Introduced with the iPhone 5 nearly two and a half years ago, Apple’s Lightning connector has stymied the incredible homebrew electronics scene that was previously accustomed to the larger, older, better documented, and more open 30-pin connector. Now, finally, the protocols inside the Apple Lightning connector have been broken. We’re still a ways off from a Lightning breakout board, but this is the first proof that a serial console can be obtained through a Lightning connector. That’s the first step to totally owning an iDevice, and this is how all those exploits will start.
[Ramtin Amin] began the teardown of the Lightning connector began as most reverse engineering tasks should – looking at the patents, finding a source for the connectors, and any other products that use similar hardware. [Ramtin] found a Lightning to Serial converter powered by an STM32 microcontroller. Disassembling the firmware and looking at the output on a logic analyzer, [Ramtin] figured out part of the protocol, most of the wiring, and after some research, schematics for how an until-now unidentified chip in Lightning-enabled iProducts was wired.
The chip in question is colloquially known as the Tristar, and more accurately as a CBTL1608A1. During the teardown craze of the iPhone 5 launch, this chip was frequently identified as a DisplayPort Multiplexer. It is a mux, but not for DisplayPort – it’s only to connect the accessory (Lightning) UART, debug UART, baseband, SoC, and JTAG. This is the key to the castle, and being able to get through this chip means we can now own our iDevices.
The chip is an incredibly small BGA affair that [Ramtin] desoldered, reflowed onto a breakout board, and connected to an STM32 Discovery board. Using the techniques he used with other Lightning-enabled hardware, [Ramtin] was able to connect his iPhone and ever so slightly peek his head into the inner workings of his device.
It’s not complete control of an iDevice yet, but this is how all those future exploits will start. [Ramtin] uploaded a short video as a proof of concept, you can check that out below.

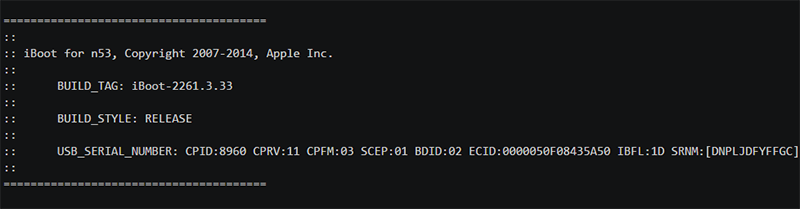














i guess yay!
Two words… Forget Apple
I can’t, I see the logo all around me… In my house!
You mean these guys?
https://www.eff.org/files/nsa-eagle-no-circle_0.jpg
That image sir or madam is entirely too Badass.
Of course, that would totally make sense in Europe….. You aluminum hat wearing nutcase.
@voxnulla
Seriously? I am a conspiracy theorist, at least as much as the next person, but I am intelligent enough to know that an aluminium hat cannot stop a standing scalar wave like a Faraday cage. If there were a chance that could even remotely work, I would be wearing one right now…..
@voxnella
Except they were actually discovered with a room at AT&T, listening in on every customer…
Hard cider
Yeah, people really how no business providing money to a corporation that treats its slaves so bad they have to install nets on their factories to keep them from leaping to their deaths… Just sayin.. What kinda human being would support that.. You should be ashamed of yourselves.
You mean Foxconn? They manufacture devices for many different companies, not just Apple. So, if you have bought any Chinese or Taiwanese products, you most likely directly/indirectly supported Foxconn with your money.
You mean Foxcon? Whose factories are the size of towns in the UK or US? And you’re surprised they have a significant suicide rate?
Or don’t hack iDevices. It will only make Apple make a new custom protocol that doesn’t meet with anyone elses.
I the process, they will adopt all of the things the hacker community has created, and introduce them to the world as Apple’s very own “Innovations”, even though they didn’t (and really don’t) innovate anything.
your stockbroker told you to buy apple, you recited this rant to him and now you are bummed at how much money you didn’t make
^^ …posted from F’s iPhone
You REALLY don’t get it…
One thing apple stoke was the multitasking app switcher. I remember jail breaking my iPhone 3GS and installing the home brew multitasker. It was the next major iOS revision that apple stole this idea and even copied the layout. Another feature I added was the quick reply to messages. Instead of loading up the app, could reply on the spot. Similar to how android allows a quick reply from the pull down menu. I don’t know if apple ever stole this but if they havent, then they clearly missed the mark.
erm, you know thats all they have ever done?
Hmm, what is wrong with this picture: so you give Apple lots and lots of money buying their products and they in turn use it to close their product, put all kinds of restriction on how a user cannot use them and then, you spend a lot of time to reverse engineer it? Does this make sense? Sounds like you let somebody install a lock in your house (an expensive one at that) and then lose access to something you own, because the lock actually does not work for you, it works for somebody else, at which point and after having spent all that money, you then have to find a way to break it so you can again gain access. Access that you should have had from the start ;-)
ups just clicked on report by accident
my simple comment for this: welcome to the apple logic
that’s apple, a big giant fluster cluck of backwards thinking and stupidity.
which happens to appeal to the large non-tech market and make Apple now have revenue more than GDP of some countries… (e.g. UK & Australia)
http://www.independent.co.uk/news/business/analysis-and-features/how-apple-become-so-successful-that-its-total-revenue-is-bigger-than-the-gdp-of-some-countries-10007454.html
Cipolla’s five fundamental laws of stupidity:
Always and inevitably each of us underestimates the number of stupid individuals in circulation.
if you had bought apple stock instead of apple products (YOUR CHOICE) you’d be singing a different tune
This is a pity reply for a very bad trolling attempt. Keep it up* and you will be a famous troll sometime in the future!
(* but not here and other sites I frequent please)
Ciapolla would term these people “naive”, rather than stupid. Preferring a simple-to-use, functionally integrated device (at the cost of capital/privacy/accessibility) is often preferred by people whose talents and/or interests lie outside of the minutae of hardware hacking – people who would be considered not-stupid in most contexts. Look at the number of programmers/network people who exclusively use Apple products.
http://en.wikipedia.org/wiki/Carlo_M._Cipolla
quote:
Look at the number of programmers/network people who exclusively use Apple products.
Huh? What are you talking about? That is a TINY fraction of people and I wonder who they are and how well trained they are, limiting themselves to such a small and mediocre computer infrastructure. There are for example no servers from Apple to speak of. The majority of programmers/network people use PCs with Windows or Linux on it, because it is much more versatile, more programs exist and it offers much more freedom. Last time I checked, Apple had a Market share of the professional computer market of like 8% or something.
So you would have to write “look at the number of programmers/network people that exclusively use PCs”, then it would be more accurate.
For people that live too much in the happy prison that the Apple ecosystem is, people that don’t know what is going on in the real world, it might sometimes seem like the whole world is only Apple ;-)
And using PCs exclusively is not hard, it is similar to saying that you are exclusively dwell on earth, as there are not many people living on the Moon and outer space ;-)
Most devices are actually equally easy to use these days. There’s almost not distinguishing factor for the standard Browser/Facebook/Twitter/Instagram/(CandyCrush/Party Games/etc) combo that most people use exclusively.
So, to me, it doesn’t make any sense.
Heck, my mom can use her Galaxy Note 3 perfectly fine 99% of the time unless she wants to do something she’s never done before.
@nigratruo
You say Apple had 8% as if that is a small amount. You fail to acknowledge the fact that Apple is ONE company commanding that 8% in a market with MANY other competitors which always get lumped together as a single entity. When it’s Apple vs. the world, 8% is quite impressive.
Apple is very successful but they don’t have more revenue than the GDP of the UK and Australia. I think you were looking at the graph of iphones sold compared to the country populations.
Australia gdp is over 1.2 trillion a lot more than your sorce says, 298 billion
Look at it from a security standpoint, to Apple and others, having all this proprietary and restrictive use makes the device “secure”. These kind of things scream out that it isn’t :D
who needs proof when you’ve got anger on your sude
I can’t speak for everyone who buys Apple stuff, but I can give you an example you might not have thought of.
I strongly dislike Apple, yet I’ve bought two items from them in the past. Why? Portable music production. I would’ve much preferred to be supporting more open platforms, yet in that one niche it’s basically a choice between Apple or living with unnecessary restrictions. For example, I’d prefer to use Android equipment but audio lag on Android devices is universally awful, and has been for at least 5 years: https://code.google.com/p/android/issues/detail?id=3434
A Linux tablet may prove a decent option one day, but they’re practically nonexistent at the moment, and Linux’s audio stack is a mess right now.
Until the time when stronger competition emerges I’ll stick to Apple for music production, even if I’d rather be spending my money elsewhere. Apple hacks like this one are a welcome development.
> Linux’s audio stack is a mess right now
That has always been and if it isn’t ALWAYS true, I’d be legitimately surprised.
You can always uninstall/disable Pulseaudio and use straight ALSA.
The reason PulseAudio was invented was to get around limitations that exist in ALSA, such as lack of per-application audio controls, and JACK is still recommended to enhance ALSA for low-latency audio applications. Compare this with Core Audio on OSX/iOS, which handles the whole range of audio requirements in a less fragmented way.
It’s not in a less fragmented way though. Being a BSD derivative, you can still install ALSA and PulseAudio software on those computer.
So it’s MORE fragmented because there’s 3 competing standards now.
Pretty much. It’s one of the largest weakpoints for Linux as a desktop OS, in my opinion. The situation isn’t hopeless though, look at what’s happening to the graphics stack, all the DRI/DRM and associated Wayland/Mir stuff, a sizeable step forward from the X.Org era. If the willpower was there, similar structural improvements could be made to the audio stack.
I can’t speak for everyone either, but I installed Ubuntu on a windows 8.1 “netbook” and sound works great so far. Ubuntu even tracks volume settings for headphones and build-in speaker separately, and reliably switches between the two when plug/unplug headphones.
As does Windows
For some hackers, owning a hacked Apple device is a badge of honor.
The more I think about the way Apple operates, the more I keep coming back to the auto industry. New models on a regular timeline, for example. Also, when you buy a car, none of it is open. Can’t modify anything on the ECU, fuel maps, timing, whatever. Sure, some things are locked down/obfuscated for safety/gov’t reasons, but I wonder if Apple’s thinking is along the same lines. There is a recent rumor/leak that Apple is making a car themselves, so maybe I’m not that off. They’ve been trying to emulate the auto industry for awhile, I think. Although, the user can still replace the battery in their car without sending it to a specialized repair shop! :p
Sure you can; it’s just not as easy as popping out the factory EEPROM and putting in an aftermarket one. Most of it is done by intercepting the signals on the CAN Bus and manipulating them on the fly to do what the user wants. These things are regulated to some degree, of course, for precisely the reasons you mention.
Right, but I mean, it’s not like the car comes with a company-sanctioned downloadable app that lets you modify fuel-maps. It still takes tech-savvy and some effort, all while probably voiding your warranty.
It’s often as easy as ordering the tuning tool for your vehicle engine model from an online or mail-order retailer like Summit Racing Equipment and plugging it into the diagnostic port on your car. In other cases, like what I was considering for my 2003 Chevy S10 at one time, you have to find someone that saw a niche market that knows how to reprogram the actual ECU to accomplish the same thing. Yes, it potentially could void the warranty, but so can many of the other modifications that are generally done to vehicles in the name of increasing performance.
Voiding the warranty? As in, all of it? Automatically?
Modifying an engine -may- void the warranty of that -part- of the car and any downstream parts, but only if it breaks. But even if it breaks, the impetus is on the manufacturer to prove that the modifications caused the damage being claimed by the consumer.
No modification, at least in the US, can automatically “void” a warranty. On anything, from cars to cell phones to wristwatches. No matter what the warranty document itself says, or appears to say.
See: Magnusson-Moss Warranty Act. (And please don’t anyone bother replying until you have seen it.)
If the warranty says that extensive modifications to a product will void the manufacturers responsibility for paying for or replacing the product……… then your right. The warranty isn’t void because they are still following the contract… the contract says they don’t have to pay. So aren’t technically voiding a warranty, but they sure as hell don’t have to pay for anything. Implied warranty only works for very low price items and everything under the sun in the US is limited warranty.
Do some more homework, buddy. Most vehicles can have the ECM modified with very little effort.
…but that does not necessarily mean that the ECM is open source.
“DRM-laden restricted junk” and “open source” are totally different animals. There is a huge difference between not publishing data sheets and actively preventing owners of your product from using it how they see fit.
Nice attitude. Define “most vehicles” and “very little effort”.
“If apple made cars” your car would only be able to drive tot he apple store and back home, the car would be available in black or white (tho you could put any colour cover on it you wanted), and its slogan would be “think different”
Its ok tho, people who bought the m$ car are still trying to get the securrity system to work and get rid of annoying messages so they can go anywhere with it.
:)
Doesn’t Apple make Tesla? If they don’t, you could have fooled me. Their stores might as well be ajoined at the mall……
Honestly that’s what “hackers” do here: reverse engineer things.
It’s not just apple lol
Plus one onnigratruo comments.
Locked hardware is the reason I dont support Apple and won’t buy any of their products.
I hope the protocols cracked but in the end it won’t matter if you dont support Apple in the first place.
tell us more about how your experience with the “unlocked” hardware in dell and lenovo computers and how you are able to modify their firmware and reverse-engineer their internal interconnects
What the hell are you talking about?
I can run whatever I want on my Lenovos. And work has Dells. There’s nothing stopping me from running whatever I want on them.
In Apple Land, you need the mother ship’s permission to do anything outside what was already blessed by Apple. And I say, Fuck That.
Do it then. Go flash new firmware onto them.
Oooh better, run your own microcode. And your own firmware.
CLEARLY you have never tried to, say, install a better wireless card in a Lenovo laptop, or upgrade the motherboard or PSU in an early-00’s Dell desktop. It’s not the software that’s the problem in most cases but what you can do with the hardware.
The only thing proprietary about desktop Dell computers from that vintage was the ATX knockouts at the back, and the front-panel connectors…both of which can be resolved with a cutting implement and the ability to splice wire.
The PSUs were bog-standard. I was buying Dell PSUs for general replacement purposes around that time because they seemed to be reliable in the sea of unrepentant trash that was all over the market at that time, and I likewise had no problems replacing dead OEM supplies in Dell computers with whatever Staples or Office Max had on-hand in a pinch.
(Dell did do a stint of BTX designs which had their own difficulties, but BTX was designed by the same sort of standards-body that ATX was and also had generic parts available for it at the time. It never did catch on with the public, but just because it was an unpopular layout does not mean that it was impossible to find generic replacement parts for it.
“In Apple Land, you need the mother ship’s permission to do anything outside what was already blessed by Apple.”
What are you even talking about? Anyone can run whatever software they want on an Apple PC, including Windows and Linux (and triple booting between all the major operating systems too). There aren’t any restrictions.
I don’t buy Dell or Lenovo either and certainly whitelisting components in the BIOS should be shunned as well but this conversation was talking about an external peripheral interconnect and last I checked USB, ethernet, and HDMI were all standardized and have published specs. 25 years in the computer business and 14 years in computer manufacturing and have yet to buy big name brand systems for the desktop or server for that matter. If you can’t build it yourself then support a local computer manufacturer who doesn’t cripple the BIOS.
I really could not care less anymore about restricted hard- and software. I tried to FOSS the hell out of every real field of production I have been known to dabble in with linux systems and dedicated hardware that wasn’t locked down, but is just does not work. In the music studio, as a graphics designer, hardware ad software developer and as somebody who also maintains the family and corporate machine park, Apple simply works better in every respect and unless the restrictions are going to hinder that, I’m not going to switch back.
If hard to hack proprietary stuff makes it possible, then all the more power to them. I also do not buy into those slippery slope fallacies where Apple is going and how this is going to harm X,Y and Z.
It seems to me that only a tiny group of people is vehemently anti-choice and that’s the open hardware evangelistic movement. And what has this movement done better than say that audio-stacks or GUI’s on linux? Not a lot.
agreed 100%
consumer products today have many many proprietary connectors and it’s a fools errand to think that there is some sort of practical value in hacking them
there are plenty of well-documented well-supported ways to connect stuff to a computer, you don’t need to hack into every vendor’s cable.
what’s the point? what’s the application? why the effort? I could reverse-engineer the cable that goes to the front door of my car, but what is the point? Who cares? What does the hacker get from lightning that makes it worth the effort? You can’t get at what you want from USB?
Debug console to iBoot for fuzzing
I’m working with a team of programmers that would like to support Apple iDevices with their software and a hardware device we want to build, but the proprietary connectors used limit our options (low volume, limited target market). It’s reverse engineering projects like this that make the end goal of cross platform support achievable for us.
How low volume are we talking about? We got MFi approval and chips for a production of just 2000 devices. The MFi program is free, you get all the information you need (which is much more than what’s being shown here). Chips and connectors are easy to order in sample quantities.
I’m not sure hacking the protocol is the way to go for a product you’re planning to sell since it’s quite likely this method will be locked out, especially if it opens the possibility of abuse.
But of course it’s up to you, if you want to burn your business down in support calls and problems then don’t let this advice stop you..
True enough on the risks. Apple’s Developer program seems more geared for commercial manufacturing rather than hobbyist projects, which is more or less what we would be; we were planning to do at least some of the hardware ourselves, rather than outsource the manufacturing process, as even 2000 pieces is more than we expect to have a market for.
Are we taking bets on how long we need to ignore F before he will change his name yet again? How many names has it been now?
I’ve noticed that he hasn’t been bragging about his superhuman strength and intelligence, and how he has somehow had every job in the world (and how he was the best at it and everyone else was stupid) and how he has been to every country in the world. I kinda miss all those stories, even if they were so ridiculous. Now he’s just angry all the time.
:( Poor F. The life of a troll must be miserable. I’m sure it gets very lonely under the bridge.
Dunno, F’s tone is usually crass but not inflammatory, IMHO. Never saw the job or travel comments, though. That being said, I agree with most of F’s comments on this story.
Nice try, F! ;)
I don’t know, off-topic anti-apple flaming could also seem like trolling, however seeing as that devalues the meaning of the word, I choose to see it as everyday fanatic tech-activism which is mostly found in the lower classes of the FOS(S) fandom.
Are F’s comments topical to other comments? Mostly. And are they just as topical regarding the article? Mostly. Well, then I think you probably have on your hands not deliberate anti-stance against the consensus here (or trolling), but rather a difference of opinion.
That being said, I did however not see F make any random assumptions about anybodies accommodations or their loneliness.
“That’s the first step to totally owning an iDevice”
“get through this chip means we can now own our iDevices”
“It’s not complete control of an iDevice yet,”
http://i.imgur.com/Sd2B3Ca.gif
Apple tablets make great cutting boards. I guess sometimes there is no point to it other than the challenge.
Unfortunately, they’re not even good for that. The glass will fold the cutting edge on your knives over, making them dull and dangerous. Best off just using them as a salad plate or platter for fetching burgers off the grill.
Can we ignore the standard “Apple is evil for locking their devices” argument for a second and just say this is awesome? Awesome job mate!
Indeed. The whole device hack ethos is largely about doing stuff with and to hardware that the manufacturer did not intend it for.
It is a bit suspicious that a single brand of hardware vendor is singled out and is being advised against, not only using but god forbid try to hack it.
I don’t think there is actually any security there.. I think there just isn’t any documentation.. I’d be surprised when all is said and done if there is any cryptography at all..
Some Chinese manufacturer probably already has a working implementation for market..
Whether you like it or not, the Lightning and Magsafe connectors are both genius in their simplicity, size, safety and capabilities (in the Lightning case). USB was a struggle from day one and still is. Mini/micro are better, but the center of female connectors are known to break.
I am very appreciative of the open source community, I tinker with and fix everything I get my hands on and try to build and program things to learn. I also admire the jailbreakers, who allow us to add cool stuff to our devices. Yet I see no reason why Apple should allow me to mess with the baseband, strengthen wifi signal or make the device compatible with my home made toys. Yet they do offer an amazing application base that basically anyone with programming knowledge can learn and they provide enough information to be able to easily use all hardware peripherals in those apps.
I understand both parties, because I use the best of both worlds. I may spend a couple hours making my own GPS tracker, program it with applications on my Macbook, test it out visually outside on my iPhone. I’m OK with what each of these worlds offers me and I don’t see why they should blend into one giant “do whatever you want with any device you want” mess.
This hack is a nice effort, yet I too am afraid the only one who’ll (unfortunately) take widespread advantage of it may be China.
I’ll reserve comment for Lightning. However, Apple should never been allowed to secure a patent for Magsafe. Magnetic safety connectors have been around on household appliances for decades!
No they don’t; none of Apple’s iOS products support Bluetooth Serial Port Profile, which is something a number of devices I know use to connect to PC and Android devices. To be able to use them with an iOS device, the hardware developer would have to add Wi-Fi support, which in the case of one project would require an extensive redesign and likely much larger battery.
Yes, lightning and MagSafe are awesome. Standardising on micro USB was a complete fuckup. Another non-symmetric connector, to match USB’s General poor plugability. My android tablet has micro USB and micro HDMI, and they’re both non-symmetric, and are so close in size I have to be careful not to force one into the other and break it.
How many of you Apple haters have an ipad/macbook? They are good products. Very good.
IMO anyone wanting to take a prototype of their own to the pre-production stage should have a look at what Apple devices look like inside and understand how beautifully hardware can be designed to be made compact in size, but powerful at the same time. The Macbook shell and board layout is hardware engineering and design pornography, something haters/lovers alike should acknowledge and take an example from when designing things at home.
I dont think anybody is denying the artistic skills of the products. To bad tho, that such beautiful products are chained to a golden cage ecosystem with limiting capabilities for tinkerer. If only they were perfect in design, hardware AND open development. It is not like they are that good in design because of their closed sources.
What exactly is it that you’d want open sourced? What is more open on an Asus or Lenovo? I have had thinkpads for years, used to repair them, and I don’t see anything more open about them, except easy battery replacement.
IBM did have extensive repair manuals back in the late 90’s.
I don’t know what the insides of current Apple laptops are like but the aluminum G4 was a hideous nightmare of excess parts and a shitload of screws everywhere. Every peripheral component was connected to the main board with a thin flex cable. Two connectors smack up against each other, with a stubby cable connecting. Every other laptop uses a single connector, with one half on the peripheral component and one on the main board so they plug directly together.
All those connectors and cables = more points of potential failure and much higher costs.
Even the frame was that way. Many threaded posts welded to the shell for the cast metal frame to screw to, instead of just gluing the frame to the shell. That would have saved cost, been lighter and stronger.
It’s as if Apple specifically designed those laptops to require human assembly, like something out of “The Midas Plague”, designed to have as many parts as possible. More parts don’t equal a better computer, they just make it cost more.
Pop forward some years and the iPhone 5C is fully robot assembled and the design simplified to make it easy to put together, but also glued to make it near impossible to take apart.
One good thing the US Congress could do is update the law requiring Lead Acid and Nickel Cadmium (I don’t recall if it covers Nickel Metal Hydride) batteries in consumer electronics to be easily removable. It was a mistake to specifically identify types of batteries instead of simply stating any current or future chemistry or configuration of rechargeable battery.
That would put the screws to Apple and their glued together phones and iPods. :)
Have you ever actually looked at what is glued in a 5C?
The battery and one flex cable. Both easy to remove.
You make it sound like they flood the phone with superglue after assembly.
The iBook g4 and the g4 Powerbook indeed were nightmares to take apart. But A. it was a challenge and B. it had to be done.
I also had to pry open some glued stuff, but in the end it always worked fine. If anything it makes working on those machines a task I don’t rush, resulting in lessen (dis)assembly mistakes.
And seriously, whining about how “something is hard to open” on a hack forum? Poor form.
Great idea… Except all my old devices with removable dead batteries are either impossible or stupidly expensive to replace the batteries. Which is ok, because frankly, they’re not worth using any more, because technology has moved on.
Wow. Took em long enough. Those last coupla pins can be tricky ;P
So…I googled the magic IC with filetype:pdf and an iphone 5 schematic PDF came up….that might have some interesting info for hacking stuff….like “12C ADDRESS: 0011010X” written above that IC (I guess that would be I2C addr, as this chip does have an I2C line)….
Matt Galisa’s page is down. Here is a wayback snap shot https://web.archive.org/web/20130429034218/http://www.mgalisa.com/?p=91
Michael
I’m making a wireless charging iPhone case product with a lightning connector. I need a way to test each unit off the production line. So I need a lightning receptacle that has a black and a red power wire so the tester can put a load on the case for test. Is that a subset of this hack? Anyone know how to do that?