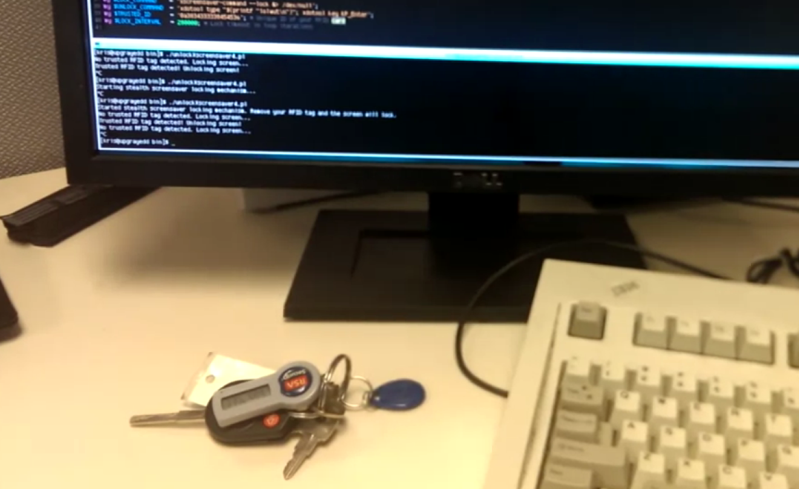
We don’t know how [Kristoffer Marshall] found himself with free time at work, but he used it to beef up his computer security. Above is the finished project. There is literally nothing to see here. He’s rigged up a hidden RFID reader which locks and unlocks his workstation.
The security of the system depends on xscreensaver, which has a password protected lock feature already built into it. When the tag is removed from the reader’s field it fires up the screensaver using a Perl script.
But waking up from the screensaver is a bit more tricky. The package doesn’t allow you to wake it from the command line — most likely for security. He found the xdotool to be of great use here. It is a command line tool which simulates keyboard and mouse entry. His script detects when the xscreensaver password prompt is on the screen and uses the xdotool to fill in [Kristoffer’s] password. Since the script knows what has focus it won’t give away your password by accident.
See the complete setup in the clip after the break.














ive had to do it before, ctrl+alt+f1, login as root, killall xscreensaver
its ugly, but you can unlock the screensaver by force if you can -9 the screensaver
This could be a better solution with a passwordless sudo to kill the screensaver than to store the password in plain text and have a script input it… Some pam libraries also work with RFID modules, like Pam mhcrfid, witch could then turn off the screensaver. Did something similar a couple years ago with a usb key.
dont need sudo either, if you run killall as the same user as the script, root isnt needed
It’s ugly, but it might be better better than leaving your password in plain text in an xdotool script.
Although I do suppose suid-ing the script could be almost a bad.
ALL=(ALL) NOPASSWD: /usr/sbin/killall
Problem solved. You could only grant passwordless sudo access to the killall binary.
I just found out Hack A Day strips out bracket characters.
[username] ALL=(ALL) NOPASSWD: /usr/sbin/killall
So what happens if you kill init? ;p
Oooh… dat IBM Model M…
That was what really caught my eye. I do miss those, I either want that keyboard or a smooth silent one.
http://www.pckeyboard.com/
There you go. Unicomp still makes a number of models with buckling springs.
Hey thanks for the site :)
So his password is stored in the clear on his machine so his script can type it in for him? Doesn’t sound like a good idea to me.
Their home directory is probably automounted from a central NFS server (for backups) and not stored on the local workstation. And NFS does not have any encryption by default, so it could be snagged from the wire in plaintext (at a guess).
Even worse – you don’t need to threaten him with a crowbar to get his password. Just steal his keys, put them near his machine, and you’re in.
does xscreensaver run as root? seems odd that you can engage from script but cant disengage.
No. Keys belong in the pants pocket (trousers to the Brits). I’d find myself at my car with no keys, but unable to go back and get them because the keys are on my desk.
Yea I’m that way as well. The only time my keys aren’t in my pocket is when they are in a vehicle ignition switch or next to my checkbook- cellphone- pocket knife-wallet- watch on a stand by the front door.
using pam in the back would really be the better idea!
xscreensaver uses pam to check the password but using pamexec you can execute an external script to auth and you can have a xscreensaver specifig pam config. this way different users canuse different rfid tokens to unlock only their sessions, etc.
So……..? We get a two minute video to waste our time showing us what a simple written sentence or two could describe.
No parts list, no hardware config description, no installation notes, code example buried on the Youtube page which you didn’t list in your write up, etc etc. Basically NOTHING but a fluff video.
The headline brought me in, and the content kicked me out shaking my head in bewilderment.
http://www.youtube.com/watch?v=uQl5aYhkF3E
since his rfid key fob is readable by any rfid device, this is as secure as having that secret token as a barcode on a piece of paper and a barcode reader.
security through obscurity.
oh btw this key fob id is 0x3834333338454536 – it’s right there in the video…
By that logic, all RFID based security is security by obscurity.
The goal here is that if his environment doesn’t have his keys (a form of physical thing) at his desk (his security zone) his machine (the security zone’s arbiter) locks (does the right thing).
It’s a clever hack, and it’s a cheaper way than how some folks have done it.
There are public key crypto RFIDs, actually I think I use somekind of crypto RFID everytime I go by subway I’m pretty sure it’s hackable though.
Although the theory sounds great, it doesn’t look very practical (takes several seconds to lock/unlock), and it does not sound even remotely secure given that the password is stored in cleartext. Hopefully he at least had disk encryption so that people can’t mess with the root shell.
Actually, it looks like PAM is the only option to properly close xscreensaver. Per the FAQ:
“Warning: never use kill -9 with xscreensaver while the screensaver is active. If you are using a virtual root window manager, that can leave things in an inconsistent state, and you may need to restart your window manager to repair the damage.”
If you’re looking for another option, use PAM as others have pointed out or switch to another screensaver.
Who cares about the unlock, he’s rockin an IBM Model M keyboard. Much more important.
I’m glad somebody else caught that. I miss that sound.
Blueproximity does this with BT and it manages to lock and unlock, at least on Ubuntu when I used it. Maybe Kristoffer can use the same mechanism. It’s certainly better than hardcoding a password.
http://nfc-tools.org/index.php?title=Pam_nfc
Looks like the right way to do this
XScreenSaver author here. This is a cute idea, but the proper way to do this is to write a PAM module that recognizes the presence of the RFID. That’s how other non-password-based authentication systems (fingerprint readers, retina scanners, etc.) work. The bonus of doing it this way is that it works for authentication from normal login prompts too, not just xscreensaver. On another note: it’s great to see that the kiddies up thread still think that “kill” is spelled “kill -9” always. Sure, go ahead and start from there all the time. I’m sure that’ll work out great for you.
Yay jwz! I love you!
I think this is why everyone hates techies. No matter the age, many throw around a juvenile, condescending attitude.
Man, almost everything in this comment thread is mentioned in the Xscreensaver FAQ or manpages and has been for ages. It’s just a matter of RTFM:ing
There must be an error in the original post language. If it “detects when the screensaver prompt is on” and then disables the screensaver, then I could walk up to his terminal and jiggle the mouse to get in. I assume this is handled by his script, but the hackaday post doesn’t make that clear.
Hi all! I’d like to thank you for the constructive comments! This is pretty much a proof of concept right now. I’ve put in a total of about 30 minutes worth of programming into the script, so it’s nowhere near polished. All physical access is controlled here at work and all my work is cloud based. This script is purely for convenience so my fellow coworkers don’t fool with things like Facebook and G+. With that said, PAM authentication may be in the future for the script. This currently works for my purposes though. Take the code and modify it to your liking.
And yes, IBM Model M keyboards are awesome.
Your “proof of concept” should at least include PAM authentication. Writing a PAM module should be pretty easy to do. Ive never done it myself, but it should only take a couple of minutes. And your using a plaintext password? REALLY?! WHYY!? Did you write this on your lunch break or something? It works, sure, but i bet i could do better if i wanted to. And i bet youre using NFS liek the other guy said to back up your laptop, because thats what you linux people do. Whats this, the 90’s and youre using linux? Or better yet Samba! Haha! I bet youure using samba.
Bottom line, your doing it all wrong.. you cant sell this to me if you wanted to. its like you just put something together to see if it works.
I really like it as a way to lock the workstation when he leaves. I don’t like that it unlocks it when he gets back. Something you have and something you know is always best.
Sync matching oscillator in monitor via screensaver duh