screen, but it does not really work: after a few tries, the iPad is locked for 1 minute, then 5 minutes, etc.. Impossible to test the 10,000 options on brute force, then.
Useless, but still awesome.
He says in the article that it does *not* work against the lockscreen. Still a bug, but not as bad as if the lockscreen were affected.
News flash:
The restore of an iOS device would put the password back onto the device as well, rendering it the same condition you began with…
Facts, man… Facts.
False.
DFU Mode > Restore > No password.
Is this so as to learn the code, because I know you could unlock old ones with a USB hack. The time I did this was on an iPod nano, (I know, right?) but you don’t have to restore your device if the code is lost (as Apple would have you believe). My friend lent my the iPod with the unknown code and I Googled solutions (since I was NOT installing iTunes). It turns out you can just access the files over USB with your favorite shell and delete a file called “locked” (or something). Is that still a thing?
iOS devices have significantly stronger security than older ipods
4-digit passcode locks on older iPods weren’t advertised as security measures, but were more like a cheap padlock – Older iTunes even had an option to unlock iPods synced to it. iOS devices(AppleMobileDeviceService stuffs) are different and they need to be unlocked before syncing. So no, they are different.
This is not an ipad attack, it’s an anything with a usb keyboard attack and has been around forever.
No, it is an iPad attack. If my desktop computer has a password and input is disabled via the keyboard, I have no means of inputting a password. If an iPad only disables the onscreen keyboard, but still allows USB keyboard input, there is a hole there.
iOS already has a built-in option that wipes the device after ten incorrect PIN attempts.
That’s only if u enable it
All it did for me was locking the screen. Am I doing it wrong or something.
You can also change the password length to 8 numbers in the settings; a brute force hacker then will have to have way more patience… and it’s not that difficult to memorize 8 numbers if they are a combination which makes sense to you.
Republicou isso em Julio Della Florae comentado:
Add your thoughts here… (optional)
If the setting to erase the data on the iPad after 10 failed attempts is on, you could end up running in to a bit of trouble.
This is a major security hole. The iOS keychain is saved in backups in an encrypted state. It’s encrypted with a key that can be retrieved if the device is jailbroken.
However, if you have entered a passcode, that is used in the encryption as well, giving an extra level of security.
So if you have the passcode and this built-in encryption key, you can theoretically decrypt the iOS keychain from backups of the device.
Of course, if you already got a hold of the device and jailbreak it, the keychain is accessible anyway. So I don’t really know if this would give you anything extra…
so the attack would only work if you have an ipad which has not locked itself again. you go to the change passcode option until you get the right code. how ever, if you have an unlocked phone, would other attacks not be more efficient?
I guess if you don’t have or know other means of extracting data, once you have the code, you can take your time to extract what you need.
If you ever need to reset the parental lock and you have root access to the device, the passcode is stored in plain text in a plist file. You can either ‘recover’ it or reset it (https://www.youtube.com/watch?v=xeTIjqHRy0w). I assume something similar is possible with the lockscreen lock, provided the iDevice has remote SSH access activated.