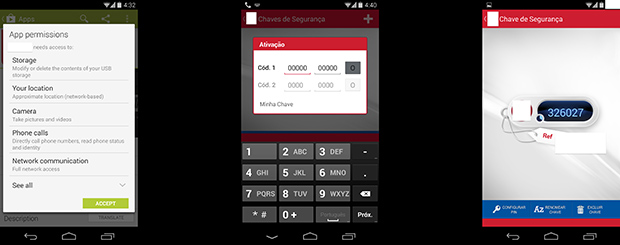
[Thiago]’s bank uses a few methods besides passwords and PINs to verify accounts online and at ATMs. One of these is a ‘security card’ with 70 single use codes, while another is an Android app that generates a security token. [Thiago] changes phones and ROMs often enough that activating this app became a chore. This left only one thing to do: reverse engineer his bank’s security token and build a hardware device to replicate the app’s functionality.
After downloading the bank’s app off his phone and turning the .APK into a .JAR, [Thiago] needed to generate an authentication code for himself. He found a method that generates a timestamp which is the number of 36-second intervals since April 1st, 2007. The 36-second interval is how long each token lasts, and the 2007 date means this part of the code was probably developed in late 2007 or 2008. Reverse engineering this code allowed [Thiago] to glean the token generation process: it required a key, and the current timestamp.
[Thiago] found another class that reads his phone’s android_id, and derives the key from that. With the key and timestamp in hand, he figured out the generateToken method and found it was remarkably similar to Google Authenticator’s implementation; the only difference was the timestamp epoch and the period each token lasts.
With the generation of the security token complete, [Thiago] set out to put this code into a hardware device. He used a Stellaris Launchpad with the Criptosuite and RTClib libraries. The hardware doesn’t include a real-time clock, meaning the date and time needs to be reset at each startup. Still, with a few additions, [Thiago] can have a portable device that generates security tokens for his bank account. Great work, and great example of how seriously his bank takes account security.















I almost wonder if his “legitimate user just getting annoyed at inconvenient security” story is a line. This story is really amusing, either way. :3 And scary.
… and then I read the disclaimer at the top of the linked article. Not *quite* as scary. Still funny, though.
Funny, my bank uses a digipass device by vasco to generate login codes based on my smart card and pin, and I’ve been yearning for a mobile app solution instead since I keep forgetting to take the device with me when on the road, meaning I cannot do online payments.
@Jeroen,
The digipass can’t be reversed in the same way. The smart card does all the cryptography, and your digipass is just a trusted keypad and screen. And the chip is strongly protected against being able to read its contents, unlike a phone app.
I’ve been all over the world, and have seen bank solutions that use smart card debit reader and browser plugins, apps with kergens, two factor auth inside SSL HTML, audio port mobile card swipers..
Some vulnerable to RCE(the keygens), all vulnerable to memory scraping and inline hooking.. Most importantly: all designed by mostly computer illiterate teams and designers who convinced a major financial entity that they were security experts..
sales and economics dictate security design, not talent and logic..
Looks like you’ve missed Portugal. Besides phishing, there’s little or no chance to get in. At least on major banks, and SIBS or MBNet. Good look finding holes there.
If there are no bugs known it does not mean that there aren’t any. ;) I think there are no such interested people in doing that in portugal. Remember that if a system is compromised and the system notices it, they might be interested in have that person on that side hiring him. Unless we are talking about a poser that wants show of but im convinced people with this level of skill goes for the right thing or at least the most profitable one.
E sim, também há buracos nos sistemas portugueses ;)
Right, but even ATM are considered more secure than the US ones. It’s not just me saying that, or a personal opinion, some other countries and companies say that our network is really better in tech terms.
Acredito que haja, mas não ao nível dos USA, como ter backdoors nas ATM com manuais publicados online ;) :)
BTW, I don’t work for any of that entities………unfortunately, lol :)
“Some names have been changed or removed to protect the innocent”
you may want to have altered the screenshots of the transaction pages to remove anything that other bank customers who are hackaday users could recognize and identify the bank if the bank name is one of those removed or changed
wait, i dont get this,
does this mean the bank is offering an app for smartphones ???
are they really THAT stupid ???
do people REALLY fall for this ???
if i told you that you should change your password to “password”, would you?
i mean seriously, cellphones DO NOT HAVE SECURITY, perioud.
if people are STEALING point-of-sale terminals in broad daylight to
“get into” a bank…
then why the (hell) would you LET someone access a bank with a CELLPHONE
let alone write a software program (app) for it, let alone encourage it.
bluetooth wallet, check
wifi wallet, check
GPS location, check
NFC wallet, check
paypal wallet, check
being told your account in negative $1000000000$ because “the phone did it”,
priceless
for everything else, theres CASH
ps im NOT talking about people stealing the cash drawer along with the register/computer!
im talking about people stealing the card reading / pin pad devices
because apparently this is how modern thieves do it, outiside the movies.
Ok, explain to me what’s the difference about using a web browser on your computer to access your bank account, access that same bank account through a mobile device and finally having an mobile app on your phone that basically opens that SAME website?
I use that app day-to-day and I must say, it’s great. In example, If someone tries to rob me and my phone “accidentally” falls to the ground and brakes, I will simply not be able to withdraw any amount of cash from my account, simple as that.(I have to input the token’s number for each transaction.
The mobile app is basically the same as visiting the bank’s website, except for that “token” part. (Wich is also password protected before it shows you the number).
Using cash is ridiculous, you can lose it, get robbed, simply annoying.
by cellphone i meant also desktop computer, which is less secure anyway.
in the old days you had to have an approuved/client address / callid
if people can bank from thier computers/cellphones then the whole damm network is open, perioud.
how the hell do you think i got YOUr bank/pin ??? lolz JustKidding but seriously…
I LOVE TO GET ROBBED!!!
why? CUZ THE CASH IS ALL YOU WILL GET!!! HAHAHA
tomorrow it’s over!!!
the next day’s cheque is safe and sound and im back home drinking beer thats why.
instead of you following me around and watching everything i do, the whole way being able to mess with my head. i’d prefer loosing the 20$ in my pocket in exchange for being secure the rest of my life!
PS: never mess with a technician in his shop, he has you out-weaponed!
every time the bank asks me for my phonecode i tell them i dont have one, they promptly undo all the nefarious activity and i get my money back instantly, without me even knowing it was gone.
if i had a telephone or webbanking login they would investigate everytime, and while they do that i go home without beer.
sweet isnt it?
Uh… Many banks supply smartphone apps. Bank of America allows us to deposit cheques, transfer money etc. pretty much whatever you want.
You don’t know this?
You did not read the article. All the app does is generate temporary PIN codes that, along with a username and password, allow the user to log into their bank account through a web browser. Web-based banking has been around for a long time, and people are rarely hacked that way unless their computer is compromised or they use an unsecured/public network.
This is an awesome hack and from the looks of it, the bank actually got things RIGHT with the security such that even with the algorithm documented, you still need various per-user secrets for the info to be of any use.
Obvoiusly, security is in the token/credentials and not the algorithm, sustend security in algorithm secrecy is from the XIX. It is the same as saying your house is secure as long as no one knows where you live..
I wonder is it possible to hack the Digipass 260 to do something else, like turn it into pocket watch? I found 2 devices, locked up and restarted one, looks like the 4 screws used to hold it together are also some sort of electrical connections: lt – ref, rt – out, lb – in-r and rb – in-l. (Maybe some factory interface?)_