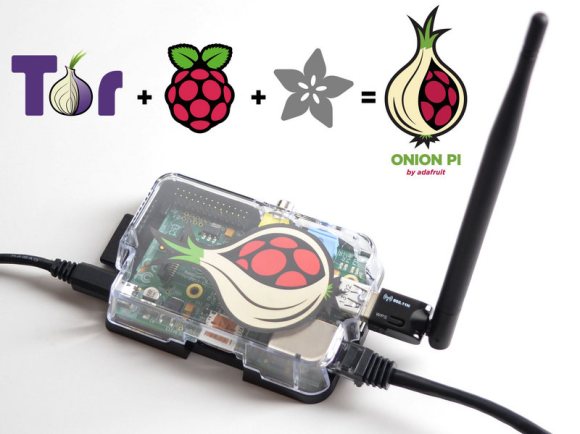
Your web traffic is being logged at many different levels. There are a few different options to re-implement your privacy (living off the grid excluded), and the Tor network has long been one of the best options. But what about when you’re away from you home setup? Adafruit has your back. They’ve posted a guide which will turn a Raspberry Pi into a portable Tor proxy.
The technique requires an Ethernet connection, but these are usually pretty easy to come by in hotels or relatives’ homes. A bit of work configuring the Linux network components will turn the RPi into a WiFi access point. Connect to it with your laptop or smartphone and you can browse like normal. The RPi will anonymize the IP address for all web traffic.
Leveraging the Tor network for privacy isn’t a new subject for us. We’ve looked at tor acks that go all the way back to the beginnings of Hackaday. The subject comes and goes but the hardware for it just keeps getting better!















Very nice! Wouldn’t it be possible to use two wifi dongles? One that connect to an existing wifi network and one to broadcast a secured wifi for your computer?
Yes, they actually go into detail on this farther into the how-to.
depending on the wifi stick and drivers, you can connect to one ap and act as an ap at the same time
its a bit tricky, but you can do both at once with a single card
“tor acks” ?
ack!
ACK! Ack ack ack. Ack.
(yes, we are picking on a typo. with a bad movie reference.)
I guess the get acknowledgments from way back at HaD
I’m not enitrely sure what’s the difference between this and having TOR browser on your unit as a SW setup. Please enlighten me if there is any
You have an excuse to carry your rPi around.
You cant really run TOR on most mobile devices, such as cellphones, ipads, kindles, and the like. With this option, you can connect your mobile devices to the internet just as safely as you can your laptop.
>You cant really run TOR on most mobile devices,
Tor should run one most rooted Android devices.
Tor has no purpose on pads/cellphones. I would definitely never ever trust any pad or cellphone, rooted or not, for keeping sensitive data or secret communications. Seriously people, those traps contain applications that access all your data and can (will) phone home as soon as they can. Phoning home through Tor doesn’t make them less dangerous when a single app can make a blob of some personal data (you allowed them to) and upload it elsewhere.
With an Android device, you can install the development package, connect the device with USB and then leave the debugger logging all app activity.
The pre-installed Facebook app on my phone, that I never use and can’t be uninstalled, phones home every night. Eventually I’ll root the phone and rip out that app. Meanwhile facebook.com is blocked at my router.
r3, if you are using a Tor proxy like this, all of your traffic over wifi (and then to the Internet) is guranteed to be proxied by Tor. If you are using it in your browser, there are situations where not all browser traffic goes through your proxy and none of your non-browser traffic will go through the proxy for sure.
“The technique requires an Ethernet connection, but these are usually pretty easy to come by in hotels or relatives’ homes.”
This is a silly statement. Of course you could just do the obvious thing and reverse the forwarding rule and then connect the ethernet side to your PC and the wireless side to the available internet connection.
Or you could just create a wireless to wireless bridge.
Your wifi router doesn’t have an ethernet jack to plug into? How odd.
It’s interesting, when I first started playing around with tor (mostly out of curiosity, at the time I didn’t really have an over-whelming reason to fear of everything I say and do on the internet being logged) connection speeds were terrible…worse than dialup, generally speaking. At this point, you can do pretty much anything you need to do through it, at somewhat reasonable speeds.
And the more people who utilize the network, the faster and more stable the network becomes. All to the good, really, given the fact that the real world is often even stranger than most conspiracy theorists would have imagined, online privacy wise.
At this point, you can do pretty much anything you need to do through it, at somewhat reasonable speeds.
Yeah, the NSA has some nice pipes.
Just run iMosque and you’ll disappear from their lists.
I had to google/bing it, and to be fair to the spooks, they watch everyone. The US of A Government is one of many Peeping Toms, voyeurs of the world.
Honestly I think all governments do – oddly enough it is probably part of why peace is kept.
OT, but that is one nice little enclosure.
Actually more on topic then some comments…
From my old Usenet days, I consider ‘OT’ to mean on-topic, allowing all other discussion to veer wildly off course. As it inevitably does, even nearly two decades later.
It’s a surprisingly useful mental trick. :)
It should be noted that while Tor is a great first step at anonymizing your web traffic, services like WebRTC which use UDP connections in addition to TCP will not be routed through Tor. That’s something I’m currently trying to work around though. ;)
It should be noted that while Tor is a great first step at anonymizing your web traffic, services like WebRTC which use UDP connections in addition to TCP will not be routed through Tor. That’s something I’m currently trying to work around though. ;)
They’re selling this as a $95 kit. I can’t really believe that similarly priced (or even cheaper!) WLAN routers/aps wouldn’t provide significantly better value. Get a TP-link, install OpenWRT and add Tor, should give you similar results, but on a hardware that’s actually designed for networking, and as such most likely has significantly better IO performance.
This is just one of the things RPi is bit suboptimal for.
Just be aware that whoever is running the Tor exit node you’re using may be snooping on you as well. They won’t know where the connections are coming from due to how Tor routing works but if your connections aren’t encrypted then they’ll be able to capture the contents.
TL;DR – Make sure to encrypt everything e.g. SSL and to check that nobody is messing around with the certificates when you’re using Tor.
What you say is very true, but probably won’t make sense to those that don’t already know. What with the jargon and everything.
How about setting up a VPN on that RPi with TOR and leaving it at home, most devices have VPN connectivity implemented (my Android has it) and all you need it send all traffic via your TOR connected RPi at home… or am I missing something?
You are not missing anything. The raspberry pi is a computer, so posting anything software related about it and calling it a “hack” is like telling people that you can install FireFox on your x86 computer.
I’m missing the part why i’d go to these lengths to cover my private data. People think they’re special snowflakes, unique one of a kinds. But in reality no-one bothers snooping on you because it’d be boring and pointless…
Too boring and pointless? That used to be true. Now, we have machines that are capable of sifting through your data, and they don’t get bored. As to whether it’s pointless, I’m sure the multi-million (billion?) dollar PRISM programs were set up as an idle pass-time.
The US government is spying on its own citizens more so than the KGB ever did (although less heavy handed). The EU isn’t far behind, and is at the same time dealing with a heavy push towards an impopular government-by-decree, rather than having actual representation. Those sorts of circumstances do not point towards the growth of benevolent government.
What happens when you some day want to exercise your right to protest against government, and instead you’re dragged out of bed the night before, because ‘they’ heard you?
Many EU countries are worse than the US actually, they just don’t have the funding the Us has so they can’t match the datacenters, but what they pull is often even more outrageous.
But from the US it’s more shocking since they come from a starting point where you expect some more limits.
How about using those cheap android media players like MiniX, MK802, whatever, they have WiFi included (and power adapter!!), so if you add another dongle you have a totally wireless system, and are avaliable worldwide via multiple dropshipping pages! and maybe cheap!!
Or you could just get a regular pi and type sudo apt-get install tor
This almost seems like a gimmick to be honest, sure it will be good to have if your company wont allow you to install anything on their systems. Other than that. I have many openwrt devices I can just throw tor onto.
More importantly: You can’t go on 4chan through tor
There is no problem accessing 4chan through Tor … try it again.
4chan anonymously confirmed ;)