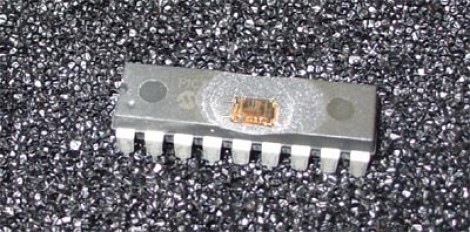
A few years back [Bunnie] took a crack at cracking the security fuses on a PIC microcontroller. Like most of the common 8-bit microcontrollers kicking around these days, the 18F1320 that he’s working with has a set of security fuses which prevent read back of the flash memory and EEPROM inside. The only way to reset those security fuses is by erasing the entire chip, which also means the data you sought in the first place would be wiped out. That is, if you were limited to using orthodox methods.
[Bunnie] had a set of the chips professionally uncapped, removing the plastic case without damaging the silicon die inside. He set to work inspecting the goodies inside with an electron microscope and managed to hammer out a rudimentary map of the layout. Turns out that flash memory can be erased with ultraviolet light, just like old EPROM chips. Microchip thought of that and placed some shielding over the security fuses to prevent them being reset in this manner. But [Bunnie] managed to do so anyway, creating an electrical tape mask to protect the rest of the data stored in the chip while bouncing UV light underneath the shielding at an angle.
Want to uncap some chips of your own without enlisting the help of others? Give this method a try.
[via Dangerous Prototypes]















Now *this* is Real Hacking. Very nice work! ;-)
“…inspecting the goodies inside with an electron microscope…”
No, I think all he needed was a good optical microscope, probably 50 or 100x at the very most. Optical microscopes are usually sufficient for reverse-engineering chips like the PIC on a circuit level. You only need to resort to electron microscopes if you need to resolve individual circuit element construction, or you’re looking at the very latest chip from Intel. (Actually in the latter case, your biggest problem is going to be digging past the thick stack of metal layers to even get to the actual devices.)
Scanning electron microscope, regular microscope, what’s the difference? Servo, stepper, same thing right? I like you Hack-a-day but I’m really starting to feel sorry for you.
Most UV filters aren’t actually 100% effective. I suspect that given enough UV (think a 250 or 500 watt bulb) would be more than enough to bruteforce through the UV filter. Those things will give you a sunburn in seconds.
Need to watch the heat output though.
What did he use to dissolve the chip case? Sulfuric? Nitric?
Always love to see [bunnie]’s work.
Original Teensy bootloader anyone? :-D
@Hackerspacer: It says he had the chip de-capped professionally. They probably used RFNA.
I’m not sure what you’re talking about there with respect to UV filters. All he had to do was tip the chip at an angle to get the UV light to bounce under the shield. That’s certainly easier than using a 500W bulb. Are you trying to say that he could just blast light through the case? I don’t think that’s going to happen…
Really slick work.
So whats the next step? If you’re able to dump the flash contents to file, you’re simply left with the code in assembly opcodes and the data. Reverse engineering that would most likely take longer than simply copying the product.
But I think the main advantage would be for recovering data on the IC. Maybe if the chip is used for some kind of security application with codes saved on the flash.
really hardcore and inspiring
-thank you
Uh, isn’t that chip vulnerable to the much, much easier attack described under “Breaking Microchip PIC18F CPU copy protection” here?
http://www.openpcd.org/HID_iClass_demystified
i want decode hex and c source file from 18f452
russiansemiresearch.com can decode to C.
oh my god! Real hacks on hack a day!
@vtl,
1. If he had the flash data he could just burn it to other pic’s (and copy the product)
2. A lot of PIC users program in assembly and we’d be fine with the data once it was put through a dissembler. No need to reverse engineer.
3. He’s a hacker he hacked the chip.
The linked to method is unlikely to keep logic in place/working, as even the author mentions. Which matters when you want to dump data.
Didn’t someone describe a way to access (=read out) avr flash overriding the fuse bits somewhere here in the hackaday comments?
I’ve read many times that it is possible but I didn’t find a way to do it, unfortunately.
The first real hack on HAD in a couple of years. This one utterly ROCKS!
Super crunchy Kudos! This person is a Uber HaXor in every sense of the word. All others are posers in their shadow…..
We are not worthy….. We are not worthy….
Ye I remember a similar article somewhere but can’t remember where. What would be interesting now is to see an example of FPGA with Anti-Fuse attack method… I believe that one requires and Ion Scanner to “set” the fuses again. Any one have any info?
hardcore
Great hack. Wonder were he got access to an elec. Microscope or did he used his own, made by himself.
Microchip should have mixed in some parity bits for this very reason… imagine a checkerboard pattern of lock bits where an unlocked state is checked one way, locked is the inverse, and anything else such as “all clear” resets the chip.
I’m thinking out loud, but they could also have layered parity bits directly on top of the lock bits.
For those who question the use of being able to reset the security bits on protected chips, one big use is to read out the data from old consoles, arcade machines and computers (many of which used protected chips to prevent unauthorized copying)
Sir I would like to unlock and creack atmel ic at89c51ed2 through you send me charges for this job
$850 by russiansemiresearch.com