Feeling the cost of commercial options like the YubiKey and Nitrokey were too high, [TheStaticTurtle] started researching DIY alternatives. He found an open source project allows the STM32F103 to act as a USB cryptographic token for GNU Privacy Guard, which was a start. All he had to do was build a suitable device to install it on.
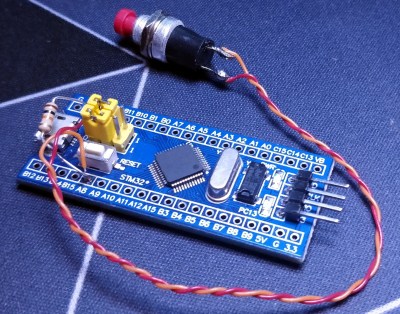
The first step was to test the software out on the popular “Blue Pill” development board, which [TheStaticTurtle] documents in the write-up should anyone want to give it a try themselves. The ST-Link V2 was already a supported target, so it only took some relatively minor tweaks to get running and add support for a simple push button. The output of gpg --card-status showed the device was working as expected, so with the software sorted, it was time to take a closer look at the hardware.
To create his “TurtleAuth” dongle, [TheStaticTurtle] started with the basic layout of the Blue Pill and added in a TTP223E touch control IC. The original Micro USB port was also swapped for a male USB-A connector so the device could be plugged directly into a computer. An upper PCB, containing the status LEDs and touch pad, was then designed so it would fit over the main board as an enclosure of sorts. While the sides are still open, the device looks robust enough to handle life in a laptop bag at least.
While it’s not exactly a common project, this isn’t the first time we’ve seen somebody spin up their own hardware token. More evidence of what the dedicated individual can accomplish these days on a relatively limited budget.