A mass participation sporting event such as a road race presents a significant problem for its record keepers. It would be impossible to have ten thousand timekeepers hovering over stopwatches at the finish line, so how do they record each runner’s time? The answer lies in an RFID chip attached to the inside of the bib each runner wears, which is read as the runner crosses the line to ensure that their time is recorded among the hundreds of other participants.
[Ken Shirriff] got his hands on a bib from San Francisco’s “Bay to Breakers” race, and set about a teardown to lay bare its secrets.

Stripping away the foam covering of the RFID assembly revealed a foil antenna for the 860-960MHz UHF band with the tiny RFID chip at its centre. The antenna is interesting, it’s a rather simple wideband dipole folded over with what looks like a matching stub arrangement and an arrow device incorporated into the fold that is probably for aesthetic rather than practical purposes. He identified the chip as an Impinj Monza 4, whose data sheet contains reference designs for antennas we’d expect to deliver a better performance.
After some trial-by-fire epoxy removal the tiny chip was revealed and photographed. It’s a device of three parts, the power scavenging and analog radio section, the non-volatile memory that carries the payload, and a finite-state logic machine to do the work. This isn’t a proper processor, instead it contains only the logic required to do the one task of returning the payload.
He finishes off with a comparison photograph of the chip — which is about the size of a grain of salt — atop a 1980s 8051-series microcontroller to show both its tiny size and the density advancements achieved over those intervening decades.
Since RFID devices are becoming a ubiquitous part of everyday life it is interesting to learn more about them through teardowns like this one. The chip here is a bit different to those you’ll find in more mundane applications in that it uses a much higher frequency, we’d be interested to know the RF field strength required at the finish line to activate it. It would also be interesting to know how the system handles collisions, with many runners passing the reader at once there must be a lot of RFID chatter on the airwaves.
We’ve featured [Ken]’s work before, among many others in his reverse engineering of Clive Sinclair’s 1974 scientific calculator, and his explanation of the inner workings of the TL431 voltage reference. Though we’ve had many RFID projects on these pages, this appears to be the first teardown of one we’ve covered.

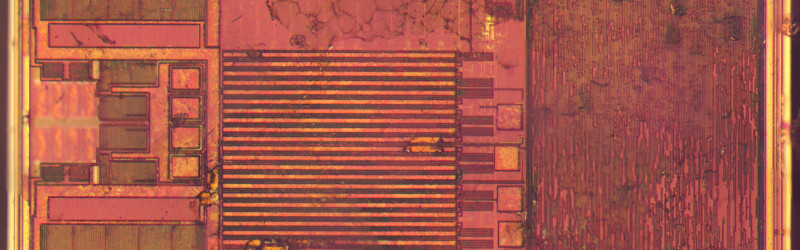














“The rectangles on the left are probably transistors and capacitors forming a charge pump to extract power from the radio signal”.
That was also my first thought when I saw the photo, but it may be also an automatic matching network.
Printed antennas have pretty high tolerances, and laser trimming them is a time consuming process, so many rf chips nowadays have automatic antenna matching, using switchable capacitors on chip.
I always thought it isn’t possibly to read more than one RFID-tag at once, so how do they do when a lot of people cross the end line of the race at the same time?
Use a swarm of readers?
The readers that I’m familiar with are amazingly good about it. The same tech is used for running and biking as well as motorsports, and it still amazes me when it can reliably pick up 3-4 cars crossing a line nearly simultaneously at triple-digit speeds. Part of it is that the spec requires a pretty close proximity for the transponder to the timing loop — and in the case of motorsports, the transponders are powered, active devices that broadcast their data out, not just wait to be activated. The passive chips used for cycling seem similarly robust, though obviously they aren’t seeing speeds as great. The riders are required to wear the chip on their ankle to keep it close to the ground-mounted loop.
One at a time, but really fast. Just has to get through all the runners while they’re still in range of the reader. My guess is the reader could read/register a dozen runner tags 1,000 times each in the time it takes that pack of runners to travel a couple feet. I think it just comes down to how the reader is designed and able to read and record
… and configured. You tell the reader a typical number of tags in view (among other parmeters), and that affects its cycle times, number of inventory attempts per cycle, parameters it speaks to tags regarding retry randomisation…
Reading a bunch of tags without conflicts is necessary for inventory control as well, so there are several clever ways they avoid collisions. One is “random-slotted collision arbitration”, where a tag waits a random amount of time before responding. There’s also a somewhat complex algorithm; basically the interrogator says “I heard from tag X, so X be quiet, anyone else?” and repeats until everyone has been inventoried. The interrogator can also ask for subgroups of tags at a time, “Anyone whose number starts with 1? 2? …” See the spec [1] for details.
[1] http://www.gs1.org/sites/default/files/docs/epc/uhfc1g2_2_0_0_standard_20131101.pdf
Thank you for these very interesting informations!
Where’s the hack. Clone that tag with a drone and fly it near/ over the finish line when you want to finish. See how the officials like that….phantom marathon runners.
They would laugh because the tag never passed the other checkpoints. But honestly; You think no one would figure it out even if you flew it through all the checkpoints? Sounds like a lot of effort just to be a troll.
I’m just rather surprised it hasn’t been reported/done…Or at least not caught yet. I mean who would think a tiny motor could live in the frame of a bike? That seems riskier than a modern day take of the Merry Melodies Tortise and Hare. Electric doping is here.
Quite frankly I don’t even think its a trolling effort. Many hacks are for tesring vulnerabilities of environments. Otherwise, why care about an RFID dye result? I can think of someone figuring the tracing of the microcapacitors to drain a tag with a undetectable pin point object and cause a dispute at the finish line when the tag is dead and they have no result..inversely maybe over power a tag to give it an extra inch or two of proximity. Similarly I think it would be a waste of time to root a phone, add an nfc app to get the tag info, relayed to multiple people around the course. But I think there are attempts and it’s gonna cause a stir. Quite frankly I can see some serious ways that someone could use this as an alibi to say oh I was at the marathon the day that….happened. And it’s hacks like those that need countermeasures I don’t think has dawned on anyone.
Finish lines are usually videotaped, there’s a clock in the frame, and the person is wearing a number. If the timing chip goes dead, that’s how they find your time.
Horses for courses.
Many low-key events still use barcodes. They’re incredibly easy to duplicate/forge, but rather pointless to do so. There’s still visibility of competitors; the tags are just for convenience of recording results. Are large monetary transactions tied to unverified, automated data collection at such events?
RFID tags often have a (modest) storage memory for data other than the tag’s ID. This can be protected by a programmable passcode. Tags also have programmable self-destruct. I’m not sure if the self-destruct can be triggered from brute-force passcode cracking, but I don’t see why it couldn’t be.
There was a NewYorker story (http://www.newyorker.com/magazine/2012/08/06/marathon-man) about a runner who somehow managed to win races from the back of the pack while no one ever saw him pass anyone, he changed clothes, and didn’t show up in pictures from the middle of the race.
One detail that caught my eye was that he went through checkpoints that didn’t exist. This made me wonder what exactly gets sent through the RFID reader. Is it just basically a serial number and the reader handles the rest? Or could you do some SQL injection with a spoofed tag that added lines to a database table, coincidently making a spot on the podium for you?
Higher frequency tags are used for longer-range with focused antennas. Regulations vary between countries, but 1W EIRP is a common limit for 900MHz ISM band use. In Australia, 4W EIRP is permitted for RFID only where necessary to achieve an outcome, and requiring the signal be constrained to the zone of operation.
EIRP: http://en.wikipedia.org/wiki/Equivalent_isotropically_radiated_power
Have you heard of TRAFFIC.COM?
The company was initially started by a handful of professors from Penn State University in University Park, PA. Their online portfolios on the TRAFFIC.COM website (circa late ’90s) indicated that they each had worked for the CIA.
Somehow, these guys got major funding to get holes dug along U.S. highways to have concrete footers poured; erect 50ft high stainless steel posts; attach a stainless steel utility communication box with a UHF antenna; above it there is a RFID transponder box aiming down at the roadway at what appears to be a 45° angle; above this is a solar panel; and atop the pole is a camera that can be rotated 360°. This configuration is then repeated over and over again along the length of the highway(s).
Pittsburgh PA was the beta site for this venture, and TRAFFIC.COM has since been sold many times, with name changes, and has expanded to 51 cities across the country.
https://en.wikipedia.org/wiki/Traffic.com
Lockheed Martin was contracted to do the installations (an interesting choice).
The Pittsburgh Post Gazette had reported that Lockheed was behind in their work, and was being fined $2000 per pole, each day, that was not completed.
The website had revealed a host of its tracking abilities, which is no longer being posted. It uses RFID backscatter to obtain a vehicle’s VIN (Vehicle Identification Number); count cars; calculate speeds; indicate direction of travel; and apply a timestamp for each; all in one swoop.
The camera gives a visual verification of occupants. One such camera along the Parkway East, Route I-376, is perched at a level looking into the windows of a group of houses located in close proximity to the interstate. Home owners complained to the media.
https://www.google.com/maps/@40.4294111,-79.9413187,105m/data=!3m1!1e3?hl=en
The system can locate and track a car which contains a wanted criminal, then disable the acceleration of the vehicle, keeping the car operational so it can be safely steered and braked until the vehicle comes to a rest. The suspect is not spooked, thinking he has been rescued when a State Trooper pulls up behind him.
Any item in the car having a RFID tag, not shielded, which responds to the transponder’s frequency when pinged, also gets reported. Privacy advocates beware. Shoplifters beware!
A diabolical fantasy of mine is to hack the system to disable every single car along the highway(s) during rush hour in order to wake people out of their sleep.
There is much, much, more… but I don’t want to write a book. Maybe later.
: