RFID tags are great little pieces of technology, but unfortunately, the combination of paper, metal, and silicon means they are as bad as some modern pregnancy tests — single-use electronic devices that can’t be recycled.
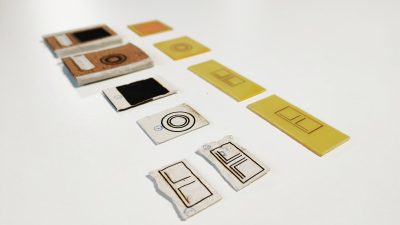
A team of design program graduates from London’s Royal College of Art aim to change that. They’ve devised a mostly-paper RFID tag that’s as safe to recycle as a piece of paper with a pencil doodle on it.
The team’s startup, PulpaTronics have created a design that uses paper as its only material. The circuitry is marked on the paper with a laser set to low power, which doesn’t burn or cut the paper, but instead changes to composition to be conductive.
PulpaTronics were also able to create a chip-less RFID tag much the same way, using a pattern of concentric circles to convey information. The company estimates that these tags will reduce carbon dioxide emissions by 70%, when compared with traditional RFID tags. They’ll also cost about half as much.
RFID is used in many industries, but it’s also great for hacking. Here’s an 8-track player that harnesses the power of RFID tags to play songs off of an SD card.
Thanks for the tip, [gir.st]!