It’s no surprise that there’s a lot of devices out of there that use simple RF communication with minimal security. To explore this, [Gordon] took a look at attacking radio controlled outlets.
He started off with a CC1111 evaluation kit, which supports the RFCat RF attack tool set. RFCat lets you interact with the CC1111 using a Python interface. After flashing the CC1111 with the RFCat firmware, the device was ready to use. Next up, [Gordon] goes into detail about replaying amplitude shift keying messages using the RFCat. He used an Arduino and the rc-switch library to generate signals that are compatible with the outlets.
In order to work with the outlets, the signal had to be sniffed. This was done using RTL-SDR and a low-cost TV tuner dongle. By exporting the sniffed signal and analyzing it, the modulation could be determined. The final step was writing a Python script to replay the messages using the RFCat.
The hack is a good combination of software defined radio techniques, ending with a successful attack. Watch a video of the replay attack after the break.
















Get a tripod your video make me sea sick.
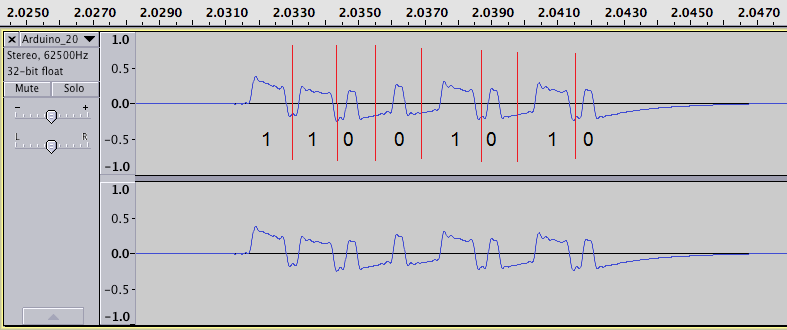
nice! do you or anyone else know if there is a software existing or a way how to decode the audio waveform automagically to binary format. so the the output from above audio file would be what you have done manually? I know it’s hard, but you should be able to setup first the analysis like frequency and how a 1 and 0 looks like. then analyize…
I use Audacity. I record it then chop out the extraneous details. Then expand what is remaining to fill the screen. It is usually pretty crummy yet but if you amplify it and chop off heh peaks it comes out to be a nice waveform. I have looked at my LaCrosse temp. sensor and teh abo e works fine.
rtl_433 can handle alot of OOK radio demodulation.
necro-ing this thread to make sure people know that https://github.com/atlas0fd00m/rfcat is the actual link for rfcat nowadays. Google Code is looong gone.