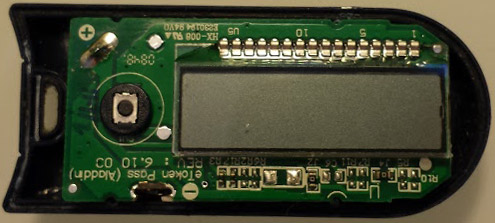
One-time passwords (OTP) are often used in America but not so much in Europe. For our unfamiliar readers, OTP tokens like the one shown above generate passwords that are only valid for one login session or transaction, making them invulnerable to replay attacks. [Dmitry] disassembled one eToken (Aladin PASS) he had lying around and managed to reprogram it for his own needs.
Obviously, these kind of devices don’t come with their schematics and layout files so [Dmitry] had to do some reverse engineering. He discovered six holes in a 3×2 arrangement on the PCB so he figured that they must be used to reprogram the device. However, [Dmitry] also had to find which microcontroller was present on the board as its only marking were “HA4450” with a Microchip logo. By cross-referencing the number of pins, package and peripherals on Microchip parametric search tool he deduced it was a PIC16F913. From there, it was just a matter of time until he could display what he wanted on the LCD.
We love seeing tiny consumer hardware hacked like this. Most recently we’ve been enthralled by the Trandscend Wi-Fi SD card hacking which was also one of [Dmitry’s] hacks.















I’m from Sweden and all the major banks use something similar. My bank’s little box includes a credit/bank card reader as well. It can be used to log in to the bank, sign for online payments, log in to sites with sensitive information (such as doing your taxes) and so on.
Surely other European countries have something similar as well?
Agree, they are used everywhere. Not only by banks but also for access to corporate VPN connections or other remote acceess solutions.
I know that some european country banks used them for a while, not sure if they still do, but the point is that yes they are in more european countries.
But the world isn’t just US and (western-)europe so it’s a good thing it was briefly explained.
Uk here – all the major banks use these also, and have for many years.
**ALL** major banks?
really? the UKs biggest bank, (lloyds TSB) which is so big that it’s been forced to split into two separate companies doesn’t use them.
Romania too. They are really common
Most banks in the Netherlands use this too. Insert your card, choose what you want to do, and enter your PIN
No this isn’t a pincard, this is a thing to create ‘TAN’ codes I think the name is, the numbers you need to do payment with online banking.
For my old German bank they used to give you a printed list of one time codes you used (and crossed off when you did) for online banking until they moved to this system.
Microchip is pretty standard with their programming pinouts, once he knew the programming pad layouts, he could just have used any programmer [set to 3.3V first] to read out the chip type ID.
They are pretty common used in in Europe, altough lately phone app’s or SMS codes take up a part of the use.
In Denmark we had a digital signature, then a OTP and now we get mailed a little card that includes codes. You get prompted with a number which you find on the little card and write the corresponding pass sequence into the browser. Different larger companies use OTP’s for VPN access.
ehh “used in usa, not much in europe” thats complete bullshit
Such useful comments :/ Anyway, it was a nice hack and an interesting read. Always interesting to see how people find out what undocumented components are. Part of the fun!
Seeing a strange model number on a chip with a familiar brand I would have assumed that they made something custom for the token manufacturer or at least something they don’t offer on the public market. I would have probably given up.
Is this kind of thing common? Should I assume that all or most parts with strange model numbers are really just familiar ones with a strange label? Or did he just get really lucky?
In my experience with various vendors over the years is that no one makes anything custom. They just re-use what they can to make custom solutions. That or they just whitelabel or OEM an existing product line for different customers. I would say if it looks like a duck and qucks like a duck but it’s painted purple…it’s probably still a duck.
I’d probably have done the same. This is a bit of an eye-opener for me.
Probably was one of the pre-programmed chips that microchip does. (You can order a lot of MCUs with your code already on them).
If you have an account with HSBC tell them you have lost yours(in bank) and they just hand you another. No questions, no paperwork etc :)
Same thing with Swedbank in Sweden.
Nice. Wish our banks had that.
We’ve used SecureID for over 15 years, from the credit card-sized password generators to the key fobs we currently have for VPN access. Next time my key fob expires, maybe I’ll take a crack at it.
Yea I think the author has it wrong – they’re widely used in Europe but not used at all in the US
They’re certainly used in the US, at least by 3 major banks that my employer uses. They’re not used by my credit union (where I keep my personal account), they use SMS instead.
SMS is so easy to intercept though I hear, but oh well.
Look at this from Marcan42, a USB token singing!!! http://www.youtube.com/watch?v=QiTNlSgk-xY
It just shows the text of the song though.
In the US the majority of special purpose login methods are via a Smart Card. One of the credit card companies did issue an easy pay method using them, but found that not that many bank companies were interested. Or people as well. The same device was first used by Sun Microsystems as a do-everything for their entire network and buildings. Eventually such widgets found their way to the cans made by Dallas Semiconductor and then Maxim. Those things were used briefly here, before the Smart Card device, outside of the US I believe they are.
Like the Java Ring?
How are you going to log into a site and do a transaction with a smart card? You’d need a special smartcard reader on your computer, and each computer that you use, and each phone.
This is for online banking, online, on a website.
Hmmm, it can be a good start to implement the OTP protocol for Gmail authentification !
Nicer and more practical than a phone in fact
People would throw a fit if they had to enter a whole new code read from a display each time they gathered their mail.
Then after the fit they would close their account and switch to another provider.
Great job, this is areally cool hack! Of course it serves no purpose but it is cool non the less!
I’m not sure where you’re getting your information, but all the major banks in Norway use OTP chips too. I’ve had one of these for 10 years or so.
Do your universities use them in the US? In Netherlands they use them everywhere to login the network, students just need the password.
OTP = One Time Pad, not One Time Password. It comes from the days of encryption codes being provided on paper pads (think post-its)
Nope. While one time pad is also abbreviated “OTP,” that’s not what this is. A One Time Pad is a pre-generated list of values. One of the key differentiatiors is that a well-done one time pad can’t be predicted; the values should not come from any predictable sequence. In this case, this token generates a one-time *password* using a pre-defined algorithm (probably HOTP) applied to a shared key and a sequence counter. HOTP is defined in RFC 4226 (see RFC 6238 for another common One Time Password implementation).
These key fobs are initially set up by taking the pre-shared key and generating a few (usually 3) consecutive values on the fob. The authentication backend then uses the algorithm to generate (basically) each possible outcome for every sequence number to find where in the set of possible outcomes the keyfob currently is at. That tells the backend where to start the sequence counter. Going forward, the backend authenticates by expecting one of the next several possible values (usually ten-ish) to account for the button being pushed inadvertently a couple of times. If the user provides a code from the near future, the counter is then resynchronized on the backend. If the user falls out of sync by hitting the button too many times outside of an authentication scenario, usually there’s an alternative means of authenticating to a system where the pairing process can be repeated, resyncing the counter. The counter also rolls over at some point (usually somewhere on the scale of tens of thousands), which is why it’s relatively easy to calculate most of the possibilities quickly.
Nope. While one time pad is also abbreviated “OTP,” that’s not what this is. A One Time Pad is a pre-generated list of values. One of the key differentiatiors is that a well-done one time pad can’t be predicted; the values should not come from any predictable sequence. In this case, this token generates a one-time *password* using a pre-defined algorithm (probably HOTP) applied to a shared key and a sequence counter. HOTP is defined in RFC 4226 (see RFC 6238 for another common One Time Password implementation).
These key fobs are initially set up by taking the pre-shared key and generating a few (usually 3) consecutive values on the fob. The authentication backend then uses the algorithm to generate (basically) each possible outcome for every sequence number to find where in the set of possible outcomes the keyfob currently is at. That tells the backend where to start the sequence counter. Going forward, the backend authenticates by expecting one of the next several possible values (usually ten-ish) to account for the button being pushed inadvertently a couple of times. If the user provides a code from the near future, the counter is then resynchronized on the backend. If the user falls out of sync by hitting the button too many times outside of an authentication scenario, usually there’s an alternative means of authenticating to a system where the pairing process can be repeated, resyncing the counter. The counter also rolls over at some point (usually somewhere on the scale of tens of thousands), which is why it’s relatively easy to calculate most of the possibilities quickly.
So is there a cheap source for these fobs?
I have not seen one used in this part of the U.S.A.
In spain we are primitives…your bank give you a card paper with numbers. Sad and cheap :-)
I like that system plenty.