There are a lot of options for local weather stations; most of them, however, are sensors tied to a base station, often requiring an internet connection to access all features. [Vinnie] over at vinthewrench has published his exploration into an off-grid weather station revolving around a Raspberry Pi and an RTL-SDR for communications.
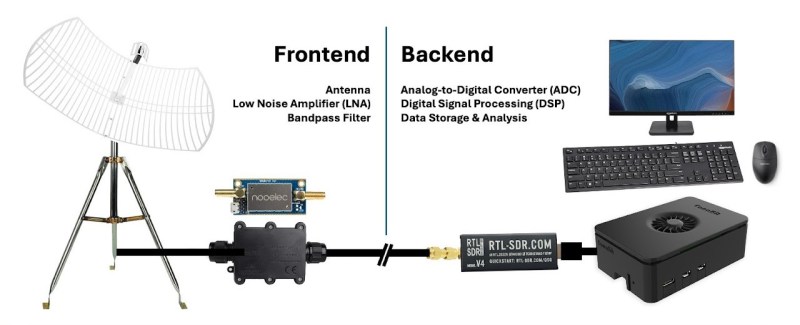
The weather station has several aspects to it. The main sensor package [Vinnie] settled on was the Ecowitt WS90, capable of measuring wind speed, wind direction, temperature, humidity, light, UVI, and rain amount. The WS90 communicates at 915 MHz, which can be read using the rtl_433 project. The WS90 is also available for purchase as a standalone sensor, allowing [Vinnie] to implement his own base station.
For the base station, [Vinnie] uses a weatherproof enclosure that houses a 12V battery with charger to act as a local UPS. This powers the brains of the operation: a Raspberry Pi. Hooked to the Pi is an RTL-SDR with a 915 MHz antenna. The Pi receives an update from the WS90 roughly every 5 seconds, which it can decode using the rtl_433 library. The Pi then turns that packet into structured JSON.
The JSON is fed into a weather model backend that handles keeping track of trends in the sensor data, as well as the health of the sensor station. The backend has an API that allows for a dashboard weather site for [Vinnie], no internet required.
Thanks, [Vinnie], for sending in your off-grid weather station project. Check out his site to read more about his process, and head over to the GitHub page to check out the technical details of his implementation. This is a great addition to some of the other DIY weather stations we’ve featured here.